Thanks to Anand Ajjan of SophosLabs for his behind-the-scenes work on this article.
The evolution of ransomware is always a hot topic, or at least a hot under the collar topic, because of its odiousness.
Not that any malware is pleasant, of course, but ransomware – which scrambles your files and holds them hostage until you pay a ransom to unlock them – often means sending hard cash (usually in the form of bitcoins) straight to the crooks.
During 2015, we wrote on the topic many times, covering ransomware with names such as Teslacrypt, TorrentLocker, Los Pollos Hermanos (really!) and, perhaps the best-known present-day threat, CryptoWall.
CryptoWall has been around for some time, and is currently at what is commonly referred to as “Version 4.0,” as though it were a legitimate application that recently enjoyed an update.
We wrote in some detail last year about CryptoWall 3 as part of a paper looking at how ransomware had evolved from 2014 to 2015.
When CryptoWall 4 appeared, its most immediate and visible external difference was that it spiced up its “now you have to pay” message with taunts and jibes, together with a blunt reminder who was holding all the aces:
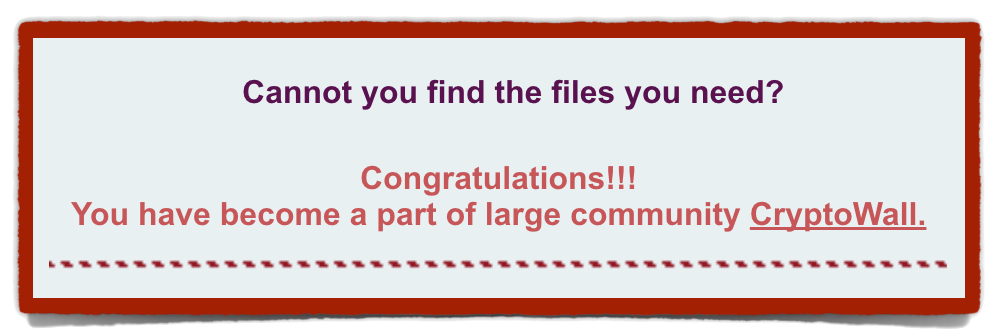
Cannot you find the files you need?
Congratulations!!!
You have become a part of large community CryptoWall.
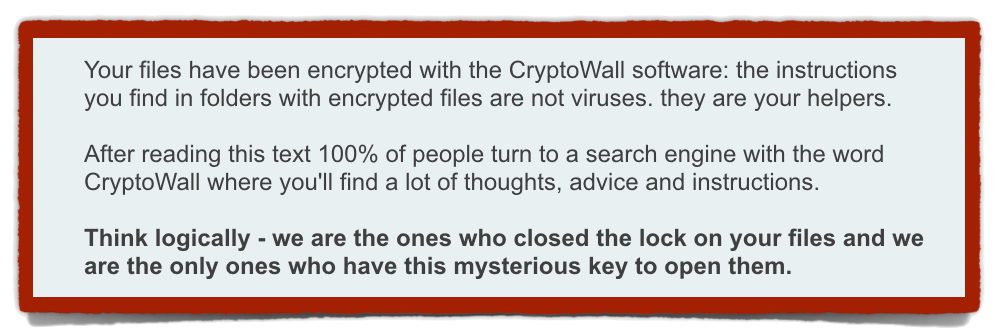
Your files have been encrypted with the CryptoWall software: the instructions you find in folders with encrypted files are not viruses. [T]hey are your helpers.
After reading this text 100% of people turn to a search engine with the word CryptoWall where you’ll find a lot of thoughts, advice and instructions.
Think logically – we are the ones who closed the lock on your files and we are the ony ones who have this mysterious key to open them.
But there were various other changes from the earlier versions of this threat, and we thought it would be not only interesting, but also informative, to take a look at the tweaks that the crooks behind this threat have made.
HOW CRYPTOWALL INFECTS
CryptoWall 3 installed several copies of itself, presumably hoping to give itself the biggest chance of success, using all of these common malware locations:
- The Application Data folder (%appdata%), where legitimate applications are supposed to store their data (not to hide other programs).
- The Startup folder (%startup%, a list of programs that will load automatically when you restart.
- A randomly-named folder on the root drive, usually C:\.
You might wonder why CryptoWall needs to worry about surviving a reboot, given that once it has activated and scrambled your files, the damage is already done.
In common with many other ransomware strains, however, CryptoWall doesn’t start encrypting right away.
It waits until it has connected out to one of the encryption-key servers run by the crooks and received back a one-time scrambling key.
That means the one-time key only ever needs to be kept in memory on your computer, so there is no local copy you might later be able to undelete to avoid paying up.
Of course, it also means that if you are offline, or connected to a network where the “call home” fails, the malware will need to survive until later, perhaps when you get home and start up your computer again.
But even though saving more local copies of the malware gives the crooks a bigger beachhead on your computer, it also makes detection – whether by accident or design – more likely.
So, CryptoWall 4 simplifies things a bit, stashing itself only in %appdata%, and setting a registry entry so it loads at every logon or reboot.
WHAT CRYPTOWALL DOES TO YOUR FILES
Cryptowall 4 scrambles your files in the same way as its predecessor, using AES with a randomly-generated key for each file.
The per-file AES keys used by CryptoWall are stored locally, but only after those keys have themselves been encrypted using the one-time scrambling key received from the crooks. That means every file encrypts differently, even if it has the same content, so you can’t use decryption hints from one file to decrypt any others. But it also means that all the different per-file keys can be unlocked with the same “master key,” of which just one saved copy exists, on the crooks’ own network. That’s the one they offer to sell back to you.
However, one big difference is that CryptoWall 4 scrambles all your file names, as well as their contents.
We can only guess why the crooks made this change in procedure, but we assume it is to give the malware a bigger fist to swing in your face.
You don’t need to open up a sample of scrambled files to find out that they’re illegible: the evidence is right there in File Explorer, and the scope of the damage is more immediately visible, too.
WHAT CRYPTOWALL TELLS YOU TO DO
CryptoWall 4, like its predecessors, makes sure you know where to go to pay the money to get your data back.
In every folder where scrambled files exist, the malware leaves behind ransom notes in HTML, PNG and TXT format.
That means they’ll open up in an image viewer, a text editor or your web browser:
In CrypoWall 3, the files were called DECRYPT-INSTRUCTIONS, but this time they appear with the more plaintive name of HELP_YOUR_FILES.
As mentioned above, the wording in the files is rather more cynical than in previous CryptoWalls, but the change in filename and content is probably not only about attitude, but also about detection, or about avoiding it.
The last thing the crooks want, once they’ve got far enough to demand money, is that you download an anti-virus that can detect the threat and remove all its files…
…including the ones that say where to send the money!
WHAT TO DO?
Prevention is better than cure – and even if it comes to cure, your own backup is better than getting into bed with criminals:
• Keep your software and operating system patched.
Malware, including ransomware, is often delivered via exploit kits, which use known security holes to break in and perform illicit installations.
• Use an on-access (real time) virus scanner and keep it up to date.
Anti-virus software can’t detect all new malware proactively, but it will often block and prevent ransomware attacks if used correctly. Ransomware is often delivered using old malware that is already active on unprotected computers.
• Avoid unsolicited or unexpected attachments.
Ransomware can be packaged into booby-trapped files such as documents, which claim to be fake invoices, unpaid invoices, or other files you may feel pressurised into opening.
• Make regular backups, and keep at least one recent backup set off-site.
Whether you store an encrypted hard drive at a friend’s house or use a cloud-based backup service, you are protecting yourself from much more than ransomware.
If your hard disk fails, then no amount of money – neither bitcoins nor dollars – is going to help.
Image of brick wall courtesy of Shutterstock.

Bob
Nice hat.
appu
any resolving techniques
Bryan
CryptoWall 4 scrambles all your file NAMES as well as their contents.
Surprised to learn this wasn’t part of version one; anyone clever enough to conceive the stunt should expect me to look first for my taxes and focus on recovering the same.
I needn’t pay ransom to re-download all my precious kitty videos.
jet86
Personally I’m surprised they changed it. I’d be more tempted to pay if I could see which files are sitting there, encrypted, compared to just a random bunch of file names. Remember that you would pay the one ransom to get the master key which will restore both your tax files AND your kitty videos – which one is more important to you doesn’t affect how you decrypt them. Thankfully I have on-site and off-site backups of my computers, so if I ever get hit I can just restore back to the last backup.
Anonymous
my friends computer has just been infected with some kind of Ransom virus. Geek Squad has been no help. It seems it’s the CryptoWall 3 from what you’re saying the message was (which is what his says) and it kept saying everything was on the “F: drive” which he doesn’t have.
He has no backup unfortunately. Is there a way to save this PC and just wipe it and start over. He realizes his files are gone. Should he just get a new computer?
any suggestions would be helpful. Also, what is this virus protection you mention. He had webroot and it was running and up to date.
Thank you
Kim
jet86
As long as your friend is happy to lose EVERYTHING, then what they would probably want to do is format the hard drive and reinstall Windows (I am assuming they are running Windows). They should have either a Windows installation disc if they purchased it separately from the computer, or some kind of restore disc if it came preinstalled on the computer (some computers use a restore partition instead of a separate disc – they should consult any documentation that came with the computer for the exact procedure to follow).
Regarding virus protection, there are many different ones available – you should at least check out what Sophos has to offer.
Herb Warren
Have you tried Windows previous versions in Explorer ? Google it.
Bryan
There’s a lag as Sophos comments are moderated, so you may eventually see nineteen replies here (I’m too lazy to read the ToS, so I hope “this is not a support forum” isn’t strongly-enforced tenet of the forum). If so… mods, I apologize; I’m more like Arrow than Flash.
New hardware shouldn’t be necessary; the drive can be completely erased and the operating system reinstalled. As long as
[a] he accepts the files are permanently lost
[b] you have a reliable, licensed means to reinstall (a recovery disk was once a common method, but media of any kind grows increasingly rare with the trending proclivity to streaming)
best of luck
Paul Ducklin
Yes, you can wipe and start over, and – if you’ve already crossed the bridge of “I’m ready to lose everything and to hell with the crooks” – it’s not a bad idea after a malware attack of this sort. Fresh start, and all that.
If you boot up from a Windows install DVD, there are typically two options: “keep your old stuff and reinstall Windows”, or “start fresh and lose everything so far”. If you start fresh, it’s sort of like buying a new PC. (Without the faster processor, bigger screen, and so forth :-)
As for virus protection…Sophos Home will protect your browsing and your downloads, and it’s 100% free. Once your friend has reinstalled Windows and got back online, he can get Sophos Home here:
https://home.sophos.com/reg
Anonymous
Even if someone does pay the ransom and gets the files back they should plan on wiping and re-installing the OS and applications. After an infection of any kind there’s no way to be sure something isn’t lingering in your system waiting to strike again.
obayas
thanx i knew nothing about this malware.
so pliz inform me incase of any news
jejaffe
This problem, albeit not in this form, was addressed more than a century ago. About 1911Rudyard Kipling, Nobel Laureate in Literature in 1907, wrote this about paying tribute.
http://nc3.mobi/references/2014-summary/#20141111
nick
how hard is it to catch these people? Is that a job for ASIO or can we form a possie and attack with pitchforks and torches?