
Apple just released iOS 9.0.2.
This new version claims to close the well-publicised Lock screen hole that lets anyone view and edit your contacts, send text messages, and rummage through your photos – without entering your passcode.
If you had an iOS 9 or 9.0.1 device with Siri accessible from your lock screen, you were vulnerable regardless of the type or length or your passcode, and regardless of whether you had turned on TouchID.
We tried the trick on an iPhone running iOS 9.0.1 and confirmed that it worked with a 6-digit numeric and 8-digit alphanumeric passcode.
So, we decided to try it again with iOS 9.0.2.
We tested on an iPhone 6 (the same device used in our previous tests) running the newly-released 9.0.2, again with both a 6-digit numeric and an 8-digit alphanumeric passcode.
Good news: it seems that Apple removed a link in the chain to stop this hack from working, because we weren’t able to skip the passcode and get at contacts and photos as we had before.
Despite the fix, however, we still recommend that you turn off Siri on the Lock Screen.
The more features you have available from your Lock screen, the less locked your Lock screen becomes, and the more that could go wrong.
And Siri has been associated with Lock screen trouble before, so here’s how to turn her off.
How to disable Siri on the lock screen
Go to Settings | Touch ID & Passcode, and under Allow Access When Locked, toggle Siri off:
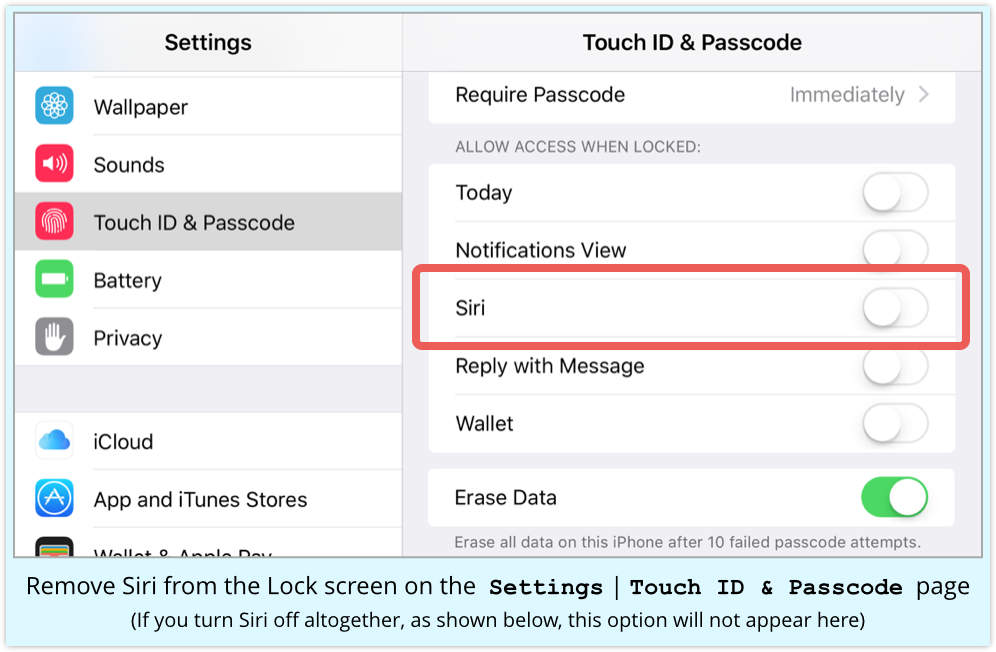
Some other settings you may want to consider while you’re about it, as configured in the screenshot above (yes, that’s a Naked Security iPhone):
- Set Require Passcode to Immediately.
- Turn off everything you can under Allow Access When Locked.
- Enable Erase Data after 10 failed passcode attempts.
How to turn Siri off altogether
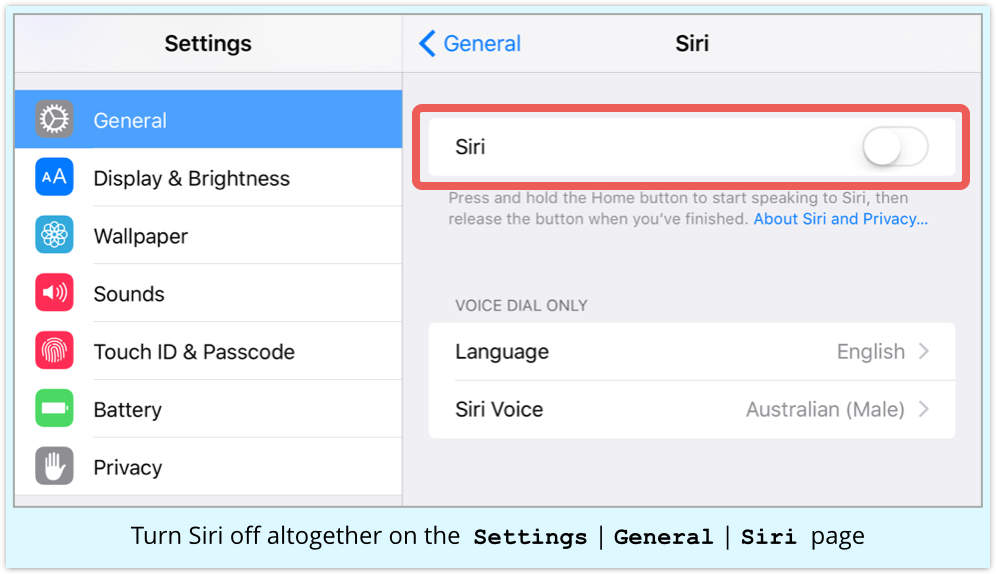
You may want to go all the way, and turn Siri off altogether.
Go to Settings | General | Siri and toggle to off:
Learn more
For more advice on what to do when you review your phone’s security settings, please take a look at our popular article, Privacy and Security on Your Phone. (Covers iOS, Android and Windows Phone.)
– Phone v. Phone courtesy of Shutterstock –

Tim S
Don’t enable erase data after 10 failed login attempts if you have children!
Paul Ducklin
Or, if you have an iPhone that you use for Real Work, don’t let your children play with it. It’s not a toy.
justiceISfake
Paul do you have children and a phone… no matter what they will get a hold of it at some point.
loadtest
The trouble with enabling Erase Data after 10 failed passcode attempts is that you can hand your phone to someone and they fairly quickly erase your data, totally inadvertently.
Many people like to guess passcodes… and often this setting results in tears. It’s much easier to remote wipe your device via the iCloud website once it’s lost.
Disabling the control center prevents someone putting the device into airplane mode. It does not prevent a power-down, but should that ever happen you iCloud Lock can be used to persist the “lost or stolen” state on Apple’s servers for when it powers back on.
Paul Ducklin
I hear you. But no-one can erase your data “inadvertently,” in my opinion.
What we really need are social mores under which dicking around with my iPhone to guess the password for your own comic purposes is no more acceptable than spiking my drink or yanking down my trousers in public, “because it’s a laugh to see the results.”
Stef
Duckers, you told me you liked the trousers thing! :)
But seriously, you are absolutely right, why would you hand your phone to someone anyway unless genuinely to make a call, and even then it would be under closely scrutinized conditions (**remembers the scene from Mr. Robot**).
Slight digression from the topic, but given the high value of things like iPhones I’d treat it very carefully overall. I had a work colleague who bought a brand new iPhone 5S who was out in the company car park when a colleague asked to have a look at it and then promptly dropped it on the floor!! Cue one damaged iPhone and a colleague who wouldn’t take responsibility.
Trust No-One…
Ocean Midge
Not really – after 5 sequentially failures it stops you guessing for 1 minute and after 6 it stops you for 5 minutes. This, generally speaking, is going to prevent someone from inadvertantly wiping your data as waiting for what I assume is a lot more than 6 minutes (I got bored when it locked for 5) in order to keep guessing your passcode suggests that they’re malicious rather than accidental.
Paul Ducklin
+1
Anonymous
Youre being sarcastic about swiftly, right?
Paul Ducklin
No.
About 50% of iDevices in existence are on iOS 9 already. The bloke who came up with the “hack” told Apple about it at almost exactly the same time iOS 9 was released, two weeks ago. *You* try preparing out a global patch for a bug like this in two weeks that will go OTA to gadzillions of user devices :-)
Remember that’s not just writing the new code and saving it into a version control system where others can access it, Android style. That’s two weeks to a patch that’s available OTA. Compare this to Google’s time to fix Stagefright, say, even in its own branded devices, and I think we are allowed to say, “Swiftly.”
Sammie
iOS is starting to look like Java, “An update a day keeps security at bay”
Paul Ducklin
Except that with Java, the updates are only published every three months.
Anonymous
Stop using the word “hack” when you mean “bug”. please.
Paul Ducklin
I used the word “hack” where I meant “hack.” If I had meant “bug,” I’d have written “bug.”
(But I think you knew that, and are just being linguistically pedantic, like people who insist that “egregious” must still be used only in its original, 16th century sense of something extraordinarily *good*, rather than terribly *bad*, as we use it today.)
I chose “hack” to denote that you need to follow a specific sequence of sneakily-timed operations to make use of one or more bugs, one or more of which has now been patched so the sequence of sneakily-timed operations no longer achieve the hacky result it used to.