 Mozilla recently published its scheduled release of Firefox 37.0.
Mozilla recently published its scheduled release of Firefox 37.0.
That was a pre-planned “fortytwosday” release, as we’ve taken to calling them.
They come out on Tuesdays, just like patches from Microsoft and Adobe, but rather than appearing on the same Tuesday every month, they come out every six weeks.
That means the updates wander through the calendar months, lunar style, over the course of a year.
And, yes, this is a nod to Douglas Adams and the HHGttG, because six weeks just happens to be 42 days.
Firefox 37.0 introduced support for HTTP/2, the not-quite-finalised-yet update to the venerable HTTP protocol.
Currently, almost all web servers speak a dialect of HTTP known as HTTP/1.1, first standardised as RFC2068 in January 1997.
That standard was updated by RFC2616 in June 1999, and you’ll still hear “RFC2616” and “HTTP/1.1” used synonymously, even though the official specification was updated in June 2014.
Following the truism that “nothing ever gets simpler,” RFC2616 was obsoleted by not one, but six separate standards documents running from RFC7230 to RFC7235:
But HTTP/2 is coming, some time soon, and one of the things it offers is a feature called HTTP Alternative Services, abbreviated to Alt-Svc.
At the moment, if you want to redirect vistors to your website somewhere else, you send a special sort of HTTP reply to tell them to do just that.
As we do, for example, if you browse to http://nakedsecurity.sophos.com/:
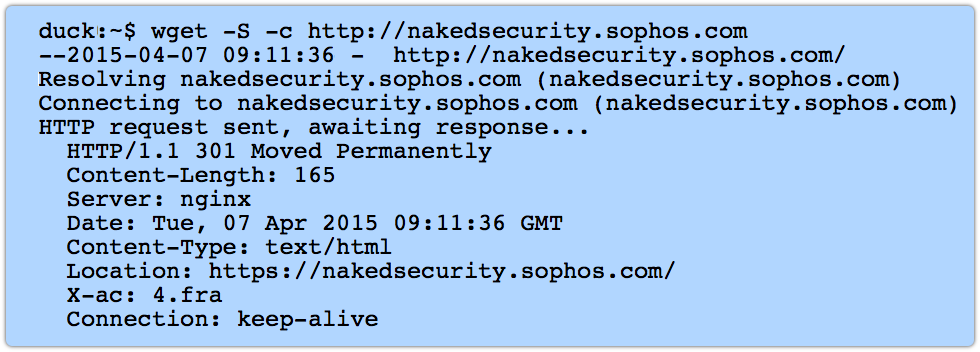
We tell your browser to try again, connecting instead via HTTPS, the secure version of HTTP.
We use HTTPS because you get encryption, which means no-one sitting nearby in the coffee shop can see what you’re reading.
Even though the content of our website isn’t secret, there’s something appealing about not letting other people get an unnecessary sniff at your interests.
Additionally, we use HTTPS because you get authentication, which means you can be pretty certain that the security advice you’re getting came from us, and not some shabby imposter who wants to use our good name to talk you into bad practices.
With HTTP/2, Alternative Services deal with redirections and alternative ways to get to your site.
So, with a special header in the reply from your web server, you can cleanly deal with all sorts of redirects, such as moving visitors to temporary servers during maintenance, or shifting unencrypted traffic over to an encrypted connection instead.
Unfortunately, Mozilla’s brand-new support for HTTP/2 included a brand-new bug, documented in Mozilla Foundation Security Advisory 2015-44.
A security researcher worked out a way to bypass HTTPS certificate validation if a web server redirected you via the Alt-Svc header.
That’s very bad, and here’s why.
If you had a phishing site that pretended to be yourbank.example, and handled HTTP connections directly, you’d have difficulty presenting a legitimate-looking connection.
You’d either have to use HTTP and hope your victims wouldn’t notice the lack of a secure connection, or use HTTPS and hope they wouldn’t notice the certificate warnings telling them that you probably weren’t the lawful owner and operator of the yourbank.example domain.
Some users would probably end up getting tricked anyway, but well-informed users ought to spot the ruse at once, and remove themselves from harm’s way.
But this Alt-Svc bug could be used by crooks to redirect victims to a secure connection (thus making the connection “look right”) without producing a certificate warning to say that the site looked like an imposter.
In other words, even a well-informed user might accept a phishing site as the real thing.
The good news is that the bug was quickly found, and just as quickly dealt with, with Firefox 37.0.1 coming out over the Easter weekend. (Technically, the bug wasn’t fixed, just turned off along with Alternate Services support.)
Even though HTTP/2 isn’t yet finalised, and very few legitimate servers actually use it in real life, it is already supported by popular web servers such as Apache and Nginx, and by Microsoft’s IIS (Internet Information Services) in Windows 10 Preview.
So crooks who want to use HTTP/2, perhaps in the hope of exploiting bugs in the comparatively new code that supports it in the major browsers, are free to do so.
In short, if you’re a Firefox user, make sure you’ve got 37.0.1.
→ Go to the About Firefox menu item to force an update check. Use the [Show Update History] button on the Preferences | Advanced | Update page to check whether you’ve got the latest version.

Goldor0ck
According to https://www.mozilla.org/en-US/firefox/37.0.1/releasenotes/, 37.0.1 did not fix the bug, but rather disabled Alt-Svc support.
In short, Alt-Svc is not available yet…
Paul Ducklin
Good point. I adapted the text to make this clearer…thanks.
Justin Credible
IIS stands for Internet Information Services (not servers)
Paul Ducklin
Fixed, thanks.
MikeP_UK
It’s a shame that despite the plea by Sophos to make sure that we use secure services shown by having the https and the padlock symbol in the address header line, this page does not! It has a simple exclamation mark in a triangle and clicking on that states “This website does not supply identity information.” despite using the https version. So we have no idea whether this is a secure site or not – I hope it is.
Paul Ducklin
I don’t see that…I am using FF 37.0.1 on OS X. I get the green HTTPS indicator and “Sophos Ltd” as the owner of the domain. Do you have some sort of web filtering going on there, do you think?
Malcolm
Mike: Are you inside a corporate network which uses an UTM? I am, and as a consequence I don’t see the padlock. For some reason the chaps at InfoSec like to see all the traffic coming in and out :).
Max
I strongly recommend to avoid using the word “crook”; since this word has several uses, formal and informal, it tends to be taken lightly. Those people who are breaking into the private information of others are NOT different than those who break into houses, with weapons, and robe and steal others’ properties. Please change that ‘crook’ word; use the correct word: CRIMINALS. Thanks for your consideration to make sure calling things properly.
Paul Ducklin
I hear you, but I don’t hear anything light in the word “crook.” Perhaps this a US versus British English thing?
To me, the word “crook” has no soft meaning. Someone who is “crooked” is criminal and corrupt; someone who is a crook is engaged in dishonest, criminal activities, plain and simple. After all, you’ll see the word “criminal” used lightly and metaphorically, too, to describe things like bad umpiring decisions (“we was robbed!”).
As my dictionary says, “crook: [informal] a person who is dishonest or a criminal.” (Both my British and US lexicons say the same thing.)
David K. M. Klaus
“Crook” is occasionally used jocularly, whereas “criminal” generally is not, and to that extent it seems to me that Max has made a good point.