
Apple’s latest trove of updates was just announced.
OS X (in its regular and server flavours) and iOS get patches that can be considered both urgent and important.
Safari gets an update too, but it’s bundled in with the new iOS 8.4.1 and the OS X Yosemite 10.10.5 fixes, so you won’t see it as a separate download unless you’re using an older version of OS X.
Once you’re patched, your version numbers should look like this:
- OS X Yosemite 10.10.5
- OS X Mavericks 10.9.5 plus Security Update 2015-006
- OS X Mountain Lion 10.8.5 plus Security Update 2015-006
- Safari 8.0.8 (7.1.8 and 6.2.8 for earlier OS X versions)
- iOS 8.4.1
- OS X Server 4.5.1
Bugs fixed
The updates cover dozens of security holes, including:
- Denial of Service (DoS). A crook can crash your computer or a key service running on it pretty much whenever he chooses.
- Elevation of Privilege (EoP). A crook can promote himself to higher access levels than he’s supposed to have.
- Information Disclosure. A crook can see data or learn information that should be concealed.
- Remote Code Execution (RCE). A crook can shove malware onto your device without you even noticing.
When all these vulnerabilities are present at the same time, attackers can chain them together to turn what would otherwise be a minor incursion into a dramatic breach.
For example, Information Disclosure could expose a login secret that makes RCE possible as a regular user.
DoS could be used to create a diversion, or to suppress the alarm bells, while EoP could grab sysadmin powers for the compromised user account.
In short: patch now!
Understanding security vulnerabilities
Listen to our Sophos Techknow podcast
(Audio player above not working? Download, or listen on Soundcloud.)
Newsworthy holes closed
Recent newsworthy bugs that have been fixed this time round include:
• CVE-2015-3760: DYLD_PRINT_TO_FILE vulnerability
DYLD_PRINT_TO_FILE is a feature added in OS X Yosemite 10.10 that makes it easier for developers or IT staff to acquire troubleshooting logs from complex software that uses numerous different library components.
Unfortunately, the feature could be abused to send output data to unauthorised places, including modifying security-critical configuration files and overwriting system programs with malware.
This vulnerability was used in the wild, including by software detected by Sophos Anti-Virus as OSX/VSearch-A.
• CVE-2015-5477: BIND denial-of-service bug
DNS is the name-to-number service that makes the internet usable by humans, and BIND is a reference implementation for DNS.
That means BIND contains every possible DNS feature, which is handy for research and testing, but makes the code almost recklessly over-equipped for most real-world uses.
Nevertheless, precisely because it has everything you’ll ever need, BIND remains very widely used.
This bug made it easy for outsiders to crash DNS servers [listen at 10’49”] running the vulnerable versions of BIND, and attacks exploiting the hole were reportedly seen in the wild.
Not fixed yet
We can’t see any fixes specific to the Thunderstrike 2 attack.
That’s a trick whereby malicious code is written into the firmware of a plug-in Thunderbolt device, such as a network dongle, and used to modify a Mac’s built-in Boot ROM firmware.
The Mac firmware is supposed to be sacrosanct and secure: modifiable at initial bootup only, and only updatable to new firmware that is digitally signed by Apple.
Unauthorised and malicious firmware modifications would run every time you reboot your Mac, would load before OS X (and thus be able to subvert it), and would be very hard indeed to remove, especially if the firmware hack were to “close the door behind itelf.”
How to do update
To see if your Mac is up-to-date go to Apple Menu | App Store | Updates:
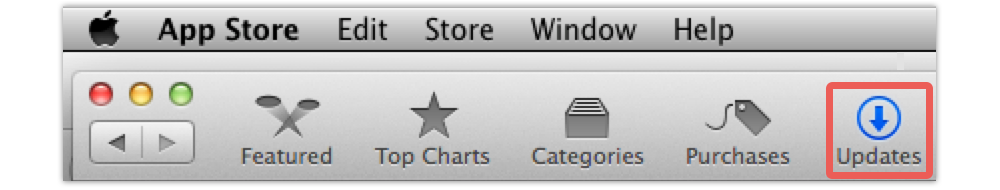
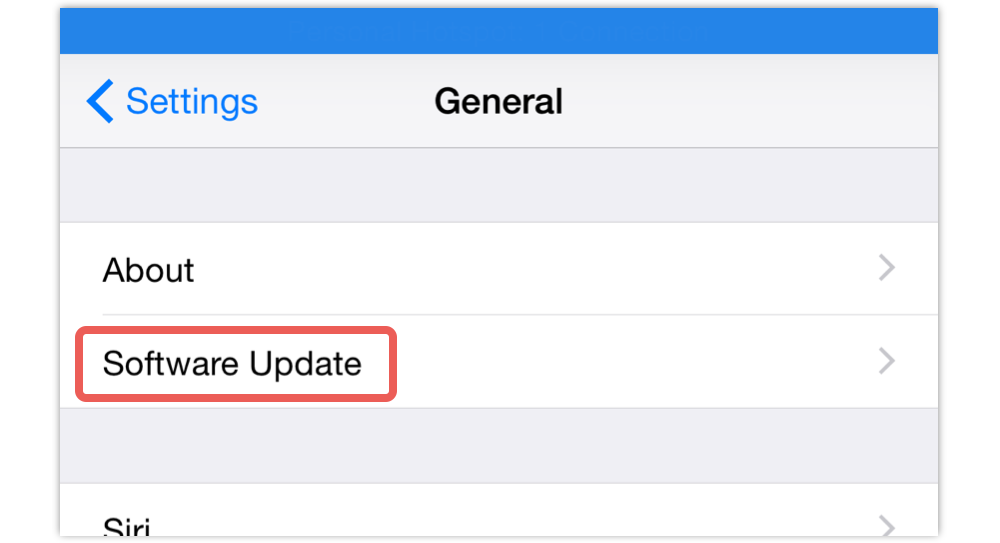
On an iPhone or iPad, use Settings | General | Software Update:

tartanrose
Thank you for another excellent article.
My iPad is now 8.4.1………….to anyone out there who is nervous about this update after reading some of the nonsense I saw online yesterday about this update…………………..DO NOT WORRY!
Because of time differences, and because I frequently check if a software update is available rather than waiting for notification I went on line to attempt to find out about this update as nothing had been posted by you guys yet.
As I mentioned a lot of doom and gloom, predications that people would need to return to the older version, etc, or worse still be unable to use the device any more.
Anyway I read your great article……..listened to the highly helpful podcast and installed the new version. Running beautifully..
Thank you Paul, Chester and Naked Security
Steve
With all the different bugs that Apple has patched in their new OS’s what’s a person to do who has an older laptop with say Snow Leopard? Get rid of it??
Paul Ducklin
You might consider switching to Linux, which still supports older 32-bit computers that can’t run the more recent versions of OS X.