 We’re calling the Sophos XG Firewall “the next thing in next-gen,” because of all the new technology and product innovations we’ve introduced to make your next-gen firewall simpler, faster, and more comprehensive than any other security product on the market today.
We’re calling the Sophos XG Firewall “the next thing in next-gen,” because of all the new technology and product innovations we’ve introduced to make your next-gen firewall simpler, faster, and more comprehensive than any other security product on the market today.
Today I want to talk about how we’ve rethought the way firewall policies are managed. If you’ve ever set up or managed rules on a firewall, you know first-hand how frustrating it can be. Most firewall products have policies across multiple functional areas for web, IPS, app control, traffic shaping, or WAF. And on top of that, they often span multiple tabs or screens, with little-documented prerequisites that force you to back up and start over. It’s a wonder how anyone can properly secure a network using such a disorganized and complicated framework.
In this blog post, I’ll explain some of the ways we’ve dramatically simplified policy management to save you time and improve security. If you prefer to watch rather than read, everything you need to know about the new policy model is in this short video.
Unified Policy Management
With the new XG Firewall, we took the opportunity to completely re-think the way policies are organized and managed. Instead of having you hunt around the management console looking for the right policies, we collected all the policy management into a single unified screen. You can now view, filter, search, edit, add, modify, and organize all your firewall rules in one place.
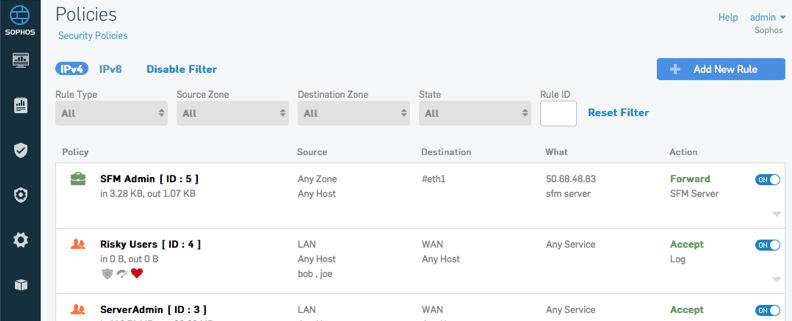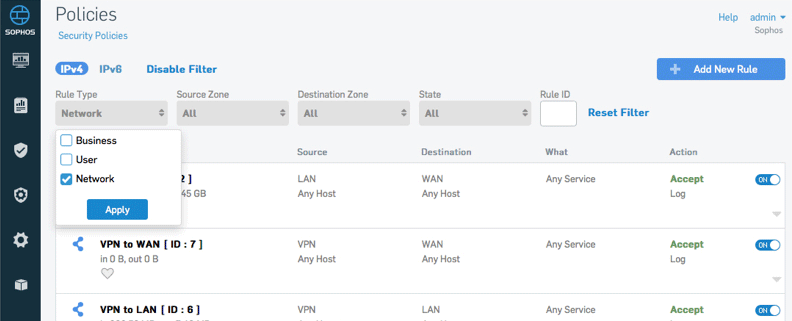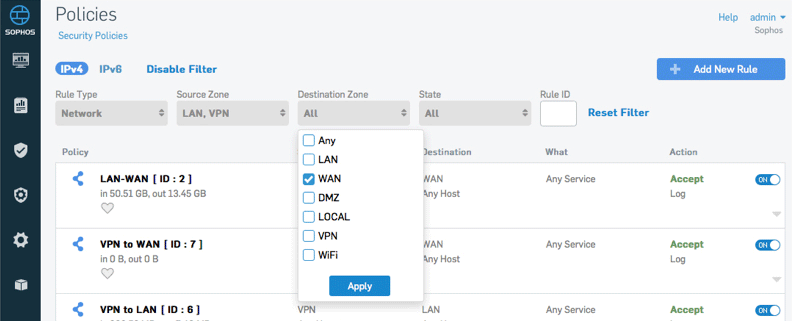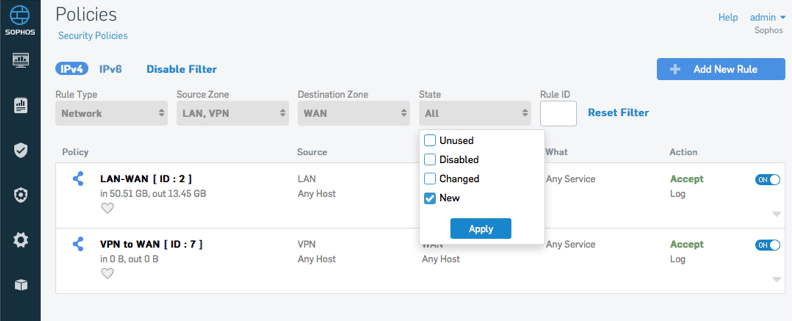
Policy Management at a Glance
Policy types for users, business applications, and networking make it easy to view just the policies you need while providing a single convenient screen for management.

Indicator Icons provide important information about policies such as their type, status, heartbeat requirements, and much more.
Natural language descriptions help you understand what a policy is doing in simple language long after you’ve configured it.
Layer-8 User Identity
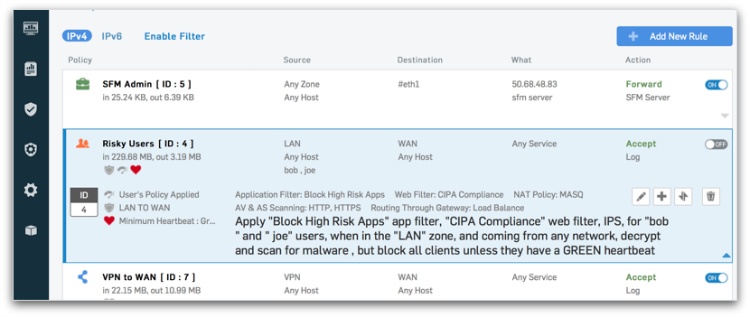
Sophos Firewall OS integrates our patented Layer-8 identity based policy technology, enabling user-level controls over applications, bandwidth and other network resources, regardless of IP address, location, network or device. It literally takes firewall policy to a whole new layer.
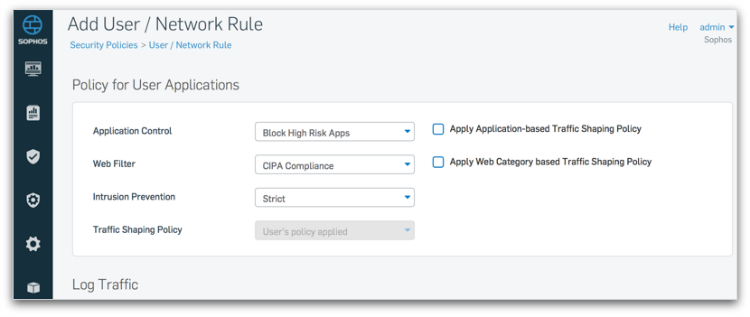
User-based Policy offers full Layer-8 control over applications, websites, categories and traffic shaping (QoS) all on a single panel. In most other firewall products, this would require four or five different policies, all on different screens. Our integrated policies dramatically reduce firewall rule count and make policy management a lot easier.
Flexible authentication options enable you to easily know who’s who and include directory services such as Active Directory, eDirectory, LDAP as well as NTLM, RADIUS, TACACS+, RSA, client agents or a captive portal.
Security Heartbeat Policy
An industry first, Sophos Security Heartbeat™ links your endpoints and your firewall to immediately identify systems compromised by advanced threats. You can establish policies that automatically isolate or limit infected systems until they can be cleaned up.
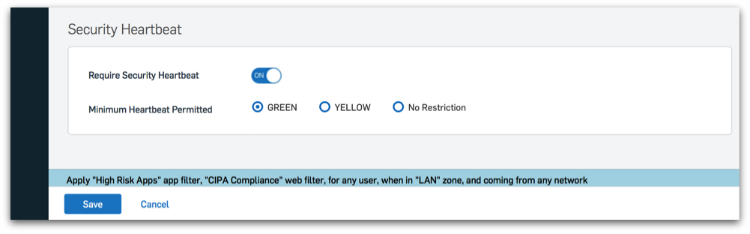
Green Heartbeat status indicates the endpoint system is healthy and should be allowed to access all network resources appropriate for that user.
Yellow Heartbeat status indicates a system may have a potentially unwanted application (PUA) or other issue. You can choose which network resources a yellow heartbeat is allowed to access until the issue is resolved.
Red Heartbeat status indicates a system that is infected with an advanced threat and may be attempting to call home to a botnet or command-and-control server. You can easily isolate systems with red heartbeat status until they can be cleaned up to reduce the risk of data loss.
Policy Activity Monitoring
If you’re like most network admins, you’ve probably wondered whether you have too many firewall rules, and which ones are really necessary and which ones are not actually being used. With Sophos XG Firewall, you don’t need to wonder anymore.

The Active Policies panel right on the control center indicates exactly how many policies you have of each type, including how many are unused, disabled, changed and recently added.
Unused policies are policies that are no longer required or meeting a need. Unused policies may benefit from some housekeeping as they can present potential openings or vulnerabilities in the network.
Business Application Templates
Pre-defined policy templates help you quickly protect common applications like Microsoft Exchange or Sharepoint. Simply select policies from a list, provide some basic information, and the template takes care of the rest. It automatically sets all the inbound/outbound firewall rules and security settings for you.
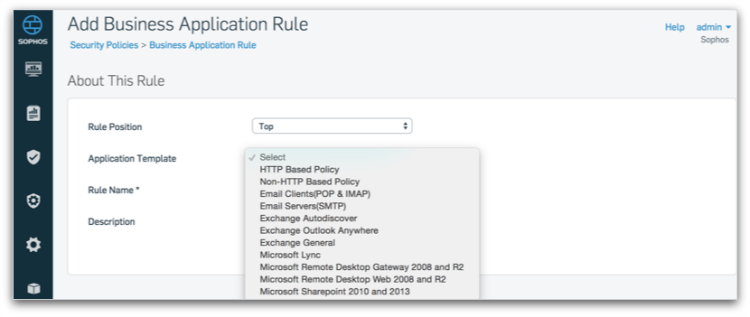
Predefined templates enable you to protect common business applications and set up new policies quickly. We will be adding more templates over time that you can take advantage of.
Custom templates enable you to create your own business application templates for your unique business applications or for less common applications.
You can share templates easily. Because all templates are stored in XML, they are easily shared between different systems or across customers if you’re managing multiple customer networks.
Sophos XG Firewall
These innovations in policy management are just a sample of how Sophos is making your firewall simpler, faster, and more-in-one. In the days and weeks ahead, we’ll be showing you more about how Sophos XG Firewall is revolutionizing network security.
Subscribe to the Sophos Blog to keep up with the latest product insights and news. Simply enter your email address in the sign-up field in the upper right corner of the blog homepage to receive our newsletter. You can also sign up for our RSS feed.

Leave a Reply