A bank industry group in Singapore is warning customers about malware hitting Android phones that can steal credit card numbers and other customer details for fraudulent purchases.
The malware also has the ability to intercept incoming SMS text messages, which allows cybercrooks to steal the one-time passwords (OTPs) often sent by banks as a form of two-factor authentication when making a transaction.
The malware sends the eavesdropped OTPs to a command-and-control (C&C) server operated by the criminals.
The Association of Banks in Singapore (ABS) said its member banks have reported several incidents of Android banking malware infections over the past few months, affecting some of the 2.4 million mobile banking customers in Singapore.
There are different variations of the scam, which affects users who have been tricked into installing a malicious app.
According to ABS, banks have reported the malware disguising itself as a system update for Samsung devices.
SophosLabs has seen variations of this malware, disguised as Adobe Flash Player for Android. (The malware is identified by Sophos products as Andr/InfoStl-AZ and Andr/InfoStl-BM.)
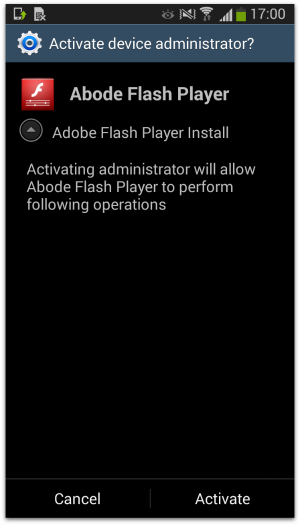
If you download the malware, it repeatedly asks for Device Administrator privileges in the hope that you will eventually relent, and click [Accept].
This is a trick designed to make the malware harder to remove than a regular app.
Once it’s active, the malware pops up bogus requests for bank and credit card account credentials, supposedly in order to install application or device “updates.”
One of the malicious pop-ups claims to be from WhatsApp, a popular mobile messenger with over 900 million users worldwide (including 72% of mobile internet users in Singapore, according to Statista), giving good odds that potential victims will have WhatsApp installed on their devices.
The pop-up asks for “billing information” to extend your WhatsApp subscription, like this:
Add or update your billing information to extend your WhatsApp subscriptions (0.99$/year) automatically.
This kind of social engineering is similar to other types of phishing scam, according to SophosLabs researcher Ferenc László Nagy:
It seems like it works similarly to phishing pages.
When it detects that a targeted banking application is launched (e.g. for Commonwealth Bank of Australia or National Australia Bank) is started, the malware presents a fake login screen.
SophosLabs analysis also shows that the app targets Google Play and Play Music as well, by popping up a bogus request for payment details.
To buy time once you have triggered a banking transaction, the malware pops up a fake system update message in the hope you will wait long enough for the crooks to grab and misuse the OTP sent back by your bank.

Mobile banking is increasingly popular, with mobile apps widely available from banks around the world, making it a lucrative target.
Ong-Ang Ai Boon, director of ABS, offered some sound advice:
ABS would like to remind mobile banking customers that smartphones are as susceptible to malware as desktop computers or laptops. Consumers are reminded to download applications only from trusted sources. As cybercriminals’ mode of operations and the malware are constantly evolving, visit your bank’s website for more information, latest updates and malware signs to watch out for.
Although this particular variation of Android banking malware is a recent addition to the cybercriminals’ arsenal, SMS stealers aren’t new.
SophosLabs has seen malware of this sort targeting mobile devices going back to 2011, when the Zeus/Zbot crimeware kit began infecting Android, Symbian, Windows Mobile and BlackBerry devices.
Mobile security tips and tools
- Follow these tips for safer online banking
- Check out our tips to keep crooks out of your mobile device
- Learn about the history of mobile malware
- Find out how to clean up and remove bad apps using Android Safe Mode
- Install a mobile security product (Sophos has a free security product for Android).
Image of flying money courtesy of Shutterstock.com.

MikeP_UK
BTW, there are numerous scam email appearing that purport to be from What’s App but are not. They all have a link that you should NOT click on.