Back in 2012, a man in the South of England was apparently renovating his chimney when he came across the skeleton of a pigeon.
One leg bone had a capsule attached, which turned out to contain what looked very much like a coded message dating back to World War 2.
The British made extensive use of homing pigeons during the war as a way to get messages back from Nazi-occupied Europe to England.
The system was not without peril, both to the birds (apparently the majority didn’t make it back) and to the message-sender releasing the bird, who faced the death penalty for espionage if caught.
With 70 years having passed, little more to go on than “likely place of release – 1940s France”, and no indication of what code or cipher had been used, even the UK’s code-breaking boffins at Bletchley Park warned that the message would probably never be cracked:

One-time pad
If the sender was a field agent in occupied France, he may well have had a one-time pad, a sort of cipher that uses a randomly generated key that is as long as the message.
Only two copies of the key ever exist: the agent takes one key, or more usually a code-pad consisting of numerous sheets of daily keys, and the agent’s handler keeps the other.
By destroying one page of the code-pad each day, whether a message was sent or not, the field agent can ensure that each key is only ever used once, or not at all, and the handler can keep in synchronisation.
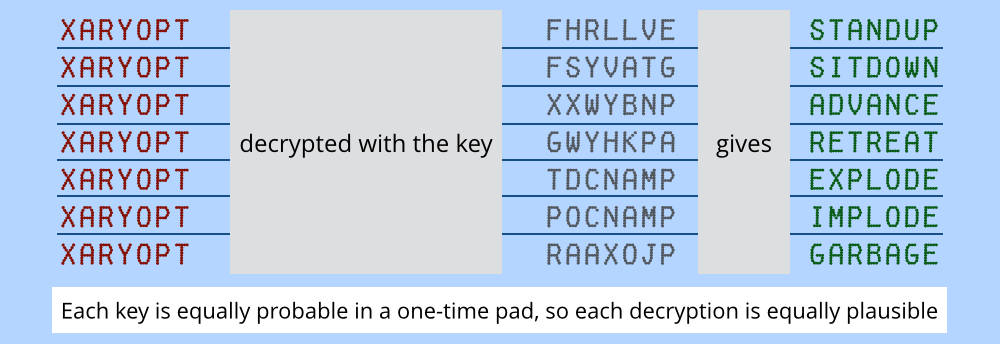
If each key really is used for one message only; if both copies of the key are handled securely; and if the key is truly random (i.e. no algorithm was used that could possibly be repeated), a one-time pad is completely and provably secure.
That’s because every possible string of characters is equally likely to have been the key, so there is no way to choose between different plausible decryptions.
Here’s an example to demonstrate, assuming that our encrypted message is XARYOPT.
Imagine that decryption involves shifting each encrypted letter back by the amount denoted by the alphabetic position of each key letter.
In other words, a key of A means “shift by 0” (M remains M), B means “shift by 1” (E becomes D), M means “shift by 12” (Z becomes M), and so on.
You can pick any possible key from AAAAAAA to ZZZZZZZ, so you can “decrypt” the message XARYOPT however you choose:
Code book
On the other hand, if decryption involved a codebook, for example so that HVPKG meant ARTILLERY and FNFJU meant MOVEMENTS, then in the absence of the codebook you would be stuck.
AOAKN, which is repeated at the start and the end of the message, might be some kind of delimiter, but for the rest of the message, you could come up with any decoding you like and claim that “your” code book was the right one.
For example, you might propose:
AOAKN = MESSAGE BEGINS/ENDS HVPKD = PLEASE FNFJU = TELL YIDDC = MUM RQXSR = I DJHFP = AM GOVFN = EATING MIAPX = MY PABUZ = VEGETABLES . . . AOAKN = MESSAGE BEGINS/ENDS 27 = COUNT OF CODEWORDS
In the absence of any other information, no-one would be able to prove you wrong.
Interestingly, even though every codeword in the encoded message is unique, except for AOAKN, that doesn’t mean there are no repeated words in the original message.
Codebooks often provide more than one encoding option for common words, so you can avoid telltale repetition in your coded text.
The first “solution”
In late 2012, a Canadian named Gord Young claimed to have decrypted the message easily, using his “great-uncle’s aerial observers’ notes, the WW1 code formula, and WW1 coding as a basis.”
Young chose to read off the code groups top-to-bottom, left-to-right, rather than starting left-to-right as they seem to have been written, and came up with this:
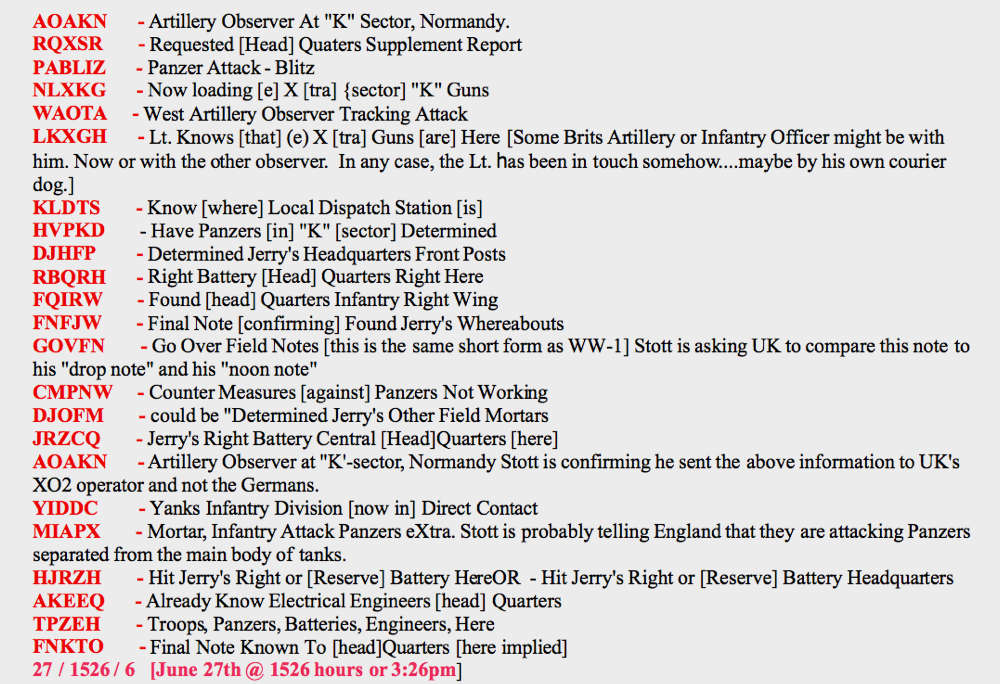
AOAKN - Artillery Observer At "K" Sector, Normandy.
RQXSR - Requested [Head] Quaters Supplement Report
PABLIZ - Panzer Attack - Blitz
NLXKG - Now loading [e] X [tra] {sector] "K" Guns
WAOTA - West Artillery Observer Tracking Attack
LKXGH - Lt. Knows [that] (e) X [tra] Guns [are] Here
. . .
DJHFP - Determined Jerry's Headquarters Front Posts
. . .
Criticisms of Young’s claim quickly appeared, pointing out details such as:
- Top-to-bottom reading is unlikely.
- Panzer (German tank) would not be in a WW1 codebook.
- Jerry (German soldier) would not be in a WW1 codebook.
- PABLIZ is wrongly transcribed and should be PABUZ.
There’s also the nagging issue that American troops were nicknamed Yanks in WW2, but Doughboys in WW1.
Additionally, it’s not clear how an aerial observer would have been able to receive a message from the Lieutenant’s hypothetical courier dog.
But the biggest problem with Young’s decryption is much more fundamental: it’s drivel.
No British observer in Normandy would have wasted a precious pigeon to send such nonsense.
Cracked at last?
And that was that for the Dead Pigeon code until last week, when a 22-year-old Spaniard, Dídac Sánchez, announced he’d cracked it at last.
He says that he started on the task when the news first broke about the message back in in 2012, and that he has been working on it ever since.
According to The Telegraph in the UK, Sánchez claimed to have spent a whopping €1,500,000 (about $1.7m/£1.1m) to solve the puzzle.
By this point, I’m sure you’re dying to know, “What was the pigeon trying to say?”
Here’s comes the suspicious part, I’m afraid.
Sánchez isn’t telling.
You’ll have to AOAKN ERFLP QSQMD WWEBN AOAKN 5 for the full story.
Image of pigeon postie courtesy of Shutterstock.


SamS
So the dead pigeon mystery continues…
Kévin Gosse (@KooKiz)
So… The guy assembles a team of experts, crack a code, derive a new encryption system from it, and market it as being “impossible to crack”. That’s… stupid?
I’ll pass on the “Mr Sánchez said during his quest he realised that a system no one understood anymore ‘offers wonderful commercial opportunities’. “. I think security by obscurity has been debated often enough.
In the end, I put my money on “just an obvious marketing stunt”.
Paul Ducklin
Yes, that made me smile.
It’s like spending ages to track down an annoying problem with your car that turns out to be the side-effect of a design flaw and thus something you just have to learn to live with…
…and then rushing out to trade in the defective car for the same model. Most people would pick another marque, let alone a different model, just because they could. But maybe Mr Sánchez knows something we don’t?
Joe
This occurred to me as well. If his product is based on carrier pigeon technology that was cracked in three years, I wonder if — in three more years — if it will be able to be cracked by a supercomputer in 3 seconds?
DC
Love your humor!
Paul Ducklin
Thanks!
There was originally an explicitly serious part in the article – my first draft had a warning at the end about “cryptographic snake oil,” and an explanation of why you need to be careful of amateur cryptography.
But it turned out that the story made those points much more, errrr, pointedly all on its own :-)
Stéphane
There is another unsolved text written on a door of a temple in Xian, China. 874 AD. Tang Dynasty. I’m trying to find a photo… it’s in a museum and it’s take pictures is forbidden.
mfernandezt2
@Stéphane can you tell us more about this, i am going to xian the next month. maybe i can take a pic, in what temple did you saw that?
Paul Ducklin
Taking pictures is forbidden. So don’t do that :-)
PaulW
Excellent article! “cryptographic snake oil” – love it :-)
Anonymous
Drink Your Ovaltine!
James
We have letters grouped into blocks of five characters each. That clearly indicates that it’s an activation key for Microsoft Windows Minus Sixty.
Rosa
Interesting about OTP. If OTP was used, wouldn’t the frequency count begin to approach noise for a crypt (say) of 100 characters or more? At a glance, the frequency of e.g., K, H and R compared to S is quite different for a longer 135 character crypt.