As you probably know, a lot of ransomware arrives by means of believable-looking Word documents.
You receive an email that looks just like a customer requesting a quote, or an invoice that you need to pay, or a courier delivery that went astray.
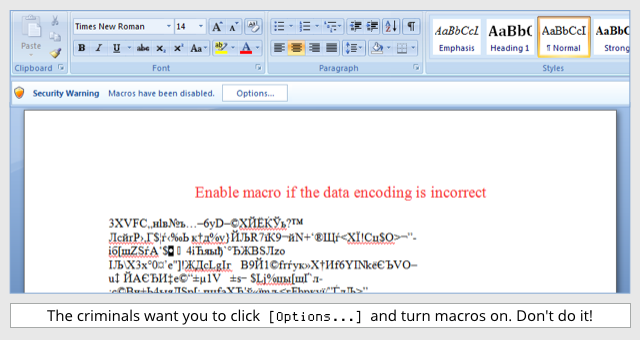
You’re supposed to consult the attached document for details…
…but when you do, there’s some problem viewing it, but you can fix that…
…if only you click the [Options] button and enable macros.
The problem is that a macro is essentially a miniature program embedded inside the document, and it can do almost anything that a regular program can do, such as connecting to a web server, downloading some software, and running it.
In other words, an email telling you to enable macros in a document is as dangerous as an email telling you, “Please download and install this unusual version of NOTEPAD.EXE, ignoring all security warnings, to read this email properly.”
Macros don’t run by default, for security reasons, but an outright block on macros can get in the way, because many legitimate Word and Excel files use macros for perfectly unexceptionable purposes, such as helping you fill in forms or perform complex calculations.
That means that in most businesses, users can enable macros if they think they need to – so that just one bad judgement call could let ransomware, or any other malware, into the organisation.
Microsoft has therefore added a new policy option into Office 2016 that allows finer control over documents with macros.
You can now limit the functionality of the macro programming system so that even if users normally have the chance to enable macros, they can’t if the macros came in an Office file from the internet.
The option is well-named: Block macros from running in Office files from the internet.
Is this end of ransomware?
Sadly, the answer is,”No.”
Malware, including ransomware, can arrive in many other ways.
Instead of using attachments containing Word macro downloaders, crooks can use numerous other infection techniques.
A common trick is to send a .js attachment (JavaScript) instead of a .doc file; scripts written in JavaScript have much the same powers as those written as Office macros, and protection based on controlling macros won’t help in this case.
And crooks can also use booby-trapped documents that work by exploiting bugs in Word itself, so that no macros are needed at all.
Lastly, there’s still plenty of malware that get in without using email, thanks to USB flash devices, malvertising, and booby-trapped websites.
Nevertheless, if you are using Office 2016, this new anti-untrusted-macro execution protection is well worth using.
Image of keep out sign courtesy of Shutterstock.

Craig Charles
There’s also a few cases where the attachment comes with a fake extension, like image001.jpg.exe inside the ZIP. Guess if you have show extensions turned off it would only the icon that appeared wrong.