 We’ve written before about the “security gap” between desktop and mobile apps.
We’ve written before about the “security gap” between desktop and mobile apps.
More than a year ago, for instance, we covered a security report by researcher Ariel Sanchez of IOActive, who examined the behaviour of mobile banking apps.
He ran 40 different iOS banking apps – the apps officially endorsed and supported by more than 60 banks in 20 countries.
He wanted to know if they offered an experience as safe and secure as using your regular desktop browser.
They did not.
Most worryingly, 40% of the apps he tested didn’t do HTTPS correctly.
The benefits of HTTPS
You’ll often hear HTTPS (short for “Secure HTTP,” which relies on a protocol called TLS, short for Transport Layer Security) endorsed primarily because it uses encryption.
That provides confidentiality.
Wi-Fi-sniffing crooks sitting somewhere near you in the coffee shop, or intelligence agents plugged into a network rack in the middle of a server room at your ISP, can see that you are talking to your bank.
But they can’t tell what you’re talking about: the contents of your HTTP session are just so much shredded cabbage to their eyes.
That’s good, because it keeps things like your bank balance and your payment details secret.
However, especially when it comes to online banking, encryption isn’t the only important feature of HTTPS.
TLS also provides authentication, which means you can be sure, or sure enough, that you really have connected to your bank.
If TLS provided encryption only, you might – if you weren’t careful, and perhaps even if you were – end up conducting a secret conversation directly with a crook.
→ TLS also provides integrity, which verifies that your traffic hasn’t been altered along the way. Even if a crook doesn’t know what you’re saying, he could put a dangerous spanner in the works by changing the data, knowing that it would decrypt incorrectly and perhaps cause problems at the other end.
Criticism of HTTPS
You’ll hear people criticising TLS authentication.
That’s because it’s based on the concept of a chain of trust consisting of digital signatures, which can end up looking both complex and confusing, like this:
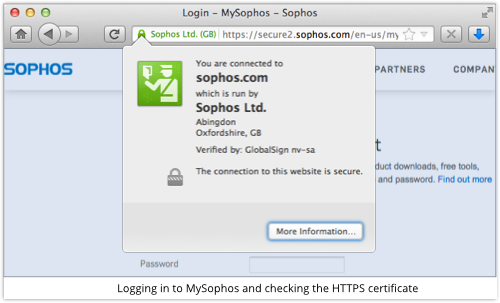
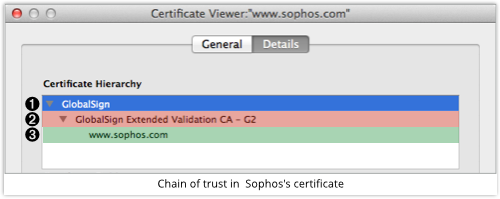
Here, you can see Sophos Ltd vouching for the website secure2.sophos.com; GlobalSign’s Extended Validation CA (Certificate Authority) vouching for Sophos; and GlobalSign vouching again for its own Extended Validation CA.
Part of the confusion is that you have to look somewhere else to find out who vouches for GlobalSign.
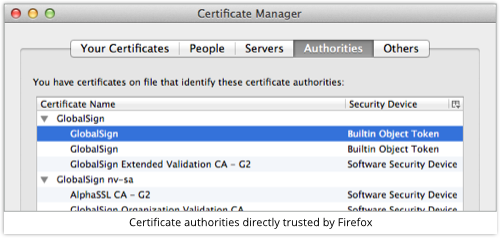
In this case (we’re using Firefox), it is Firefox that closes the chain of trust, because the browser itself contains a list of built-in trusted signers, including GlobalSign:
Tricking the user
For all the complaints about the visual complexity of the TLS chain of trust, it does make it easy for your browser to spot obvious fraud.
If I redirect you to my fake secure2.sophos.com portal, I have to do one of three things to trick you into using it in place of the real thing:
- Bribe or subvert a CA into signing me a fake certificate in Sophos’s name.
- Use a certificate I signed myself, and hope you don’t notice.
- Use plain old HTTP, and hope you don’t notice.
If I use Trick 2, most browsers will pop up a rather obvious warning, like these ones:
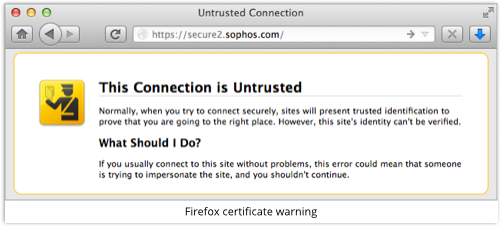
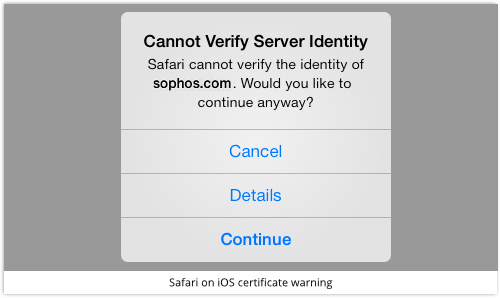
Critics of TLS see this as a problem, because each browser has a different way of warning you; most warnings can easily be bypassed; and even legitimate sites sometimes throw up warnings that you need to bypass, which sets a poor standard.
But at least you get a warning, so you can usually spot Trick 2 if you really want.
Mobile apps fall short
That’s where Ariel Sanchez’s report comes in: 40% of the banking apps he tried out at the end of 2013 actually supported Trick 2 on behalf of the crooks.
You could feed those apps a fake, self-signed certificate claiming to identify your website as anything you liked, and they would blindly accept it.
In other words, the crook didn’t have to hope you wouldn’t notice his HTTPS subterfuge, because you couldn’t notice it!
You’d have hoped things would get better over the past year, but some mainstream mobile apps are still showing signs of a “security gap.”
Dutch security company Securify, for example, recently tested Pinterest’s iOS app, as well as Microsoft’s Yammer client for the same platform.
The result?
Those apps didn’t give security warnings about fake certificates.
Worse still, those apps send your password to the server when you first log in, assuming that HTTPS encryption will keep it safe from prying eyes.
But if the server you are “logging into” is a fake one, and you don’t notice because there is no certificate warning, that HTTPS encryption will serve only to deliver the password securely into the hands of a crook.
What to do?
• Update Pinterest or Yammer on iOS right away if you haven’t already. This problem is fixed in the latest versions.
• Change your password on those networks, just in case. A “man-in-the-middle” attacker could already have seen your password in transit.
You might also want to consider sticking to your browser for activities like social networking, online banking and other transactions, at least until the security industry reaches a consensus that this “security gap” has closed.
Sure, mobile browsers can be hard to use.
But they are much more likely, at least in 2015, to protect you from Trick 2 above.

Tattooed Mummy
How does this affect sign in via Google facebook etc on pinterest etc? Should I change all the passwords? Not sure how much of the authorisation chain is seen or affected (did that make sense?)
Paul Ducklin
Gotcha…and I must admit, I don’t know. Chester?
Chester Wisniewski
Google, Facebook, Twitter, etc use OAuth and do the authentication directly with you and pass you back to Pinterest. At worst it might have allowed your OAuth token for Pinterest to be compromised.
To be on the safe side you could revoke Pinterest’s permission from your Google/Facebook/Twitter account and re-authorize it to get a new token. I don’t know where it is precisely on each service, but it is usually referred to as “authorized apps” or something along those lines.
David
Is there any way for a mug punter such as myself to verify if my bank’s mobile app (or any app for that matter) is secure? When you first wrote about Ariel’s report (which doesn’t name names) I emailed my bank with a link to your article, but of course received no reply. Consequently, I follow your advice and just use the browser, but am curious nonetheless.
Paul Ducklin
There are fairly easy ways to check (things you can do yourself, at home), but I can’t think of a really easy way that I could explain in a comment (or even in a sidebar in the article above).
Maybe an article showing what to try :-)
The lack of response from your bank is a bit shabby. It’s an important security-related question from a customer. How about popping into your branch and asking face to face for the question to be escalated? More and more people will surely want to know, so they might as well get their answer ready now :-)