 Malware that encrypts all of a victim’s files and holds them for ransom – what’s commonly called crypto-ransomware or cryptoware – continues to be hugely successful in making money for the criminal gangs who perpetuate it.
Malware that encrypts all of a victim’s files and holds them for ransom – what’s commonly called crypto-ransomware or cryptoware – continues to be hugely successful in making money for the criminal gangs who perpetuate it.
According to a public service announcement from the FBI’s Internet Crime Complaint Center (IC3), the CryptoWall variant of crypto-ransomware cost US businesses and consumers at least $18 million between April 2014 and June 2015.
That figure is based on complaints from 992 CryptoWall victims, and includes related damages such as the cost of network mitigation, loss of productivity, legal fees, IT services and credit monitoring services.
It’s not clear how much of the $18 million was paid out in ransom fees to the CryptoWall criminals, but the FBI said that the ransom demanded typically ranged from $200 to $10,000.
The FBI called CryptoWall the “most current and significant ransomware threat” in the US.
Although the FBI’s report of financial damages caused by CryptoWall is significant, it’s likely those figures represent only a tiny minority of the cost to victims worldwide.
It’s difficult to determine the exact number of crypto-ransomware victims, in part because many businesses caught in the ransomware trap don’t want to come out and say so (public sector organizations like police departments haven’t had the same luxury).
Equally hard is figuring out how much money the crooks have hauled in from their ransomware enterprises.
What we do know is that crypto-ransomware is highly effective, and lucrative enough for criminals to keep coming up with new forms of it – one survey found that 3% of UK citizens had been victims, and 40% of those had paid the ransom.
CryptoWall’s predecessor, CryptoLocker, was extremely successful – the crew behind CryptoLocker raked in an estimated $27 million in the first two months after it was unleashed in September 2013.
Although CryptoLocker was fatally damaged by a law enforcement take-down of its server infrastructure in May 2014, cybercriminals soon began spreading other dangerous forms of ransomware based on CryptoLocker’s successful model.
We began seeing CryptoWall in April 2014, along with another similar variant called CryptoDefense.
Since then, other copycats have emerged that have proved to be just as dangerous, some even borrowing the CryptoLocker name.
Recently we even saw crypto-ransomware that borrowed themes and imagery from the popular television series “Breaking Bad.”
The crooks have figured out some fiendish ways to get people to pay up: by making their illicit software “consumer-friendly” with easy-to-follow instructions on how to pay with bitcoins or other forms of untraceable e-payment, and offering “user support.”
Crypto-ransomware crooks have also figured out that they can earn their victim’s trust (more or less) by offering to decrypt one file for “free” – so you’ll know the crooks will follow through on their promise to decrypt the rest of your files once you pay them.
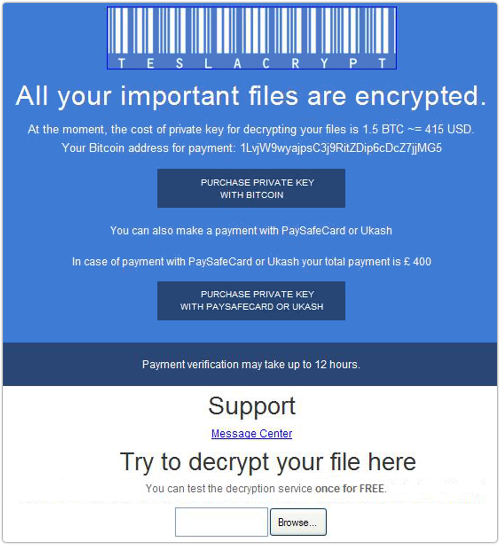
If the crooks have implemented the encryption process properly – and they often have – you’re left with a choice of losing your files, or paying for a copy of the decryption key.
It presents an ethical dilemma – one which Sophos security expert and fellow Naked Security writer Paul Ducklin captured well in his excellent post “Ransomware – should you pay?”
His spot-on and simple advice is summed up here:
- Don’t pay if you can possibly avoid it, even if it means some personal hassle.
- Take precautions today (e.g., backups, proactive anti-virus, web and email filtering) so that you avoid getting into a position where you ever need to pay.
We’ve got a lot more advice on dealing with ransomware in the Sophos Techknow podcast below.
(Audio player above not working? Download, or listen on Soundcloud.)
Image of money with ransom note courtesy of Shutterstock.com .

Laurence Marks
I can’t help thinking that better, pro-active antivirus software would solve this by either detecting the malware or simply detecting that all the user’s files were being re-written and nipping the process in the bud.
How about an AV popup which says
“Malware.exe is attempting to re-write My Documents\letter to Auntie.doc and other files. Press 1 to stop re-writing this file. Press 2 to stop re-writing all files. Press 3 to delete Malware.exe.”
This would at least limit the damage to 1 or 2 files.
If the AV gets good enough that these programs rarely succeed, we will see fewer of them.