 A bit of a brouhaha has broken out about a “Black Box” that can brute force your iPhone PIN by trying every possible combination, from 00..00 to 99..99.
A bit of a brouhaha has broken out about a “Black Box” that can brute force your iPhone PIN by trying every possible combination, from 00..00 to 99..99.
Robotic “PIN typing” devices are not new, but this one doesn’t press on-screen buttons.
Apparently, it uses a USB connection to inject the screen taps virtually, thus simplifying operation.
As you know, an iPhone keeps a count of how many wrong PINs have been entered, in case you have turned on the Erase Data option on the Settings | Touch ID & Passcode screen.
That’s a highly-recommended option, because it wipes your device after 10 passcode mistakes.
Even if you only set a 4-digit PIN, that gives a crook who steals your phone just a 10 in 10,000 chance, or 0.1%, of guessing your unlock code in time.
But this Black Box has a trick up its cable.
Apparently, the device uses a light sensor to work out, from the change in screen intensity, when it has got the right PIN.
In other words, it also knows when it gets the PIN wrong, as it will most of the time, so it can kill the power to your iPhone when that happens.
→ If the device couldn’t tell when it had guessed correctly, it would end up rebooting even after finding the right PIN, so it would never know when it had cracked the unlock code.
And the power-down happens quickly enough (it seems you need to open up the iPhone and bypass the battery so you can power the device entirely via the USB cable) that your iPhone doesn’t have time to subtract one from the “PIN guesses remaining” counter stored on the device.
So, when the Black Box reboots and is asked for the passcode once again, the Black Box still has 10 guesses left.
Fixing this in iOS itself seems easy enough: instead of counting down after each PIN failure until the 10th bad PIN has been entered, just count up before each PIN entry until the 11th PIN entry is requested.
(This fix may, indeed, be in iOS 8.2. Sadly for the author of the original work, the iOS 8.2 update came out almost immediately after he’d done his tests, and he hasn’t yet had a chance to repeat them)
Of course, there’s a easy way to work around this problem even in the absence of an iOS-level fix.
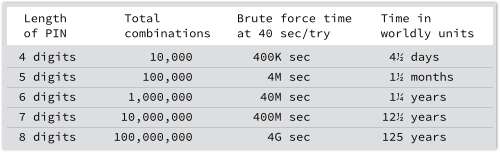
With a full power-cycle needed to suppress the “PIN guesses remaining” countdown, each guess takes a long time: up to 40 seconds, apparently.
That’s close to five days to try all 10,000 four-digit PINs.
But a PIN of just 7 digits would take more than 12 years to crack for sure.
So, choose a PIN longer than 4 digits!
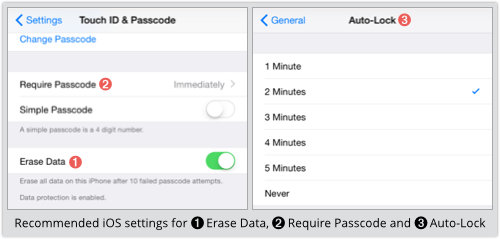
Our recommendations
- Turn on the Erase Data option to wipe your phone after 10 tries. You are unlikely to do it yourself by mistake.
- Go longer than the 4-digit minimum passcode. Every extra digit makes a brute force attack 10 times less likely to succeed.
- Set Require Passcode to “Immediately.” That means that whenever you see the lockscreen, you know the passcode is activated.
- Choose the shortest Auto-Lock time you can. The shorter you go, the safer you are.
- Consider using a Mobile Device Management product to require these settings at work. If your users complain, remind them you are improving security in their personal digital life, too.



Guy
I have a 16 digit PIN for my Android. I’ve actually got quite fast a typing it accurately and can normally get into my phone on the first or second attempt these days, as opposed to the fifth or sixth that it used to take (-:
I know some people don’t like Android’s arbitrary 16 digit limit on PIN length, and I hear it. At least, though, you can choose a between PINs, patterns and passwords, so if you wanted a 17 digit PIN, you could make it a numeric password.
(What is it with Geeks and the letter P? PINs, patterns, passwords, Perl, PHP, Python…)
Chris
Protocol, Rasp Pi, privacy, piracy…
I feel like we have enough to re-write Daft Punk’s “Technologic” with all tech P-words.
Paul Ducklin
I’m pretty sure Android’s limit is 17, for both digit-only PINs and alphanumeric passwords. Microsoft (e.g. on Outlook.com) has 16.
As to, “Why?”
Who knows…
Anonymous
Using a 16 digit PIN inconveniences you and offers no real security. All it takes it for somebody to brute force it using from ROM and my calculations are that it could be cracked in 1.85 minutes using cloud computing or 1.29 days using a slow, offline computer.
Paul Ducklin
To brute-force a 16-digit PIN (i.e. try every possibility) requires 1016 attempts, which is ten thousand million million.
I’m not aware of any “from ROM” attacks, so you’d have to try each PIN on the device itself. The cloud is irrelevant because you can only try one PIN at a time…but even with 1.29 days at your disposal, you’d still have to try about 100 gigaPINs per second.
Ahhhhhhhhhhhhh, darn. I just got trolled, didn’t I?
Dan
I think OP meant an offline brute-force of a dumped ROM. Eg. attaching JTAG’s and sucking out the ROM image and cracking the hash value of the PIN.. But to be honest, i wouldn’t be surprised if the PIN isn’t even hashed.
Paul Ducklin
Good luck with that. Apple has done a pretty good job of stopping you getting at whatever you feel like inside an iPhone, even if it’s yours and you know all the passwords to get in officially…one reason jailbreaking takes such serious effort. Maybe it takes 1.29 days to crack the PIN _after you have spent 12.9 years getting the hash to attack_ :-)
I’ll stick to my supposition…I got trolled there.
Graham Cluley
I believe the IP Box still works on iOS 8.2
The add-on board cuts power after every passcode five attempts. Slow, but works.
Andrew Ludgate
I ran the math a while ago and realized that 8 digits is more than enough. However, while I follow all the other advice on here, I have my device set for remote wipe but not for wipe after 10 tries.
Why?
I’ve got children. They regularly find the device and go way past the 10 attempts, just for the thrill of punching a “code” into something.
So if you’ve got kids, you may want to think twice about enabling that feature — it could result in having to restore your phone at awkward times.
But please… everyone else do it; if crooks assume the phone will wipe after 10 tries, that’s almost as good as every phone actually doing so.
Bruce Kay
I have a long alpha-numeric passphrase set for my iPhone. It takes too long to type, so I use TouchID for routine use. I only need to enter my long passphrase when I reboot. If they crack TouchID, I’m back to shorter PINs. Otherwise, this works very well because it’s very convenient.
Josh
Touch id was cracked almost as soon as it came out, a bit of woodglue and a finger was all it took, they also then lifted the prints and re-made them and were still able to get past it.
Paul Ducklin
Here are some fun stories we wrote on how it all unfolded…
The challenge:
https://nakedsecurity.sophos.com/2013/09/20/win-bitcoins-booze-and-cash-be-the-first-to-crack-the-iphones-touch-id-fingerprint-sensor/
The victory…
https://nakedsecurity.sophos.com/2013/09/22/chaos-computer-club-claims-to-have-cracked-the-iphone-5s-fingerprint-sensor/
Redux with Samsung Android device:
https://nakedsecurity.sophos.com/2014/04/17/samsung-galaxy-s5-fingerprint-hacked-iphone-5s-all-over-again/
Laurence Marks
Duck wrote: “Fixing this in iOS itself seems easy enough: instead of counting down after each PIN failure until the 10th bad PIN has been entered, just count up before each PIN entry until the 11th PIN entry is requested.”
It doesn’t matter whether you increment or decrement. The key is to make it a pre-increment or pre-decrement rather than a post-increment or post-decrement. In C that’s ++PassTry or –PassTry, not PassTry++ or PassTry–.
On the zeroth (or tenth) pass, you allow the attempt. When you come back for the eleventh attempt you fail the test.
Paul Ducklin
Errr, I *think* I made that perfectly clear. In fact, modulo the “up” and “down”, you are simply repeating what I said, but with a bit of coder’s jargon thrown in. (Perhaps I shouldn’t have added the “up” and “down”, which were just to make it read better. They obviously turned into red herrings.)
As you say, it’s the *before* or *after* that matters.
Strictly speaking, you can log the failure before or after the PIN has been entered – in this case, all that really matters is that the increment-or-decrement happens *before you signal whether it was a pass or a fail*. (The simplest safe way IMO is to do it before the PIN is even entered, which is why I suggested it that way.)
Don Miller
I can see this as a request from Law Enforcement to get around iPhone encryption when a suspect is uncooperative about complying with a search warrant to search an iPhone
Harp
I use a short passphrase on mine – easy to type, remember and much longer to crack.
J T
I use a 12 character alpha-numeric-symbol passphrase on my IOS devices. It’s a pain to type in because of the multiple shifts/numeric switches, but I’ve never been in an extreme hurry to get into my phone other than to answer a call, which doesn’t require me to unlock it.
Abbalah
I have a 9 character PIN and enabled the wipe-after-10-guesses feature. Everything worked fine for a while until someone on my robotics team took my phone and tried to guess the PIN. Apparently, reading the little pop-up warning is too hard. I lost everything but my contacts (I had been running backups but I guess they weren’t going through). I have since disabled that feature.
Paul Ducklin
Shouldn’t that person be in serious trouble, assuming this is in a work environment? He or she shouldn’t be fiddling with your phone at all without your permission, let alone deliberately wiping it as if that were great sport.
Abbalah
It’s a school environment but I’m sure something would have been done had I reported the incident. I normally would have but I’m an idiot that wants to avoid any situation that may result in a confrontation.