Thanks to the Emerging Threats Team at SophosLabs for their behind-the-scenes work on this article.
“Locky” feels like quite a cheery-sounding name.
But it’s also the nickname of a new strain of ransomware, so-called because it renames all your important files so that they have the extension .locky.
Of course, it doesn’t just rename your files, it scrambles them first, and – as you probably know about ransomware – only the crooks have the decryption key.
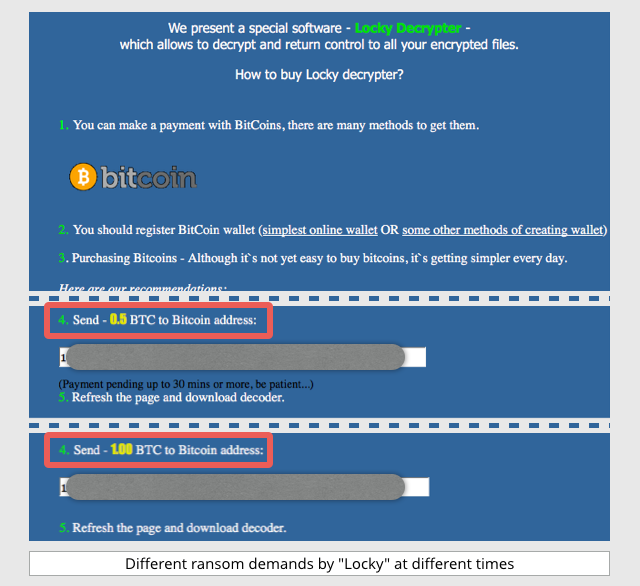
You can buy the decryption key from the crooks via the so-called dark web.
The prices we’ve seen vary from BTC 0.5 to BTC 1.00 (BTC is short for “bitcoin,” where one bitcoin is currently worth about $400/£280).
The most common way that Locky arrives is as follows:
- You receive an email containing an attached document (Troj/DocDl-BCF).
- The document looks like gobbledegook.
- The document advises you to enable macros “if the data encoding is incorrect.”
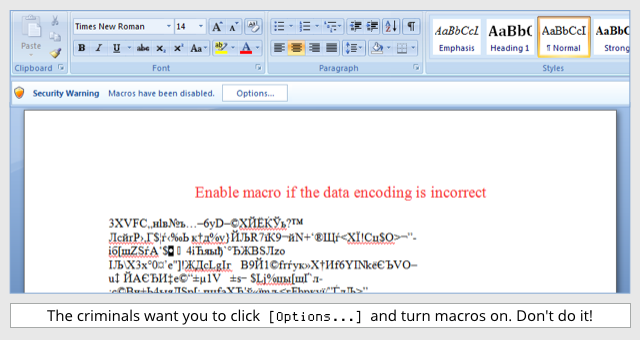
- If you enable macros, you don’t actually correct the text encoding (that’s a subterfuge); instead, you run code inside the document that saves a file to disk and runs it.
- The saved file (Troj/Ransom-CGX) serves as a downloader, which fetches the final malware payload from the crooks.
- The final payload could be anything, but in this case is usually the Locky Ransomware (Troj/Ransom-CGW).
Locky scrambles all files that match a long list of extensions, including videos, images, source code, and Office files.
Locky even scrambles wallet.dat, your Bitcoin wallet file, if you have one.
In other words, if you have more BTCs in your wallet than the cost of the ransom, and no backup, you are very likely to pay up. (And you’ll already know how to buy new bitcoins, and how to pay with them.)
Locky also removes any Volume Snapshot Service (VSS) files, also known as shadow copies, that you may have made.
Shadow copies are the Windows way of making live backup snapshots without having to stop working – you don’t need to logout or even close your applications first – so they are a quick and popular alternative to a proper backup procedure.
Once Locky is ready to hit you up for the ransom, it makes sure you see the following message by changing your desktop wallpaper:
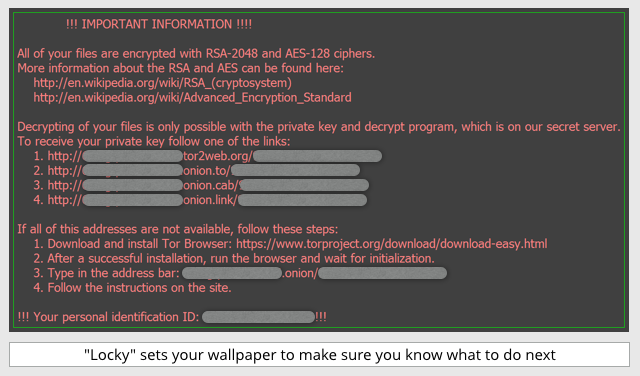
If you visit the dark web page given in the warning message, then you receive the instructions for payment that we showed above.
Unfortunately, so far as we can tell, there are no easy shortcuts to get your data back if you don’t have a recent backup.
Remember, also, that like most ransomware, Locky doesn’t just scramble your C: drive.
It scrambles any files in any directory on any mounted drive that it can access, including removable drives that are plugged in at the time, or network shares that are accessible, including servers and other people’s computers, whether they are running Windows, OS X or Linux.
If you are logged in as a domain administrator and you get hit by ransomware, you could do very widespread damage indeed.
Giving yourself up front all the login power you might ever need is very convenient, but please don’t do it.
Only login (or use Run As...) with admin powers when you really need them, and relinquish those powers as soon as you don’t.
WHAT TO DO?
- Backup regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Don’t enable macros in document attachments received via email. Microsoft deliberately turned off auto-execution of macros by default many years ago as a security measure. A lot of malware infections rely on persuading you to turn macros back on, so don’t do it!
- Be cautious about unsolicited attachments. The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
- Don’t give yourself more login power than you need. Most importantly, don’t stay logged in as an administrator any longer than is strictly necessary, and avoid browsing, opening documents or other “regular work” activities while you have administrator rights.
- Consider installing the Microsoft Office viewers. These viewer applications let you see what documents look like without opening them in Word or Excel itself. In particular, the viewer software doesn’t support macros at all, so you can’t enable macros by mistake!
- Patch early, patch often. Malware that doesn’t come in via document macros often relies on security bugs in popular applications, including Office, your browser, Flash and more. The sooner you patch, the fewer open holes remain for the crooks to exploit.

justiceISfake
Just had a client get this 2 days ago… she was running as admin for her daily user… locky went crazy. Locky sucks :(
The version she got demanded $500 even not BTC.
lemonblogger
Our company was hit with this one on Monday. Unfortunately, we use older software that requires macros for document merging, leaving us vulnerable to this type of attack. One of my users received an attachment and opened it, apparently. We caught it less than an hour after it starting doing it’s work, but the damage was done, over 20,000 files encrypted. It searches mapped drives and searched the network for open Shared Folders (not mapped). We were able to restore everything from backups, which, besides prevention, is the only defense. I even created a Group Policy to stop older ransomware (Cryptolocker) that prevents anything executing from C:\Users\USERNAME\AppData\, but it didn’t stop this one. This creates a file in C:\Users\USERNAME\AppData\Local\Temp\RANDOMSTRING.tmp and puts registry entries to execute this file at startup. There was another registry entry on the system in BINARY that I assume helps this file.
Mahhn
Thank you for sharing the information!
Hope the recovery went well.
Mike
Had this one last night…
justiceISfake
just curious if you had any luck outside of paying them… i did not.
Mike
In our case it didn’t extend to the network, the damage was only done in the local computer. I decided to accept the loss.
khaled
is there any solution for this issue ??
roberrt gray
the viewer app you recommend are ancient and may not even run under Win10
Matthew
Seen a similar variant recently called .lechiffre. If it can gain admin privileges, it will run a vssadmin delete shadows command like others of this type.
Always a good idea to review and test backups!
Anonymous
“Run as” sucks as the application will save data in the profile of the user you are running as.
Anonymous
Please update if any of you have got a solution. A few of our users have also been affected. They do not have admin priveleges on their user, yet they are affected.
Will
Not having admin rights just means the sphere of influence that Locky has is smaller, but it doesn’t mean that it couldn’t encrypt their personal files, or change their desktop background.
Unfortunately it’s likely that the only recovery from ransomware encrypted content is restoring from a backup.
Chris
Does it pro-actively scan the lan for open smb/samba shares, or just encrypt shares the user already has mapped?
Does this need to contact a c2 to grab the encryption key before it can encrypt files, or is it completely self contained?
Paul Ducklin
A1. Not sure if it sticks to already-mapped drives or not. Will check and let you know.
A1. The former. It calls home first, and doesn’t start the scrambling until a reply comes back with the public key. In other words, if you block access to its backend server, you can avoid disaster. (Sophos Web Appliance, for example, will do that.)
Dave B.
It goes after ANY share, mapped or not.
Brockin
See Lemonbloggers comment above. It scans open shares as well as mapped drives. (our NAS was not mapped on one pc that was infected, yet it was encrypted)
JChris
What is the simplest/best way to explain to clients, friends, family, how to NOT use an administrator login for general use (especially if they have been unknowingly doing it forever)? Should they be advised to make their current user/login a general user, then keep an administrator username/password nearby, so they can do administrator tasks, when needed? Curious how others have (successfully) explained this to others. Thanks!
Paul Ducklin
Imagine that you have a safe at home for your valuables. You trust yourself, right? So why not leave the safe unlocked whenever you’re at home? If you need to get things out of it, you won’t have to mess around unlocking it, perhaps a few times a day. And from there it’s an easy jump to say, “Should I go and lock the safe now? I’m only nipping out to the shops, I’ll leave it.” Or, “We’ve got visitors, but it’ll be OK. I’ll keep my eye on it most of the time. No need to lock it.”
Niall Mullen (@Phweakazoid)
Teach them about Windows UAC feature. If used correctly a daily user need not have admin rights.
ray
that doesnt help. I have a user on my network with no admin rights at all. The my server was infected still. Just today.
Paul
… I have encountered trojans which DO NOT require admin rights – as they come with their own due to bugs in the M$ coding . One such – within seconds, both hard drives lost ALL access privileges to open files, create folders, etc.; yet to re-enable took more than a half day, for each drive, just to get back most controls, leaving the particular scanner running with out interruption … then had to clean ot the rest of the junk
So don’t be complacent about raised admin rights or not as MOST of these gremlins apply their own admin controls once they get in.
I have just seen on a local business the effects of Locky, and it aint pretty the trail of mayhem which it inflicts. Unfortunately they didn’t have any recent document backups, and the shadow files were only 10% legible. This one came in through an email requesting confirmation of an invoice … … … and due to a large client base new and existing, just instinctively opened it …
Paul Ducklin
It’s still a good idea not to give every user (or yourself) admin rights all the time for day-to-day work.
Some malware is able to “pronote” itself to admin, for example using an elevation of privilege vulnerability, but most malware is not. (And you can reduce the risk of elevation of privilege hiles being avaialbale by patching promptly, too.)
aroundmeridian
If you have used a credit card with a computer that is now infected, would you recommend cancelling that card?
Paul Ducklin
Tough one! Problem is that quite a few ransomware infections are caused by crooks using *existing* malware you didn’t even realise you had as a bckdoor for installation. (Loosely speaking, Crook A with new malware X pays Crook B, with botnet Y, on a “pay per install” basis to deliver the victims an “upgrade” to the new malware.)
If it’s not a huge inconvenience…my gut feeling is, clean the computer, make sure nothing bad is left behind, start afresh with a new card.
Anonymous
any updates?
ikkegoemikke
We were attacked tuesday by this ransomware. 150 Emails spoofed to our mailserver. 149 Mails were blocked by the Barracuda spamfilter. One slipped through and was initialised by a coworker from the saledepartment. In half an hour our fileserver, applicationserver and shared maps on local PC’s was encrypted.
After locating the PC where it all started, we took that one from the network and started to restore everything from the backup. In one hour the fileserver and applicationserver was back working.
Except one local folder with lots of data in that wasn’t on the fileserver was completely destroyed. We succeeded in fixing this as follows.
First we installed RECUVA on this PC and tried to recover the lost map.The fact that the user kept working on it, had as result that most files were’nt recoverable because they were overwritten by cookies and temporary internetfiles. (So when noticing the LOCKY files … stop working)
Windows 7 has shadow files. Too bad those files are corrupt because of the LOCKY virus … but … we were able to recover those files with RECUVA, restore them and start SHADOWEXPLORER and go back 6 days to recover a shadowcopy from the lost data folder. In the end we recovered about 99% of lost files !
But as someone said before …. nothing helps to prevent it so backup, backup and backup …..
john meyer
Hello Paul
Do you have recommandation for an hips tool for private use
regards john
Paul Ducklin
You could look at the Hitman Pro tools from SurfRight:
http://www.surfright.nl/
(Declaration of interest: SurfRight is owned by Sophos.)
Laurence Marks
I’m curious to know what steps the AV providers are taking to heuristically detect that the encryption is taking place (e.g., lots of files in the same directory being re-written and re-named in a short period) and killing the malware. Many users wouldn’t need to pay if they’d only lost a dozen files or so, making this kind of extortion less profitable.
Naked Security has been surprisingly silent on this.
Paul Ducklin
There are security products that try to do this. You have to be careful, though, because in a business environment, if you are overly generic you may end up “recognising” behaviour that was intended (such as updating a directory of locally-stored files with more recent version off a server) and killing off a process that’s supposed to run on every computer, blocking an important part of your organisational workflow, and generating a sea of false alarms.
S J Morgan
My company got Locky’d on Wednesday, thankfully only 2 machines were logged onto the network at the time, while looking at the machine that downloaded the infected word doc, (5 minutes after this thing started encrypting) I saw a white icon drop on the desktop, at that point I ran to the comm room and unplugged the LAN network switch. at that exact moment the anti virus on both machines alerted to a threat. I then went to machine 1 and opened the mystery white icon which was the Locky ransom note, (Locky didn’t run to completion, ‘Desktop background didn’t change to the ransom note photo’) thus I had 1 shadow volume copy from Monday, then I ran multiple AV programs on both machines making sure there was no Locky left. did a system restore on machine 1 to the Monday restore point. didn’t work, cussed a bit, then sent samples of encrypted files and copy of ransom note to Kaspersky for analysis.
Today I was at machine 1, and just for fun, on a folder full of photos, right clicked and selected ‘Restore previous versions’ and referenced Mondays shadow volume copy, and IT WORKED!!! the photos were restored, Locky encrypted files remained, (will be deleted later)
a bit time consuming, but I’m now doing multiple folders and files, and so far seems to work, so if Locky didn’t delete all your shadow volume copies, this method should work for you.
Anonymous
Hi my PC was infected on Friday. All files encrypted. Laptop is now in a shop with the boffins but if anyone knows or have heard that files can be recovered please let me know. Unfortunately my PC wasn’t backed up.
Thank you
Lee
Glenn Simpson
I note that stopping the Malware from “phoning home” stops it from encrypting, does anybody know if it is proxy aware? By default none of our clients have direct access, and this practice has saved us in the past from Cryptolocker but if they have figured that out it is one less line of defence.
Medix
Any info as to what versions of Windows Locky can run under? Does Locky run on any non-Windows OS?
Paul Ducklin
Windows only.
There are some Linux ransomware examples, but so far they haven’t been well-enough written or organised to pose a serious threat:
https://nakedsecurity.sophos.com/2015/11/11/ransomware-meets-linux-on-the-command-line/
Note, however, that users of non-Windows computers can be *affected* by Windows ransomware…for example, if they’ve shared files on their computer over the network, and someone else who has write access to their shared stuff gets infected.
Anonymous
Does this affect Win10 with secure boot set up?
Paul Ducklin
Yes. The ransomware runs as a regular program inside Windows, with the same access rights as you, so it can read and write (and thus scramble) any files that you can access. Secure boot is a long way in the past by the time this happens.
mike
I have a question. Is there a possibility to extract somehow the key that is required to encrypt the files? I mean let’s say i have a sandbox laptop that i can sacrifice, and i have e-mail with this virus. I create a common xls file, backup it and then i run the virus. Having both files before and after infection doesn’t give any chance to extract the difference which would be the key? Maybe it is stupid what i just say, and if so i’ll be appreciated if you explain me that it is :)
Paul Ducklin
Unfortunately, this won’t work. There’s a different, random key for encrypting each file, so even two copies of the same file will end up looking different. Even if you deliberately infect two cloned VMs, the end result of the scrambling will be totally different on each computer.
Also, the random keys for each file are then encrypted with a public key that comes from the server run by the crooks. There’s a different public key for each infected computer. So you can’t buy one decryption key and share it with anyone else.
jacques
how do i get rid off locky??
Paul Ducklin
If it has scrambled your files, and you dont have any backup, and you aren’t prepared to do a deal with the crooks…
…I am afraid you will pretty much have to start over. An anti-virus (like Sophos Home or the Sophos Removal Tool) can get rid of the malware that’s left behind, but it can’t repair your files.
Anonymouse
What if it hasn’t scrambled my files but is simply refusing to be deleted from my registry?
I encrypted my machine with VeraCrypt several months ago but even before encrypting my system, I already had BitDefender’s Anti-Ransomware tool installed and running, so I’m assuming this may what is currently thwarting the Locky bug that hit my machine. I use several Anti-Malware programs, including Malwarebytes, but the only one that caught this thing was GridinSoft’s Anti-Malware (Formerly ‘Trojan-Killer’).
I deleted all the ‘Locky’ registry entries found while in Safe Mode, after running rkill, but when I reboot, the files still remain. I can delete the files even in normal mode but they still re-appear in the registry after subsequent reboots.
Throughout my many attempts to delete these files even using Malwarebytes ‘RegAssassin’ tool, it appears that some of them are no longer present on my system, however several Locky entries still remain.
Does anyone have any removal scripts I could try with Emsisofts BlitzBlank that might work?
Please note: I’m not looking to decrypt anything because my system hasn’t been taken over. I simply found these files in my registry recently and now just need to remove them though they continue to persist.
Paul Ducklin
You seem to be saying that one product identified the malware, but couldn’t clean it; that another product can block the malware from encrypting your data, but can’t identify it; and that a third product can’t identify it but can clean part of it.
Do you have the malware but it’s inactive because one of the products killed it? Do you have the malware and it’s active but inhibited from activating because one of the products is getting in its way? Do you have some harmless left-over parts of the malware after one of the products cleaned it? Is one product adding some “decoy” registry data to try to trick any future attacks by this malware, whereupon the other products point out that something suspicious happened?
You probably need to ask for technical support from one or more of the products you’ve got installed (be sure to tell each vendor that you’ve got the other products installed, how they’re configured and what they’ve reported so far) …give them a fair chance to try to figure out what’s going on.
jon
will a system restore outside of windows help?
Paul Ducklin
I’m not an expert on Windows System Restore, but AFAIK it is specifically intended to restore your *system* files and leave your data untouched (in case you break the OS itself).
dwscott
Really curious; if a user is not an administrator and User Account Control is turned up, will the executable run without a notification?
Paul Ducklin
I haven’t tried all the combinations myself, but remember that the malware only need to run as you to scramble *your* files. If you’re an admin, you can do a lot more damage to your own computer and to others on the network…
…but malware doesn’t need high privilege to ruin your data :-(
dwscott
Thanks, Paul. I understand that my files are toast if it runs in my context. I’m just looking for more warning signs, like that (sometimes annoying) popup that says “Wait! You’re about to execute a file!” because of UAC.
I certainly don’t want to test the malware myself to find out ;)
Thanks!
Vickie
Has anyone paid the ransom and did it work? I have no recent backup. I’ve never used BTC. My ransom say’s they want 3.00 BTC. They way I figure it its a lot more then $500.00
Dan
We have a customer that has just been hit by this virus. It was opened via email on the terminal server and has encrypted files on the file server. Does this mean both servers are infected and need to be cleaned or just the terminal server where it was executed?
Thanks…
Paul Ducklin
It depends…one server could be *infected* and that could *affect* both servers (the malware will encrypt anywhere it has write access, including network and removable drives, not merely the C: drive). Or they could both have the malware on them. You could try scanning them with this:
https://www.sophos.com/en-us/products/free-tools/virus-removal-tool.aspx
John F Ryan
I had a computer infected yesterday. Windows Defender “full scan” found the malware and removed it.
Blocky
Thanx for your good job here, Paul !!!
The best way would be if someone traces and shuts down the IP addresses
of these gangsters but we can add them to the HOSTS file, so Locky can’t become “alive”.
127.0.0.1 31.41.47.37 #[Locky – Ransomware]
127.0.0.1 188.138.88.184 #[Locky – Ransomware]
127.0.0.1 85.25.138.187 #[Locky – Ransomware]
Warning: Some new Locky version might use other IPs.
And:
The files inside the Windows folder remain untouched from Locky
so a backup of the personal important data should be stored somewhere there!
Paul Ducklin
Some remarks, if I may. If you add IP numbers to your HOSTS file as a way of deliberately diverting traffic, keep reminding yourself that “this is for emergency purposes only”. If you try to do this as a primary anti-malware trick, you will have 100s of 1000s of entries in there within about a week, which is inefficient and unmanageable – and it only work for malware, including ranswomare, that calls home before it does bad things, rather than after. Also, backing up files in the Windows folder isn’t such a good idea: it’s defeating the idea of keeping the OS files and your personal data apart, and it still leaves the files actively in harm’s way. Repeat after me: “Offline, and if possible off-site.”
In short: by all means go for malware-specific “immunisations”, but never allow yourself to think that you’ve done anything of general protective value :-)
(We saw this back in the days of the infamous Melissa virus. If you had an invalid email address in your address book, the virus would crash at that point and stop spamming itself out, so lots of people added a dodgy email at the very top of the list, “0000fake,” or something. This was a handy and specifically anti-Melissa hack, but it ended up entrenched for many years in popular wisdom as a general-purpose protection technique that was, in fact, useless – the virus writers just fixed the bug in Melissa and carried on.)
cat
this one is from today, one of the employees here received an email from her own account as she said, with a zip file, proceded to open it and voila! all files went with extension locky and infected the server
Jean-Yves Hemlin
She must have executed something else as zip files don’t DO anything.
Zip files are like Words document. They can not do anything unless you give them special authorization.
Dvn
Pulled the harddrive out and used ShadowExplorer to get the earlier copies of the documents that were having the .locky extension. All the documents are now fully functioning and the computer was then formatted.
BB
My PC might be infected by Locky but I am not sure. The zip file was opened less than 2 days ago. For the moment, I haven’t seen any change in th extension of my files (still .docx, .jpg, .mp3 files) and no ransom.
I bought a portable hard drive to make a backup (to not mix them with my previous backups)
Is there any possibility to check if those dates are affected ?
I will reset my computer tomorrow with an IT service. Will I be able to use those datas again ?
Thanks
Paul Ducklin
if the file extensions haven’t changed and the files can still be opened, it sounds as though you are OK. So back up right now and will have something to fall back to if the worst happens before you get the computer checked out and cleaned up.
cdoggyd
This form of ransomware hit a local hospital recently. Luckily, they were able to restore systems without paying the ransom.
http://krebsonsecurity.com/2016/03/hospital-declares-internet-state-of-emergency-after-ransomware-infection/
Saskia
I had a battle with ransomware today, but it was called vevzohi. Everything was encrypted and given the .vevzohi extension. Just wanted to let everyone know. Luckily the affected computer started messing with a shared Dropbox folder sending alerts to me. Still got over 16.000 files affected though. Luckily most are backed up and other were recovered with Shadow explorer (works even if the restore to a previous version doesn’t!).
Wish I got figure out a way to prevent programs like this from accessing Dropbox and Google Drive. Any ideas on this would be appreciated!
Jason X Bånd
@Saskia, ransomware doesn’t access Google Drive. It only encrypts on the PC. Google Drive Sync then copies the encrypted version to Google Drive. It’s important to realise that Google Drive maintains previous revisions, so it’s very easy to get rid of the encrypted revision and thus restore the previous version.
Charlie Summners
There is apparently a new variant; this one does _not_ create a desktop BMP, creates text files named “_HELP_instructions.txt” in each affected folder, and (most importantly) cannot be found by the Sophos Virus Removal Tool (at least as of this date). Malwarebytes _did_ remove the executables, but of course the damage to the user area and in this case a medical office’s external fax cache was already done.
Vector was apparently a ZIP file attached to an email that was accidentally clicked. (*sigh*)
CoolPra
Hey Bros, to get rid of this ransomeware, there are only two solutions….
1. Pay the ransome to them to recover your data. (I strongly suggest DO NOT PAY and encourage these A## Ho##s….!!!!)
2. REGULAR BACKUP!!!BACKUP!!!BACKUP!!!…Always backup your data (disconnect from Internet/ Network before backup)…Keep the BACKUP DATA OFFLINE!!!!!
Do not rely on System Restore since this “CRAZY” delete the “Shadow Copies” of your System Restore….
Hope this information is good for all of us to prevent any future attack…..
GOD BLESS!!!
ma
hi
we got hit on more than one machine
by one that adds .exe to everything
open the file and it jumps off lets you use that file and encrypts whatever files it can get to
the popup screen takes awhile to pop up and wants a Bitcoin payment
I can’t understand how if you pay to the wallet how you get the unlock key
vivek lahoti
We got infected on 29april 2016 and the very next day we transfered them ranson. Within 2hrs of transfering ransom we got locky decrypter and all our data was back. We never want to send ransom but we had seven computers infected on LAN and all our data was lost, so very important to get that back.
Anonymous
we got hit by locky today. all files are now with .locky extension and unfortunately we dont have any backup. looking forward on using all help provided here step by step. will post updates on what happens.. fingures crossed.
sys
Hi, We lost critical datas two days ago. I’m trying to pay that f*cking ransom but can’t do because the link disappeared… What the heck can I do ? (hw5qrh6fxv2tnaqn)
GradIT
You referenced the site, we got directed to the same one (hw5qrh6…). Considering paying, can I ask how it went for you? did you get the decryption key when you paid?
SAM
Same here, it encrypted my NAS, trying to pay ransom but the site is down :(
Anonymous
It’s idiots like you, with no backup and paying these criminals’ ransom demands which means they keep doing it!!!
Anonymous
Infection today now requesting 4BTC! They are getting greedier!
Peter Crescitelli
I got hit with locky this other day, no option but to pay Ransom. Can anyone confirm here if it works ? Still waiting for BTC to be credited to the account. Hoping the link doesn’t expire.
Branden
We got hit with locky on Friday, by a user that opened a zip file and released it into the wild. Thankfully Trend was able to detect it and stop it from encrypting any files on the network. I spent quite some time scanning and searching our file server for key words related to this virus and the server was clean. Our RDS server on the other hand is toast, and will be restored from or latest backup.
Like others have said, backup regularly and test those backups on a regular basis. Backups can truly save you when something devastating like this happens. Trend in recent versions…I believe 11.0, had added some ransomware detection to their software. So another thing that should be mentioned is, make sure your antivirus is up to date. Along with this, user knowledge is key, train employees to not open any emails and files they are unsure of.
I wish the best to everyone dealing with this ransomeware, as it is truly a pain to deal with.
Anonymous
When has it attacked most recently?
Anonymous
We got hit today. Paid ransom as it has put our multi million dollar firm completely to its knees. Haven’t heard back or received a key and it’s been six hours. Has anyone else paid and what time did they hear back please? Thank you.
Jason
Its now the June 21st. Did you ever get the key after paying ransom? Also was the ransom 5 bitcoins?
Syed Hamzah Mehmood Rufai
I am trying o map and study various internet attacks,
can anyone give me date and time when they were attacked in February 2016.
Shawn Bennett
Just hit us Friday. Took out our file server and APP server. Just blew out the volumes and restored from backup the night before. We were down half a day but it could of been worse. How much is your data worth is always what I ask. People get cheap and dont want to spend money on Technology till they lose it all. Verify you have good backups and you will be ok. If not get a new IT guy.
Wbean
Does anyone know how the virus traverses non-mapped file shares? I’d like to isolate workstations so that if one is infected it can’t spread to the servers.
Puiu Macaveiu
I have a SQL Server with RAID. Every night it is automatically backed up on another drive (same PC). If attach a Synology NAS that saves backups from which are made to himself, without there being any shared folder on the NAS is a safe solution against viruses of this kind?
bittin (@bittin)
Started getting this too the company i work ono sent out an extra WARNING
Behind the mask
Who will that stupid to open suspicious files that from unknown source on the internet.
Everybody knows that encoding could be only changed by the encoding options, not only ms office, it’s same to every word processing software. Never heard of marco scripts could do the magic.
Seems there is a pattern that how the virus spread to every internet end-user,
opening the things or clicking the things on the internet without any awareness is must be the main factor why they are growing furiously.
Sometimes even those files or executions are came from a trusted site, I still prefer give those docs a scan and double confirm that the file is safe and clean. People may say I am too overprotective, but I say a trusted site could be hacked anytime, you’ll never know when will it happens. Stay focus, then there are no worries about watching dirty things on the internet (if you know what I mean).
Bernd Wechner
I think you missed an opportunity under WHAT TO DO? alas which was to state clearly:
NEVER open a .doc or .docx file from an email even if you know the sender. Don’t do it, ever, unless it is a document you know, you know you are collaborating on and need to edit. If someone sends you a Word document to view, respond politely asking them to send you the document as a PDF, the portable document format designed for sharing documents and not in a word processor format designed for working on and editing a document. Spread the word and help your friends learn how to make a PDF and how easy it is, from MS-Word or otherwise.
Paul Ducklin
It’s not quite that easy ;-) Firstly, you have a rule that says “don’t open DOCs in email, ever.” Then you add, “Well, unless you need to, of course.” Such rules are quite hard for users to follow. Secondly, you’re creating the perception that PDFs (or files that seem to be PDFs) are a perfectly safe alternative… but sadly, they aren’t. They too can contain the equivalent of Word macros, so just switching DOCs for PDFs isn’t a magic cure.
Ed
I read Anonymous’ comment that runas “sucks”. I fail to understand a bit why. You can grant temporary permission by using the “runas” tool, which is great. Essentially you give each user a default read-only account, with which they login to Windows and that only has read-only access to your important network shares. Next you create a write-access account for each user, that you will only invoke using runas. Then you create a shortcut to a small batch file that uses runas to fire up MS Word with the write-access account of the user. You can specify that this batch file should run invisibly by tweaking the shortcut a bit. By using the /savecred option of runas you could also make this work without revealing the write-access password to the user. This way MS Word could have write access to your documents, but your user and the ransomware will only have read access. And when a doc arrives in mail, by double clicking it, the user invokes the standard Word application with read access, not the runas version with write access as long as you don’t change file type associations. The only downside I see is that the document history that is shown in Word for the write-access account is different than for the read-access account and printers might have to be added to the write-access account once. But this seems to be a minor issue to me, as this procedure should involve a limited number of commonly used applications like Word and Excel. It’s not perfect because tools could read the Windows Credentials, but for the rest it seems to work pretty well.
R
Paul, I’m giving a talk on cybersecurity basics to fellow physicians. Can I use the image of the “Locky” ransomware in my presentation?
Paul Ducklin
if you don’t mind putting “Image courtesy of nakedsecurity.sophos.com” under it on any relevant slides.
garylarsen
here is my idea for NAS backup, get a timer clock, the ones that turn on lights, (digital is best as it remembers the time if theres a power failure) and plug in a small switch into it, then plug your NAS into that switch. Set the powertimer to power off before people come into work and on after everyone leaves work …or just before Backup software is timed to start. In other words the power switch disconnects your backup NAS from the network during the day without powering off the NAS. this way onsite backups have a chance to survive!.
TJ
Just to say I had a customer who got hit the other week; first time I’d come across this. I ran EaseUS Data Recovery in deep scan mode and got all of her data back. Locky was asking for 2 BTC, almost £2000, which she was willing to pay. We both felt satisfied we’d beaten the criminals. Thanks for the article, pointing people to your site.
Samrat Sen
Tip for the Microsoft Office Viewer was nice. I am going to install it. Then at least my system will remain safe from the office files.