Part of the mobile website of the Washington Post was compromised briefly on Thursday by the Syrian Electronic Army (SEA) hacker group, in an attack that redirected traffic to a site with anti-US and anti-media messages.
The SEA, known for its frequent targeting of media organizations including a 2013 hack of the Washington Post, publicized the cyberattack on Twitter, including screenshots of compromised webpages displaying the messages.
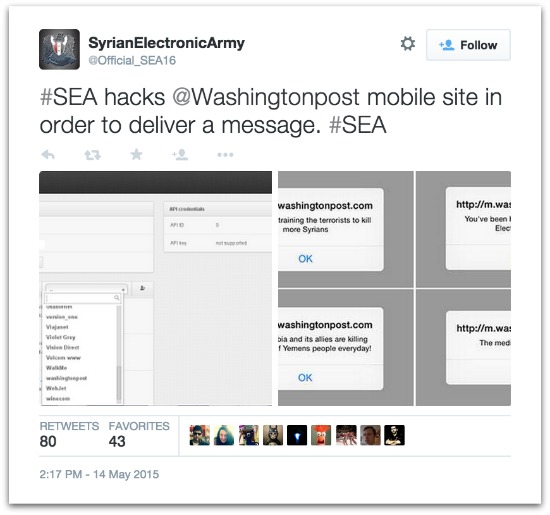
@Official_SEA16: #SEA hacks @Washingtonpost mobile site in order to deliver a message. #SEA
Washington Post chief information officer Shailesh Prakash confirmed the attack, which he said affected the mobile homepage and some section fronts on the mobile site, but he told CNN that “the situation has been resolved and no customer information was impacted.”
An anonymous member of the SEA told Motherboard that the hacking army breached the newspaper’s content delivery network, or CDN – a third-party network of servers used to serve web content including videos, advertisements and graphics.
The SEA member claimed to have compromised the CDN Instart Logic, and to have had access to other media sites before being kicked out of the network.
The SEA also posted on Twitter a screenshot seemingly showing a hacked Instart Logic account.
In a statement on its blog, Instart Logic confirmed on Thursday that it had been breached by a “sophisticated phishing attack.”
Through rapid deployment of our security protocols, we were able to quickly contain the breach, mitigate impact and maintain service. We determined that a sophisticated phishing attack exploited a vulnerability in a 3rd party corporate application that is not part of our service.
Although no customer data was stolen and the breach was quickly contained, it could have been much worse, security experts say.
Security researcher Kenn White documented the breach by using a laboratory PC to mimic a mobile device, as he continually visited the Washington Post mobile site to watch it unfold, reported Ars Technica.
 The SEA didn’t attempt to use control of the m.washingtonpost.com subdomain to inject malware to compromise site visitors, but the attackers could have done so, White said.
The SEA didn’t attempt to use control of the m.washingtonpost.com subdomain to inject malware to compromise site visitors, but the attackers could have done so, White said.
By controlling a domain name server (DNS) or a CDN, “an attacker controls your site, your code, your authentication cookies, your links. No bueno,” White told Motherboard.
That’s pretty much what Sophos security expert and Naked Security writer Chester Wisniewski said after the last time the SEA attacked the website of the Washington Post (along with CNN and other major media outlets).
Attackers with more malicious intent than the SEA could use similar techniques to infect “millions of internet users,” he wrote at the time.
Those attacks happened nearly two years ago, but Chet predicted they wouldn’t be going away anytime soon:
I don't imagine these types of attacks are going to go away anytime soon. Too many people are too trusting and too few websites offer mitigating technologies like two-factor authentication.
Unfortunately, he was right.
Image of Washington Post logos courtesy of 360b / Shutterstock.com. SEA logo via Twitter.

Leave a Reply