SophosLabs just pointed out to us a new piece of ransomware with an interesting twist.
It’s a virus!
Most malware samples these days are what’s known as Trojans, short for “Trojan Horses” – programs that seem harmless on the surface, but have nasty surprises hidden inside.
Trojans don’t get around by themselves – they have to be delivered somehow, typically by email or via a booby-trapped web page.
Twenty years ago, however, most malware samples were viruses, meaning that they were programmed to spread on their own, like a viral infection, typically by copying themselves to other files or directories they could find, including on your network, if you had one, and to removable storage devices (or “floppy disks,” as they were known in the 1990s).
Self-spreading malware has one important advantage for the crooks: they don’t have to keep on spamming out attachments or dangerous links, because viruses get a life of their own once they’re out and about.
As a result, viruses may well spread further and last longer, not least because infections inside an organisation that aren’t stamped out completely may keep reappearing, sometimes for years.
Of course, the act of self-spreading is one more way for malware to draw attention to itself, so in today’s always-connected world, it’s a technique that’s not seen much any more.
Viral ransomware
Nevertheless, self-spreading ransowmare has been tried by cybercriminals before.
Presumably, their hope was that multiple infections inside a business, or on a home network, would therefore be more likely.
Most ransomware generates a unique encryption key for each computer it attacks, so there’s no shortcut if several computers inside your company get hit: you need to buy a unique unlock code for each one of them.
Moving around inside your network seems to be the aim of this new ransomware sample, detected and blocked by Sophos products as Troj/Agent-ARXC and Troj/Mdrop-HGD.
The good news is that we haven’t seen much evidence of it in the wild, so it doesn’t seem to be spreading very effectively, despite being a virus.
Like a lot of ransomware, we’ve seen this one “promoted” via email, claiming (admittedly rather unconvincingly) to come from a public service department in California:
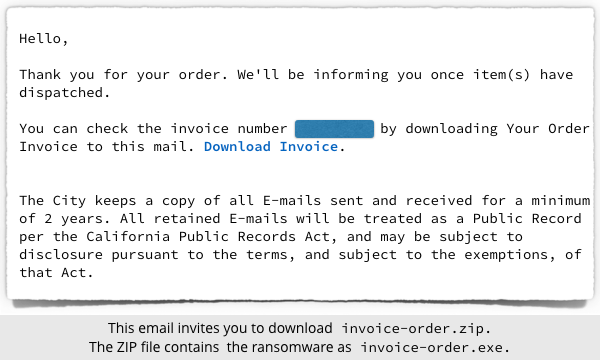
If you allow yourself to be talked into downloading the alleged invoice, you’ll receive a file called invoice-order.zip; opening it up will reveal the malware in a file invoice-order.exe.
If you open up the invoice-order.exe file, the ransomware runs, scrambling any files it can find with extensions from a lengthy list, including archives, images, videos, documents, spreadsheets and even programming projects.
The ransomware then displays its “pay page,” making sure you know how to buy back the decryption key to unscramble your data:
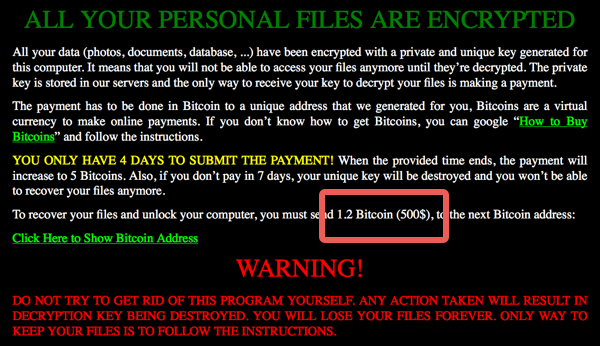
Bitcoins have surged a bit in value over the past few days since this malware appeared, so the bill you’ll face (BTC1.2) is more like $640 at the time of writing [2016-06-01T17:00Z].
As well as scrambling your precious files, this ransomware also makes copies of itself onto writable network shares and removable drives it finds, presumably hoping that someone else might open the infected file later on.
The dropped file is called zcrypt.lnk, and it is accompanied by an autorun.inf that attempts to load it automatically when a user inserts the infected device or browses to an infected network share.
This is something of a blast from the past, because “Autorun” on removable drives has been turned off by default on Windows computers for years, so the risk of unexpected infection this way can be considered low.
Nevertheless, if you’re a system administrator, it’s worth checking that AutoRun really is turned off on all your computers. (You can do this using Group Policy.)
The malware also adds itself to the AppData\Roaming directory, which is automatically replicated onto other computers you use on the same network, meaning that this virus can literally follow you around.
What to do?
We don’t expect you to be affected by this one, because we think it’s rather obviously suspicious.
Nevertheless, all our usual suggestions will help you against this and other malware threats:
- Use a web filter to block untrustworthy links.
- Use an email filter to block untrustworthy messages.
- Apply common sense when faced with invoices and other messages you weren’t expecting.
- Don’t open .ZIP files or run .EXE files from unknown sources.
- Use Group Policy to make sure AutoRun is turned off everywhere.
- Make regular backups, including keeping off-site copies.
Importantly, please remember that not all ransomware is made alike.
In particular, viral ransomware of the Zcrypt sort doesn’t work on a one-email-one-sample-one-potential-victim model.
In other words, after you’ve had one infection, other victims may later get infected too, even though they never received a malicious email, or clicked a malicious link, or downloaded a malicious file.
Even after a single report of this malware, consider doing an on-demand or overnight virus scan of your file servers to make sure that it hasn’t left copies of itself lying around, hoping to snare additional victims later on.
Benzo
Hmm I mean self propelled ransomeware would rake in more money….makes sense
kingofgng
Well, this seems more of a worm to me than a virus to me. The last time I checked viruses were parasites, not self-sustained EXEs :-P
Paul Ducklin
All worms are viruses. Not all viruses are worms.
(Think of a worm as a virus that infects a zero-byte host file.)
That leaves the word “virus” with the more general and commonly used meaning of “spreads by itself” it has long had.
Aelon Rhiadra
It is also possible to stop programs running from the appdata folder via group policy get we have this in place on our network.
Paul Ducklin
Good advice.
M. Wright
In layman’s language, how does one use group policy to make sure AutoRun is turned off everywhere?
Thanks for the posts. They’re interesting and quite helpful.
Paul Ducklin
No promises, but I found this on Microsoft’s support pages:
– – –
1. Click Start, type Gpedit.msc in the Start Search box, and then press ENTER.
If you are prompted for an administrator password or for confirmation, type the password, or click Allow.
2. Under Computer Configuration, expand Administrative Templates, expand Windows Components, and then click Autoplay Policies.
3. In the Details pane, double-click Turn off Autoplay.
– – –
M. Wright
Thank you. The more I learn about PCs, the less I realize I know.
Dan
Please be advised, that Group Policy may not be available on Windows Operating Systems where the business platform isn’t the intended use such as the Home or non-Professional versions available.
Paul Ducklin
You can nevertheless edit the registry directly to achieve the results that a Group Policy Object would…take a search around Microsoftland for what to do and where.
Gerardo Contreras
Well… Sophos itself used to make a precise difference between virus and worm, leaving “virus” for the kind of programs which replicate themselves to reachable files, and yes, stay like parasites on them. Worms, on the other side, was the name Sophos used to give to programs which are able to copy as a self sustained program on the network.
It seems recently Sophos adopted the specific definition “Parasitic virus” to make “Virus” something more general.
Paul Ducklin
I don’t think that’s true. (At least, in all my years at Sophos I have resolutely – pedantically, some might say, but that is an insignificant detail – declared that worms form a proper subset of viruses, and I’m sticking to that now. If you consider worms and viruses disjoint sets then you have the annoying problem that there is no convenient, meaningfully-metaphorical term for “virus-and-worms-considered-together.”)
As an aside, I don’t recall Sophos ever using “worm” to define *network* spreading malware, because there are many worms that spread via other means, such as removable drives. Stuxnet springs to mind.
As to this article…I think you know what I meant when I said, “It’s a virus,” so I don’t think I’ve misled anyone there. OTOH, I think I’ll edit the bit where I imply that many viruses deliberately spread via your network. Most viruses looked for other files to infect, including on the network, but they could spread just fine without a network.
Laurence Marks
The grammar and syntax aren’t too bad, although “dispatched” is more British than American–we Yanks say “sent.” And the second paragraph isn’t well-formed.
But the concept isn’t very credible. US municipalities don’t usually take orders for merchandise, nor do they usually sell it. No one should fall for it.
Paul Adams
More and more people seem to want to use “dispatched” for “sent”, but to dispatch means to kill.
Despatch means send
Paul Ducklin
My American English dictionary (it’s a good one) disagrees with you, and so do I. “Despatch” is merely an alternative spelling for “dispatch.” They’re the same word, meaning “to send off for a purpose,” with a secondary meaning of “to get rid of a problem” and thus, metaphorically, “to kill.” (Compare jewelry/jewellery, or tire/tyre.)