 United Airlines stopped security expert Chris Roberts boarding one of its flights on Saturday, days after he had tweeted how the carrier’s onboard systems could be hacked.
United Airlines stopped security expert Chris Roberts boarding one of its flights on Saturday, days after he had tweeted how the carrier’s onboard systems could be hacked.
The researcher was stopped while attempting to board a flight from Colorado to San Francisco – where he is due to speak at the RSA Conference that begins today.
The One World Labs founder who was stopped by corporate security personnel at the gate, said United Airlines would not tell him why he had been barred from the flight, saying instead that it would send him a letter of explanation within the next two weeks.
Roberts had previously been removed by FBI agents from a United flight on Wednesday when he landed in New York, after jokingly tweeting that he could hack the airplane and get the oxygen masks to deploy:
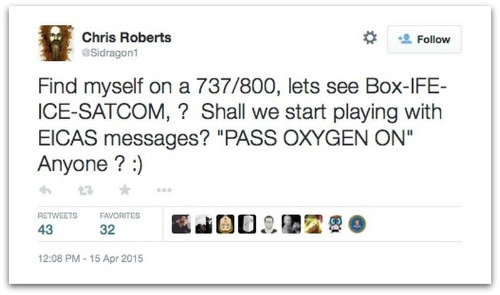
Find myself on a 737/800, lets see Box-IFE-ICE-SATCOM, ? Shall we start playing with EICAS messages? "PASS OXYGEN ON" Anyone ? :)
The inappropriate comment led to Roberts being questioned for several hours, as well as the confiscation of his laptop and other electronic devices, although his lawyer says he is yet to see a search warrant.
Speaking to The Associated Press, United Airlines spokesman Rahsaan Johnson said:
Given Mr. Roberts' claims regarding manipulating aircraft systems, we've decided it's in the best interest of our customers and crew members that he not be allowed to fly United.
However, we are confident our flight control systems could not be accessed through techniques he described.
When asked why United Airlines had an issue with Roberts, given that it was saying its systems were immune to the hacking techniques he had detailed, Johnson said:
We made this decision because Mr. Roberts has made comments about having tampered with aircraft equipment, which is a violation of United policy and something customers and crews shouldn't have to deal with.
Johnson also said that Roberts had been notified of United’s decision to ban him from flying prior to his arrival at the airport, explaining how the airline had called him several hours before the scheduled departure time.
Roberts’ lawyer, however, said the call was assumed to be a prank as the United representative failed to give their name or a number to call back on. When Roberts attempted to return the call via the phone number received on his mobile, he was connected to a hotel, leading him to assume that he was the victim of a prank.
Roberts had previously spoken to the FBI before his detention last week – two months ago he agreed to back off from his avionics research after a meeting at the bureau’s Denver office.
Since then, however, his work has featured on Fox News and CNN as both ran stories about the danger of hacking airplanes in flight, highlighting how Roberts was able to connect to a box under his seat on several occasions, allowing him to view data from the aircraft’s engines, fuel and flight-management systems.
The Security Ledger reports Roberts as saying he thought the authorities may have been reacting either to the increased media attention shone upon his work, or the fact that, after four years, there had still been little action in terms of addressing the vulnerabilities identified by himself and other researchers.
According to the Electronic Frontier Foundation (EFF), which is representing Roberts, he has now successfully made his way to San Francisco, via a last-minute booking with another airline.
The EFF said it has long been concerned about “knee-jerk” reactions to security researchers who are legitimately pointing out flaws in the hope that they will be fixed, adding that it hoped companies would:
Recognize that researchers who identify problems with their products in order to have them fixed are their allies.
As for whether or not an airplane can actually be hacked and, in a worst case scenario, plucked out of the sky by a tablet-wielding terrorist, last week saw a report from the US Government Accountability Office (GAO) on that very subject.
As Paul Ducklin wrote after analysing the 56-page report, the answer is a resounding… not likely.
“United Airlines Boeing 767-322ER” by Luis Argerich from Buenos Aires, Argentina – United B767-322ER. Licensed under CC BY 2.0 via Wikimedia Commons.

TG
“Roberts was able to connect to a box under his seat on several occasions, allowing him to view data from the aircraft’s engines, fuel and flight-management systems.”
Pen-testing without authorization = asking for trouble.
kadajawi
That may be, but do you really think airlines would give authorization? And I’d rather have a non-malicious white hat hack a plane and have them rethink their security systems, before someone with less… friendly motives does it.
t1nym1ght
This is a muddy subject. But the way you put it, (kadajawi) I have to fall on the side of supporting the unauthorized access.
Bureaucratic delay of “authorization” = head in the sand when it comes to security that literally holds thousands of lives in the balance.
I also agree with the below comment that Roberts should have kept his thoughts to himself and his fingers off twitter in this matter.
He probably had a couple of drinks on the flight. In my own (sometimes regrettable) experience, most regrettable content on the internet lands there with the aid of at least a modicum of alcohol.
I’d install a Breathalyzer on my laptop for twitter access sooner than I’d install one in my car…
loadtest
I thought avionics data was protected by a blue box marked “ethernet router/firewall” nearby seat 12B.
I wonder how well that’s working out if the allegation that he accessed that data from the comfort of his seat turns out substantial.
He’s blowing the whistle and getting it confiscated, whereas the GAO publishes demonstrably misleading information to create a false sense of security, and has the FBI with guns drawn to assure us that there’s nothing to see here.
The government needs a lot more depth in technical expertise if they’re ever going to be taken seriously in the security community. Notwithstanding the NSA, the only branch that has it but unfortunately only uses it offensively.
Tyler
PCI Requires that in-scope access ports not be placed in a common location. I wonder how long it is before we see a similar requirement of transportation systems.
Tom
Just because we have Twitter does not mean that you have to tell the world about every thought that comes into your head. Roberts should have saved the thought for a seminar at RSA instead of posting it.
Deramin
I disagree. He didn’t threaten anyone with harm. He stated a fact they didn’t want to hear. Free speech rights may not apply to companies, but it does make them jerks to react this way. And it makes me wonder what other critical safety oversights they’re burying. If I was in the marketing department of a rival airline, I’d be milking this for all it’s worth.
sg125
Sadly he is just wasting his time presenting at RSA the most ridiculous waste of time for any true security engineer. Market hype and drinks from the vendors, what a total waste of humanity
Phil Wade
I don’t understand why United were so stuffy – did they break his guitar too?
Deramin
Because intimidation is cheaper than fixing the issue.
Steve
I could get behind this guy, had he not done the twitty tweet. Makes him appear, IMHO, NOT to be a responsible security researcher but just a publicity-sucking twit.