Thanks to Fraser Howard of SophosLabs for his behind-the-scenes work on this article.
What do cybercrooks do over New Year?
Some of them, you probably won’t be surprised to learn, take a vacation, or something resembling one.
At least, that’s what SophosLabs noticed from the crooks behind the notorious Angler exploit kit, activity from which seemed to drop off on New Year’s Eve.
(Or perhaps the rest of the world simply took a break from surfing the internet and concentrated on other things, such as watching the fireworks, first-footing neighbours, or swigging down refreshing beverages, leaving Angler with not much online action upon which to intrude.)
Whatever happened on New Year’s Eve, however, wasn’t the end of Angler, because it was soon back to its 2015 infection levels.
EXPLOIT KITS REVISITED
To explain: an exploit kit is a pre-packaged toolkit of malicious web pages that crooks can buy, license or lease for the purpose of distributing malware.
In other words, if you have some shiny new malware – ransomware, perhaps, or a zombie, or a password stealer – you can use an exploit kit to deliver that malware to unsuspecting victims.
Instead of figuring out how to booby-trap your own web pages so that visitors end up infected, you rely on pre-prepared attack code in an exploit kit to try out a series of known security holes, in the hope that one will succeed.
An exploit kit is usually delivered directly into a potential victim’s browser in the form of convoluted and hard-to-follow JavaScript, and automatically tries out a series of attacks, typically in the most likely sequence, until one of them works, or they’ve all failed, something like this:
if java installed then try java exploit 1 if exploit worked then install malware end end if silverlight installed then try silverlight exploit 1 if exploit worked then install malware end try silverlight exploit 2 if exploit worked then install malware end end if flash is installed then ... end if nothing worked then give up end
The same exploit kit can be used to deliver multiple different malware samples; and the same malware sample can be delivered by one or more different exploit kits.
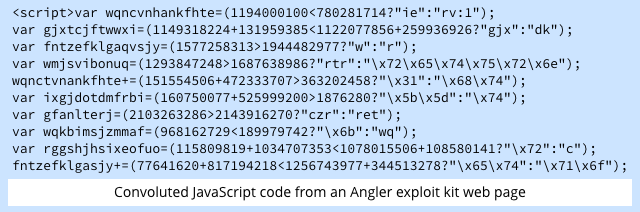
CRIMEWARE-AS-A-SERVICE
Thanks to exploit kits, malware authors don’t need to worry about how to find bugs in Java, or Silverlight, or Flash; how to build those bugs into working exploits; how to find insecure web servers to host the exploits; or how to entice prospective victims to the booby-trapped web pages.
Likewise, the exploit kit authors don’t have to worry about writing full-blown malware; they don’t have to run servers to keep track of infected computers, or to collect money from individual victims; they don’t have to get involved in exfiltrating stolen data, or selling that data on, and so forth.
Each group specialises in one or more parts of the threat landscape, in what’s become known, satirically, as CaaS, or Crimeware-as-a-Service.
Interestingly, even though an exploit kit can in theory be used to deliver almost any sort of malware (indeed, the crooks can choose which malware to implant at runtime if they want), SophosLabs has found that so far in 2016, Angler’s biggest partners in crime are…
…the guys behind the CryptoWall ransomware.
CRYPTOWALL REVISITED
If you’ve been reading Naked Security lately, you’ll know that CryptoWall 4.0 is latest version of this ransomware family.
Version 4 is very similar to earlier versions, inasmuch as it scrambles all your files using a cryptographic key that is known only to the crooks, whereupon the malware offers to sell you the key for a few hundred dollars.
If you don’t have a decent backup, and you want to recover your data, you don’t have much choice but to pay up.
The CryptoWall crooks, for better or for worse, have established a reputation for what counts as honesty amongst rogues. If you pay, you almost certainly will receive your key, and you almost certainly will get your data back. Unfortunately, each key is unique to a single infection, so you can’t join forces with other victims to share the cost. Each victim stands or falls alone.
But there are some curious differences in CryptoWall 4.0, too, notably that it doesn’t just scramble your files and then wait for you to open one of them and receive an error.
CryptoWall 4.0 is much more in-your-face than previous versions, scrambling your filenames as well as their contents, to make the extent of its damage much more immediately obvious:
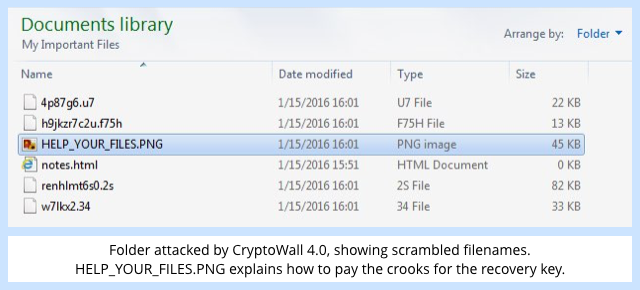
WHAT TO DO?
To boost your defences against exploit kits:
- Patch early, patch often. If you have already closed the holes that an exploit kit is programmed to try, all its alternatives will fail and the exploit kit will be useless.
- Remove unused browser plugins. If you don’t need Java (or Silverlight, or Flash) in your browser, uninstall the plugin. An exploit kit can’t attack a browser component that isn’t there.
- Use an active anti-virus and web filter. Good virus detection tools will block the whole exploit kit if even one its components (or associated web pages) is suspected.
To boost your defences against ransomware, try all of the above, plus:
- Make regular backups, and keep a copy offsite. If you encrypt your backups, then you can store them at a friend’s house (and vice versa) without each of you worrying about what happens if the other’s home gets burgled.
- Use administrative accounts only when necessary, not all the time. Most ransomware will scramble any file to which it has write access, even if it’s on a removable device or a network drive.
SOPHOS PRODUCTS DETECT AND BLOCK THIS MALWARE AS FOLLOWS:
• Angler exploit kit delivery pages: Mal/Redir-AE
• CryptoWall 4.0 ransomware: HPMal/Ransom-(I,R)
💡 LEARN MORE: The Angler exploit kit explained ►
💡 LEARN MORE: The CryptoWall 4.0 ransomware strain ►
💡 LEARN MORE: Ranwomare – should you pay? ►
Image of Angler fish courtesy of Shutterstock.

James
Remove unused browser plugins … Silverlight
And then, the Microsoft updater won’t take no for an answer, so we have to hide the Silverlight installation item around six or seven times. Yay for Microsoft security.
Laurence Marks
Ever notice that, in the new Naked Security format, the Previous and Next links are reversed from the order in the daily email?
For example, suppose I receive an email with the following articles (which conveniently happen to be arranged alphabetically)
–Apple bug fixed…
–Beta Facebook Tor access announced…
–Cross-Site scripting explained..
As a normal reader, assume I read the email from top down, linking out to the Apple article, the Beta article, and the Cross-Site article in succession.
Now suppose I have the Beta article open. At the bottom will be the following:
Previous: Cross-Site scripting explained Next: Apple bug fixed
This is opposite of the order in the email.
Paul Ducklin
The email list is in reverse chronological order – most recent at the top, just like the articles appear on the main web page.
The previous/next links at the bottom of the article are like a book – the earlier pages are to the left; the newer ones to the right.
That’s fairly usual, isn’t it?
Wilbur
Paul, PLEASE give us back the Previous/Next navigation buttons at the top of the page like was available on the older version. I revisit pages in a non-linear fashion and it is very frustrating to have to scroll down to the bottom of a page to get to the navigation buttons when I get to the wrong article.
Pretty Please?
Paul Ducklin
I think we already answered you on that one – we’ll look into all these requests once the main changes needed after the site redesign are done.
(And do spare a thought for me, the author – what you are effectively saying is that you don’t actually read my articles, because you rarely get to the bottom. I don’t write my articles to be read non-linearly, after all :-)
Wilbur
Sorry – I didn’t see a response to my previous requests, I must have missed it. As for your concern, rest assured I read all of your articles linearly and completely. I also read most other articles linearly the first time – the problem comes in when I return to the site to revisit an article and click the wrong link in the saved email. When I say “non-linearly” I am referring to the order in which multiple articles are read, not the way a specific article is read. Sorry for my poor wording.
Your articles are always worth a second or third read (linearly, the way you intended).
Paul Ducklin
Thanks! (I am reassured ;-)
I’m not really invovled in site design, but I know that Prev/Next buttons are likely, if not definite, to make a return at the top. (I prefer them at the end of the article, so perhaps we’ll have both :-)
Sootie
from which seemed to dropped off on New Year’s Eve?
Should be From which seemed to drop off on New Year’s Eve?
Paul Ducklin
Errr, your original quote and your suggested replacment are the same :-)
Rich
They’re not, his correction has changed “dropped” to “drop”. It should either be “seemed to have dropped off” or “seemed to drop off”
Paul Ducklin
Hah! I’ll see my own mistake, and raise myself another mistake.
Fixed. Thanks. Sorry about that.
Someone
There is a typo, it says earliver instead of earlier.
Paul Ducklin
Fixed, thanks.