
This week, the White House unveiled a new strategy for modernizing the US government’s cybersecurity, and there’s a lot of work to be done.
Last year, a US Senate report found the government’s cybersecurity to be shockingly bad; even computer systems at the US Department of Homeland Security, an agency with significant cybersecurity responsibilities, were found to have “hundreds of vulnerabilities” due to out-of-date software.
It’s hard to keep track of how many times the US has been victimized by cyberattacks – in the past year, there have been breaches at government agencies from the US Postal Service to the IRS, and all the way up to the White House.
Russian attackers breached the unclassified email system at the US State Department, accessed the secure email communications of President Obama, and compromised the email system of the Joint Chiefs – the highest ranking US military officers.
In June 2015, the biggest and most devastating breach in US government history compromised the private information of more than 20 million current and former US government employees (the attack was blamed on China, perhaps the US’s biggest cyber-adversary).
It’s not just sophisticated state-sponsored attacks that have broken through the US government’s cyberdefenses – low-skilled hacktivists like the self-described teen stoners who hacked the director of the CIA‘s unclassified, personal email account have had their successes too.
After the mega breach at the Office of Personnel Management (OPM), the White House launched a 30 day “cybersecurity sprint” to rapidly identify and close the biggest security holes.
This week marks the beginning of the US’s new Cybersecurity Strategy Implementation Plan, which focuses on five key areas: protection of high-value assets and data; rapid response to attacks; rapid recovery and adoption of “lessons learned”; recruitment and retention of cybersecurity professionals; and efficient acquisition and deployment of new technology.
US Chief Information Officer Tony Scott said in announcing the new plan that there are no “silver bullets” and “cyber threats can not be eliminated entirely.”
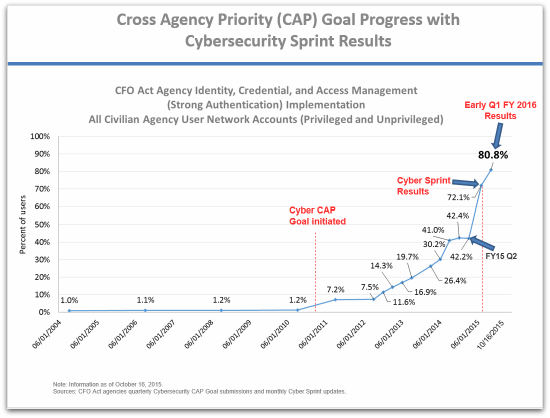
Scott did, however, point to some successes as a result of the cybersecurity sprint and continued efforts since then – including a rapid growth in the use of “strong authentication” such as the government Personal Identity Verification (PIV) card.
Since the OPM breach, the percentage of employees using strong authentication has doubled, from about 40% to 80.8% (see chart below).
Defending the US government from near-constant attacks is not an easy job. There are hundreds of agencies to protect, each responsible for their own IT systems.
And the US government has over 2.6 million civilian workers and another 1.4 million uniformed military personnel.
To put it in perspective: the US government employs 4.1 million workers, almost twice as many people as Wal-Mart, the country’s largest private employer – and the 212 biggest private employers in the US combined have 4.4 million workers.
Protecting such a broad attack surface is a daunting task, which is why the US cybersecurity plan calls for a “defense in depth approach that relies on the layering of people, processes, technologies, and operations,” Scott said.
It sounds like a good strategy, but cybersecurity ultimately depends on users making smart decisions and following protocols.
To prevent the next big government hack, US bureaucrats, diplomats, soldiers, sailors and other civil servants – from mail clerks to astronauts – will all need to do their part.
Image of digital George Washington courtesy of Shutterstock.com.

Michael Argast (@michaelargast)
Quote from the article “cybersecurity ultimately depends on users making smart decisions and following protocols”.
Wrong.
Don’t get me wrong, users certainly have a part to play in security, but stating that security *depends* on users making smart decisions and following protocols completely eliminates the consideration of security design, architecture, data strategies, etc.
It is possible to design systems and processes that make it difficult for users to make good choices, and likewise in some cases it is possible to design systems that make it difficult for users to do stupid things.
Your article puts the weight on users as having primary responsibility, which in my mind is unfair.
I’ll use an analogy. You could say “drivers are ultimately responsible for their safety on the road, making the right choices and driving safely is critical”. While it is a somewhat true statement, it completely ignores road design, vehicle safety, other drivers, etc.
Stop blaming users.
Mark Stockley
If, after all the gizmos, gadgets, policies, laws, strategies and user education has been done a user can still undermine their own safety or the safety of others whilst driving then I think it’s fair to say that car safety depends on drivers without that being characterised as blame.
Ditto cybersecurity.