 The US Government Accountability Office (GAO) publishes an eclectic range of documents at a fair clip.
The US Government Accountability Office (GAO) publishes an eclectic range of documents at a fair clip.
Indeed, the GAO’s website is an impressive source of documents zeroing in on a wide range of public service issues.
In just the past week, for example, we’ve had coverage of: how to deal with the implementation of the Helium Stewardship Act of 2013; the adoption of an incremental approach to Amphibious Combat Vehicle Acquisition; management challenges for the National Nuclear Security Administration; and gender equality, or the lack of it, in STEM research (Science, Technology, Engineering and Mathematics).
But no recent document has caused quite as much media stir as GAO-15-370, boldly entitled Air Traffic Control: FAA Needs a More Comprehensive Approach to Address Cybersecurity As Agency Transitions to NextGen.
NextGen, in case you are wondering, means, at least in this context, the Next Generation Air Transportation System, an extended project to update and improve the software, hardware and operational procedures surrounding air travel in the USA.
As a result of this report, published earlier this week, you’ve probably seen headlines all over the web giving prominence to concerns about hackers taking over planes, with various degrees of implied drama.
Wired had an eye-catching but reasonably non-commital headline:
Wired: In-flight Wi-Fi is a ‘direct link’ to hackers
NBC rowed the boat out a bit further, announcing that:
NBC: GAO Report Says Airplanes Are Vulnerable to Hacking
And Fox News fairly trumpeted a clear and present danger, telling us:
Fox: [H]ackers could bring down plane using passenger Wi-Fi
So, what’s the truth?
Could a hacker *really* bring down a plane from a mobile phone in seat 12C?
The answer is, “That’s very, very, unlikely.”
Nevertheless, hats off to the GAO for adopting the computer security principle that we informally refer to as never say never.
The complete document, at 56 pages, is actually much more interesting than you might at first think, and doesn’t actually ask you to imagine planes raining out of the sky thanks to tablet-wielding terrorists in tourist class.
But, as the document points out, the Federal Aviation Administration (FAA) is now ten years into the abovementioned NextGen modernisation programme.
A detailed review of where the FAA has got to, where it is going, and how it ought to get there was requested, and the GAO obliged.
The ten-year timeframe seems particularly pertinent given the recent news that a voting system in Virginia, USA – one that you would have been forgiven for calling comically insecure ten years ago – has only just been reviewed, found wanting and decommissioned.
Ironically, one of the serious insecurities in the Virginia Comedy Voting Machine story was Wi-Fi related: the reliance on Wired Equivalent Privacy (WEP), a cryptographic protocol that seemed OK at first, but was soon found to be fundamentally flawed and automatically crackable in minutes.
Of course, on many modern airliners, passengers don’t need to hack into the Wi-Fi network at all, because it’s offered as a service you’re encouraged to connect to, albeit at the same sort of cost as a month’s worth of bandwidth on the ground.
In short, Wired’s headline pointing out that “in-flight Wi-Fi is a ‘direct link’ to hackers” is unexceptionable; what isn’t so certain is whether in-flight Wi-Fi is also a transitive ‘direct link’ to the control systems of the plane.
If that were so, perhaps hackers really could cause seriously scary situations, like unauthorised barrel rolls, right from their seats?
But with two completely separate networks for in-flight entertainment and for aircraft control, you might reasonably be willing to say “never” after all…
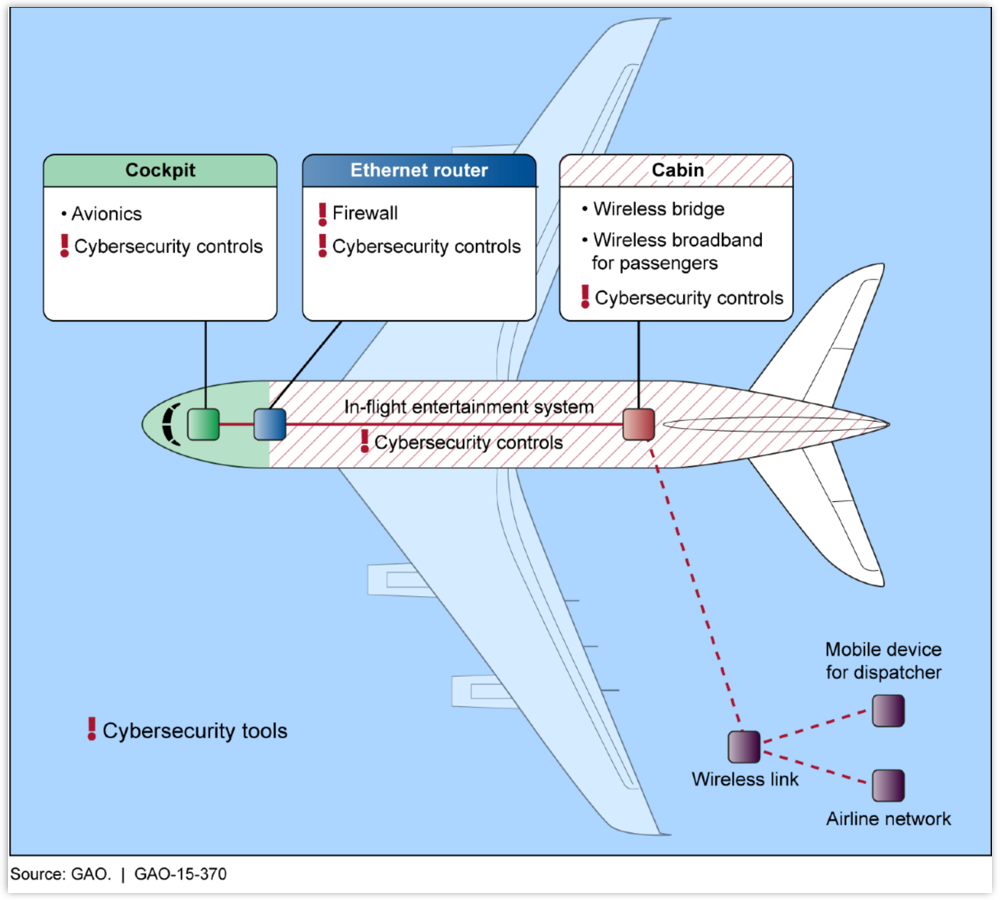
…at least, until you get to Page 23 of the GAO’s report, where you will find this network diagram:
I’m not alarmed – I have no doubt that occasional air travel is significantly safer than my daily rush-hour bicycle commute, which brings a whole new dimension to Warbiking – but that particular diagram did make me alert.
I don’t know about you, but a single blue box labelled “ethernet router” between seat 12C and the pointy end of the plane certainly gives me pause for thought.
When the GAO next produces a Cybersecurity in the NextGen Project report, I’d be a lot happier to see two separate red lines providing network service inside the plane.
Divide and conquer: it really does work!
Image of plane weaving through clouds courtesy of Shutterstock.


Guy
Let’s hope it’s not a Belkin or D-Link…
Paul Ducklin
That’s a bit unfair :-)
What about Sercomm?
https://nakedsecurity.sophos.com/2014/01/03/gaping-admin-access-holes-found-in-soho-routers-from-linksys-netgear-and-others/
Or Sercomm again?
https://nakedsecurity.sophos.com/2014/04/23/the-soho-router-backdoor-that-was-fixed-by-hiding-it-behind-another-backdoor/
Linksys?
https://nakedsecurity.sophos.com/2013/04/11/anatomy-of-an-exploit-linksys-router-remote-password-change-hole/
InnGate?
https://nakedsecurity.sophos.com/2015/03/30/hotel-wi-fi-router-security-hole-will-this-be-the-ultimate-pwnie-award-winning-bug-for-2015/
Pirelli?
https://nakedsecurity.sophos.com/2015/01/15/ouch-home-router-security-bypass-actually-means-no-security-at-all/
MikeP_UK
Aircraft are designed to be efficient on fuel usage, as much as possible anyway, and weight is a significant factor in that goal. So it is possible that significant weight can be saved by sharing the wiring used for the computerised flight control systems with the WiFi feeds offered to passengers, otherwise many more miles of cabling will be needed with the consequent weight penalty. If they are sharing the same wiring, then the potential exists for transference from one to the other, despite firewalls – they are not perfect. The possibility of EMI/crosstalk having an effect on both systems should not be ignored either, most aircraft wiring is unscreened – again for weight saving. It’s worth noting that screen Cat6 cabling is significantly heavier (per unit length) than unscreened Cat5.
That then raises the chances that some nefarious person could find their way into the flight control systems, perhaps seeing it as both a game and a challenge. If anyone does succeed then the flight itself is at risk as are all on board plus those on the ground below or nearly under the flightpath.
So who is going to pay for the extra fuel needed to allow airliners to have physically separate well screened systems for flight control and internet/entertainment systems? Ultimately, it’s the passengers who pay but the regulators need to take note of the risk potential and have cognisance of whet they need to regulate for to safeguard the flying public and those on the ground.
Sg125
Those darn WIFI wires
Samir
it baffles me why the avionics section is even networked with the rest in the first place
Keith
I would be less concerned about a person on the airplane discovering a way to get into the airplane navigation system than I would be about a person on the ground doing it.
The document says “information systems that interoperate and share data throughout FAA’s operations and those of its aviation partners.” Aviation is going from a ground-based point-to-point system to one where the airplane talks, using wireless IP, to satellites, towers, and other airplanes. This will conceivably allow a person on the ground to hammer away on the network until access is gained. The person in 12C only has a few hours to work at it.
I’m especially concerned about that “aviation partners” comment. That would seem to mean that every company, whoever they may be, will have to have the same level of security to keep the system safe. How many security breaches occur because a trusted partner didn’t have the security processes they should have?
Anonymous
Don’t be alarmed…… there are “Cybersecurity Controls” everywherez to keep you safe.
Paul Ducklin
With exclamation! points! to make them sturdier!
R0B_ROD
When we learn that those who create problems already have the solutions we can get our heads out of our 4K-VirtualTunnelReality and realize that “criminals” dont exist. “Terrorists” are an illusion of BigBrother and G-men.
Wake up folks.
Anonymous
So, before was the toothpaste that was banned inside the passengers area. Now, smartphones, tablets and laptops if they pose a threat.