
We’ve written about ransomware a lot, because it’s such an odious and in-your-face sort of threat.
Ironically, ransomware isn’t actually the most dangerous or insidious sort of malware.
Ransomware crooks don’t steal your data covertly, or keep track of you via your webcam, or try to read your emails over an extended period for competitive advantage.
But ransomware is still a big, bad body-blow for anyone who hasn’t taken the right precautions, such as a recent and safely-stored backup.
To summarise briefly:
- Ransomware scrambles your personal files using a random, one-off encryption key.
- The key is sent to the crooks and then wiped from memory locally, so the crooks have the only copy.
- A message appears, offering to sell you back the key so you can recover your files.
Usually, you have to use a payment system such as Bitcoin.
That means the transaction is hard to trace, so the crooks can hide, and as good as impossible to reverse, so you won’t get your money back
Of course, this means that the crooks could simply take your payment and run, but for the most part, they don’t.
Indeed, the cybercrooks in the ransomware scene have built up a reputation for “dishonest reliability,” so that if you do pay, you probably will get your data back.
Surely some shortcut?
We’re often asked for help by ransomware victims who assume that there must be some way of recovering their data without paying up, even if it’s not obvious, or is very complicated.
But unless the crooks make a programming error, ransomware can be as good as hack-proof, thanks to strong encryption.
Sometimes the crooks do blunder, and then there’s a faint hope of getting some data back:
- The malware might temporarily put a copy of the decryption key in a hidden file or registry entry, and forget to delete it.
- The crooks might make encrypted copies of your files and forget to delete the originals.
- The encryption might be programmed badly, perhaps using a decryption key that never changes or isn’t very random, so you may be able to guess it.
Unfortunately, those are the exceptions these days, as the ransomware criminals have learned from their earlier mistakes.
Most modern ransomware gives you almost no chance of recovering without paying, unless you can afford to spend large sums on forensic analysis, and then also just happen to get lucky finding some left-over data from before the attack.
In short, if you don’t have backup, and you do care about your files, you don’t have much choice but to pay.
→ Some users have even told us that it was cheaper to pay up than to go through IT to get their files recovered officially, which sounds like a good reason to streamline your backup process. If you can’t restore effectively, then it’s not really a backup, is it?
Insult to injury
Ransomware families you may have heard of, past and present, include CryptoLocker (now defunct thanks to a law enforcement operation), CryptoWall, TeslaCrypt and even Los Pollos Hermanos, named after the restaurant run by crooks in in the TV show Breaking Bad.
To add insult to injury, the crooks behind the CryptoWall ransomware have now taken to spicing up their “get your data back” instructions with taunts and jibes added to Stage 3 above.
The crooks pop up a web page that tells you, amongst other things:
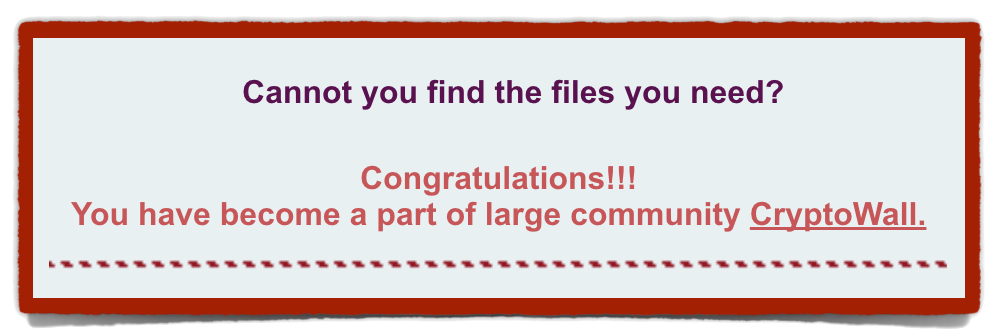
Cannot you find the files you need?
Congratulations!!!
You have become a part of large community CryptoWall.
Then they say:
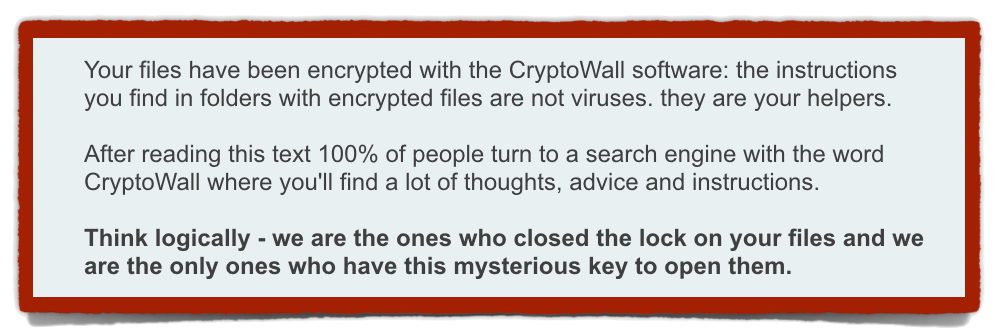
Your files have been encrypted with the CryptoWall software: the instructions you find in folders with encrypted files are not viruses. [T]hey are your helpers.
After reading this text 100% of people turn to a search engine with the word CryptoWall where you'll find a lot of thoughts, advice and instructions.
Think logically - we are the ones who closed the lock on your files and we are the ony ones who have this mysterious key to open them.
Later on, they turn their malicious irony on the security community:
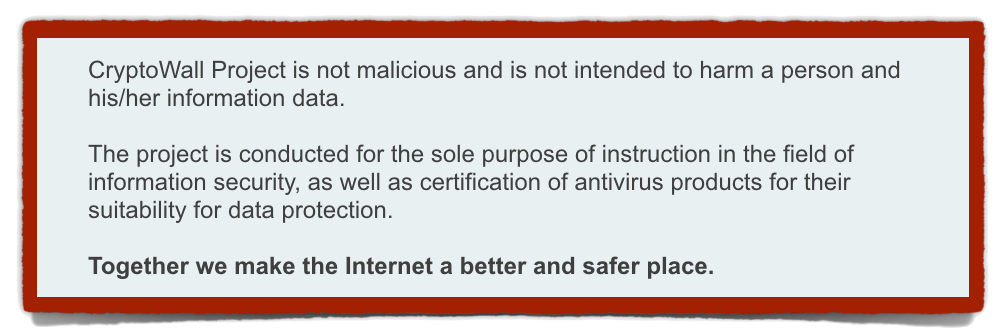
CryptoWall Project is not malicious and is not intended to harm a person and his/her information data.
The project is conducted for the sole purpose of instruction in the field of information security, as well as certification of antivirus products for their suitability for data protection.
Together we make the Internet a better and safer place.
Ho hum.
What to do?
Prevention is better than cure – and even if it comes to cure, your own backup is better than getting into bed with criminals:
• Keep your software and operating system patched.
Malware, including ransomware, is often delivered via exploit kits, which use known security holes to break in and perform illicit installations.
• Use an on-access (real time) virus scanner and keep it up to date.
Anti-virus software can’t detect all new malware proactively, but it will often block and prevent ransomware attacks if used correctly. Ransomware is often delivered using old malware that is already active on unprotected computers.
• Avoid unsolicited or unexpected attachments.
Ransomware can be packaged into booby-trapped files such as documents, which claim to be fake invoices, unpaid invoices, or other files you may feel pressurised into opening.
• Make regular backups, and keep at least one recent backup set off-site.
Whether you store an encrypted hard drive at a friend’s house or use a cloud-based backup service, you are protecting yourself from much more than ransomware.
If your hard disk fails, then no amount of money – neither bitcoins nor dollars – is going to help.
Free Virus Removal Tool
The Sophos Free Virus Removal Tool works alongside your existing anti-virus to find and get rid of any threats lurking on your computer.
Download and run it, wait for it to grab the very latest updates from Sophos, and then let it scan through memory and your hard disk. If it finds any threats, you can click a button to clean them up.
Ransom note letters courtesy of Shutterstock.

Tom
Back up or pay up! I’ve been doing backups of my servers since 1992 (when I used QIC’s). There are so many options for backing up data. If you’re lazy, use one of the well known online services. If you’re cheap, use a NAS or USB external HD. It’s not just ransomeware, it’s malware, crashed drives, user errors (“I think deleted the invoice spreadsheet for last year.”) Once you lose your data, you don’t ever mind doing backups again.
Dan
You do realize that cryptoware and ransomware can spread across network shares and ultimately encrypt those devices as well along with all connected removable mounted devices. So backing up would be moot, and also it should be recommended that once a backup is done unmount the device and disconnect it from the network until next time.
jejaffe
Make your backups with removable media. I use an old P4 with large capacity mirrored drives to “echo” my workstations via an old-style batch file run after each work session. (break time, right before lunch, end of day etc.)
Once a day use high capacity USB 3 memory sticks to backup the P4. It takes time, but the P4 isn’t being used by a human at the time. The most recent memory stick is off site, the others, in another room.
Jonathan @NC3mobi
Laurence Marks
Paul, you didn’t state whether Sophos AV detects and inhibits Cryptowall, TeslaCrypt, Los Pollos Hermanos, or even CryptoLocker. Does it?
Paul Ducklin
Yes, we do detect and block them, though of course new variants come and go all the time. For precise detection details you can look at the other articles I’ve linked to.
Our generic detection will show up in your logs as HPmal/Ransom-*, if you want to check for it.
This sample is detected specifically as Troj/Ransom-BPB, if memory serves. Other people are calling it “CryptoWall 4.0” but that sounds a bit too legitimising for me.
throwaway102983
I got infected with Cryptowall v3 with Sophos Endpoint Protection installed 2 months ago.. didn’t detect anything until it finished encrypting the entire filesystem. I would understand if it didn’t prevent it from spreading but it didn’t even detect malicious behavior at all.