 Years before nude photos of celebrities flooded the internet in 2014’s Celebgate, commenters on 4chan and Reddit threads were offering to extract, in bulk, revealing photos from women’s private Photobucket accounts.
Years before nude photos of celebrities flooded the internet in 2014’s Celebgate, commenters on 4chan and Reddit threads were offering to extract, in bulk, revealing photos from women’s private Photobucket accounts.
It’s known as fusking: using a program to automate the collection of photo file from a website, a task made easy by obvious naming conventions, such as 1.jpg, 2.jpg, etc.
As BuzzFeed’s Katie Notopoulos wrote back in 2012, a privacy hole in Photobucket – an online photo service – had made it simple to figure out URLs that would enable fuskers to get guest access to see such private images.
In fact, that hole had been open for at least 5 years when she wrote about it.
It’s probably safe to assume it was open for at least two more years after that, given that two US men have been arrested for offering a service to facilitate stealing content out of private Photobucket photos between 2012 and 2014.
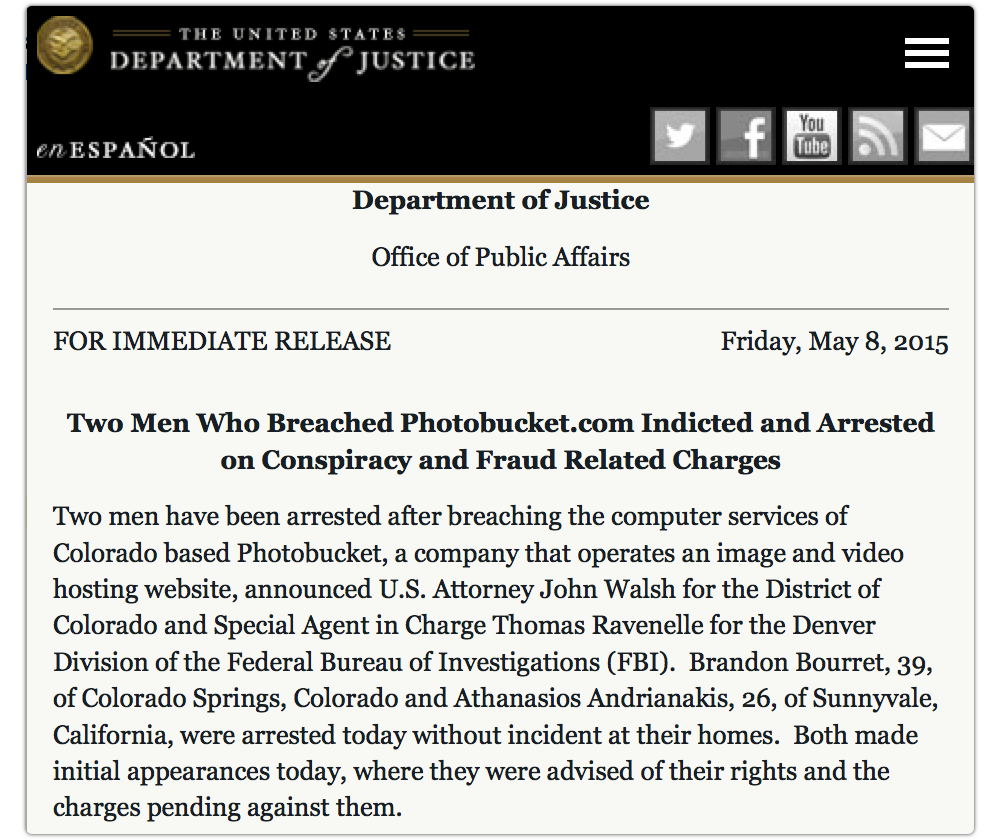
The Department of Justice announced on Friday that it had arrested Brandon Bourret, 39, of Colorado Springs, Colorado and Athanasios Andrianakis, 26, of Sunnyvale, California, for allegedly selling an application called “Photofucket” to clients who wanted to plunder Photobucket users’ private and password-protected information, images and videos.
(Don’t go to the website they created: it’s now offering a rotating variety of dicey links that we wouldn’t advise touching with a 10-foot pole.)
According to the indictment, Bourret and Andrianakis developed, marketed and sold the nastyware, which enabled viewers to circumvent the privacy settings of the image and video hosting website at Photobucket.com and to access and copy users’ content.
The pair allegedly used Photofucket to obtain guest passwords to access users’ password-protected albums and then handed the ill-gotten guest passwords out to paying customers.
As BuzzFeed explains it, the security hole was made possible by the way that Photobucket used to handle privacy levels, which differed from how Flickr or Facebook went about the task.
Photobucket had users set privacy levels at the album level, as opposed to setting it for each individual photo.
Photos inside albums marked as “Private” or “Password-protected” wouldn’t show up in searches or to people who browsed a user’s profile.
But you could still get to those photos with a direct URL. That way, users could send a direct link to share a given private photo with a friend, and that friend wouldn’t need a password to look at the content.
Then, she could forward that link to somebody else, who could send it along to a third party, and, well, you can see where that photo’s headed: to infinity and beyond!
…or, at least, if not to infinity, those URLs could be forwarded to somebody who got it into his head that he’d really like to see what else was in that album.
Since that recipient already had a URL for one of the photos in the album, plus the name of the Photobucket user, he or she could send those snippets of information on to a fusker app and have it guess what other URLs might pertain to that album and which might thereby lead to the private photos that the user didn’t want to reveal.
Engadget reports that in 2012, Photobucket announced that all new accounts would have their links scrambled by default, and existing users would also get the option to scramble links so that filenames couldn’t be easily guessed.
If the charges prove true, between July 2012 and July 2014, the two men racked up about 722 guest passwords, and their fusking program allegedly let them waltz into Photobucket.com password-protected albums without users’ permission.
The indictment lists evidence including emails the two men sent in which they discussed exploits, customer service messages to Photofucket buyers, and PayPal transfers to fund the operation.
Bourret and Andrianakis are each looking at up to five years in federal prison and up to a $250,000 fine for the conspiracy charge; the same again for a charge of computer fraud, aid and abet; and not more than 10 years in federal prison and up to a $250,000 fine per count for two counts of access device fraud.
What’s the lesson here? To not take naked photos? To not send them to other people or store them in online services? Or how about what Notopoulos suggested: don’t be nude, ever?
Well, that would help, and would also save time by collapsing bathing and laundering into one chore.
Crayminal
What?! How is this not Photobuckets problem? How about they take responsibility for their own stupidity?
“I dropped $20 on the street… and some damn criminal picked it up!” – PB
jet86
While it appears true that Photobucket didn’t implement very good security, that doesn’t make it legal or okay to intentionally bypass what security was there – even if it was relatively easy to do so.