
Thanks to Sandor Nemes of SophosLabs for the behind-the-scenes effort he put into this article.
Cryptoransomware isn’t a new topic any more, but it’s intriguing to look at what the crooks are up to these days.
As you probably know, ransomware – malware that locks you out of some or all of your digital stuff and demands money to let you back in – has two main flavours.
There’s lockscreen ransomware, where you can’t use your computer at all, except to stare at the lock screen or pay up the extortion fee to unlock.
You can usually get out of that sort of malware scrape on your own by rebooting (e.g. using Sophos Bootable Anti-Virus, which is Linux based) so that the lockscreen program never runs:
Can’t view the video here? Watch on YouTube. Can hear? Click on the Captions icon.
And there’s cryptoransomware, where your computer runs just fine but all your files are scrambled.
To unscramble them you need to buy a decryption key from the crooks.
Sometimes you can get out of trouble on your own, especially if you have a recent backup.
Then you can thumb your nose at the crooks, no matter how cleverly they’ve handed the encryption and decryption part.
If you don’t have a backup, and you aren’t prepared to pay (we salute your obduracy!), then you have two choices.
Either have to take it on the chin and lose your files, or hope that the crooks have made a programming blunder that lets you sidestep or crack their cryptography.
What you see
Usually, lockscreen ransomware tries to frighten you into paying up by using a police logo, often vaguely tailored to your own jurisdiction with ripped-off logos and web banners, and by asserting you’ve committed some kind of cybercrime.
The crime typically relates to pornography or copyright infringement, and the malware claims that the payment is a penalty that will settle the matter without criminal charges, much like when you pay a parking fine or minor speeding ticket.
Cryptoransomware, on the other hand, no longer bothers with the police pretence: the crooks are quite happy to remind you who you’re dealing with.
You’re not paying up because you think you might otherwise get into trouble for those pirated ROMs in your 1980s videogame emulator stash.
You’re paying up to get back your unsubmitted thesis/irreplacable kitten videos/records urgently needed by tax office/priceless 1980s videogame ROM stash.
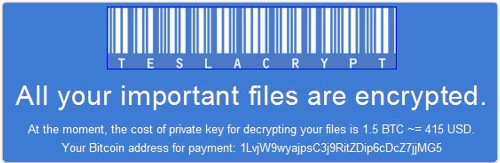
TeslaCrypt, for example, kept things really simple, stating unequivocally that:
And now, there’s PolloCrypt, for want of a better name (Sophos products block this one as Troj/LPoLock-A), where real-life cybercrooks are drawing on imagery from TV criminals:

As you can see, this sample was targeted at Australian users – AUD is the currency code for the Aussie Dollar – and has a two-tier payment plan.
The theory of two-tier payments seems to be that some users will back themselves to get out of trouble without paying, and then have to come back in a few days and admit defeat…
…so why not recover your data at a “discount” right away?
→ This malware doesn’t adapt itself at run time by working out where in the world you are, like most lockscreen ransomware. The warning screen is embedded in the malware itself as a base64-encoded BMP file, so that the malware will work even if it triggers while you are offline.
For those not up to speed on twenty-first century cult TV shows, Los Pollos Hermanos (The Chicken Brues) is a ficticious fast-food chain in the Southern border states of the USA that appeared in Breaking Bad.
Despite the unlikely-sounding basis of a high school chemistry teacher turned methamphetamine crook, Breaking Bad ended up with a Guinness World Record as the highest-rated TV series ever.
Seems like cybercrooks love their cult TV, too.
They’ve also learned to trade on the “reputation” created by CryptoLocker, the first widespread ransomware that really raked in money.
Early victims reluctantly reported that by paying up they did get their data back, and the CryptoLocker gang had built an online infratructure that could keep up with demand, so paying almost always worked.
Even some police departments ended up shopping for Bitcoins to recover data they’d neglected to back up. (We’re not sure what evidentiary value any of it would have had afterwards, but if the recovered data meant the difference between making payroll or not, we can understand those payments, for all that we disagree with them.)
The PolloCrypters are playing the same card:
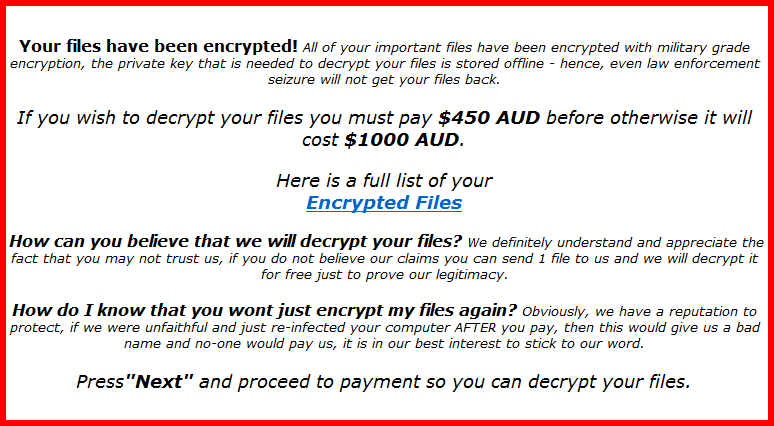
How can you believe that we will decrypt your files? We definitely understand and appreciate the fact that you may not trust us, if you do not believe our claims you can send 1 file to us and we will decrypt it for free just to prove our legitimacy.
How do I know that you wont just encrypt my files again? Obviously, we have a reputation to protect, if we were unfaithful and just re-infected your computer AFTER you pay, then this would give us a bad name and no-one would pay us, it is in our best interest to stick to our word.
They even go on provide a help screen explaining how to buy Bitcoins, but they warn you to keep quiet about the reason, lest some do-gooder tries to talk you out of paying up:
NOTE: When speaking to the Bitcoin exchangers its wise not to mention that you are paying for a ransom, they may refuse you.
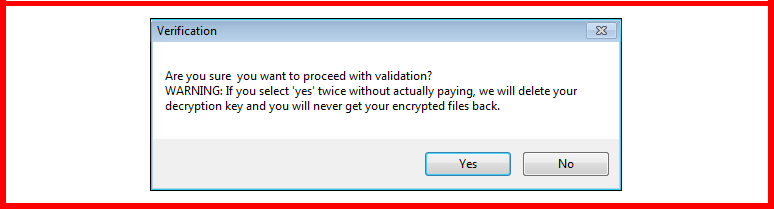
It’s not all sweetness and light, of course
WARNING: Only proceed to validation once you have paid. False attempts will cause destruction of your decryption key.
That’s reiterated in no uncertain terms when you go ahead to claim your decryption key:
The silver lining
In the Troj/LPoLock-A sample we examined in SophosLabs, the crooks didn’t get the cryptography right.
That means there is a fighting chance that you can recover your files by bypassing the private key component of the cryptographic equation, and not paying up.
However, because this malware is written in a high-level scripting language (Microsoft PowerShell), anyone who gets their hands on a copy of the code can fairly easily modify it to adapt its behaviour.
So don’t rely on cryptographic blunders to get out of trouble – take steps in advance to defend against ransomware and much more:
- Keep your anti-virus active and up to date. That means you’re more likely to block malware attacks proactively.
- Patch your operating system and applications promptly. Many attacks rely on exploiting bugs that are already fixed, so make yourself high-hanging fruit.
- Be suspicious of unexpected email attachments, no matter how relevant they may seem. That means you are less likely to double-click a malicious program by mistake.
- Make regular backups, and keep at least one offline. That protects you from data loss of all sorts, whether caused by ransomware, flood, fire, loss, theft and so on.
By the way, there is one thing you can learn from the crooks: encrypt your backups!
That way, if someone steals the USB hard disk with your tax returns on it, your data is just so much shredded cabbage as far as they’re concerned.
Free Virus Removal Tool
The Sophos Free Virus Removal Tool works alongside your existing anti-virus to find and get rid of any threats lurking on your computer.
Download and run it, wait for it to grab the very latest updates from Sophos, and then let it scan through memory and your hard disk. If it finds any threats, you can click a button to clean them up.

jet86
“there is a fighting chance that you can recover your files by bypassing the private key component of the cryptographic equation, and not paying up.”
Is it possible for you to elaborate on why this is possible and how it might work?
Paul Ducklin
You mean, perform a free code review for the crooks :-)
Anonymous
Los Pollos Hermanos – Breaking Bad
Rudy Cartassi
This is a Joke I would just format my PC reinstall and move on with life lol 1.5 BTC