A bit of a brouhaha has broken out about a “Black Box” that can brute force your iPhone PIN by trying every possible combination, from 00..00 to 99..99.
A bit of a brouhaha has broken out about a “Black Box” that can brute force your iPhone PIN by trying every possible combination, from 00..00 to 99..99.
Robotic “PIN typing” devices are not new, but this one doesn’t press on-screen buttons.
Apparently, it uses a USB connection to inject the screen taps virtually, thus simplifying operation.
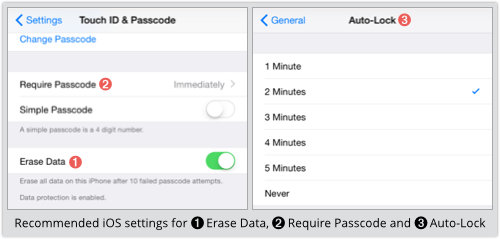
As you know, an iPhone keeps a count of how many wrong PINs have been entered, in case you have turned on the Erase Data option on the Settings | Touch ID & Passcode screen.
That’s a highly-recommended option, because it wipes your device after 10 passcode mistakes.
Even if you only set a 4-digit PIN, that gives a crook who steals your phone just a 10 in 10,000 chance, or 0.1%, of guessing your unlock code in time.
But this Black Box has a trick up its cable.
Apparently, the device uses a light sensor to work out, from the change in screen intensity, when it has got the right PIN.
In other words, it also knows when it gets the PIN wrong, as it will most of the time, so it can kill the power to your iPhone when that happens.
→ If the device couldn’t tell when it had guessed correctly, it would end up rebooting even after finding the right PIN, so it would never know when it had cracked the unlock code.
And the power-down happens quickly enough (it seems you need to open up the iPhone and bypass the battery so you can power the device entirely via the USB cable) that your iPhone doesn’t have time to subtract one from the “PIN guesses remaining” counter stored on the device.
So, when the Black Box reboots and is asked for the passcode once again, the Black Box still has 10 guesses left.
Fixing this in iOS itself seems easy enough: instead of counting down after each PIN failure until the 10th bad PIN has been entered, just count up before each PIN entry until the 11th PIN entry is requested.
(This fix may, indeed, be in iOS 8.2. Sadly for the author of the original work, the iOS 8.2 update came out almost immediately after he’d done his tests, and he hasn’t yet had a chance to repeat them)
Of course, there’s a easy way to work around this problem even in the absence of an iOS-level fix.
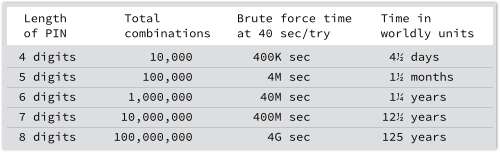
With a full power-cycle needed to suppress the “PIN guesses remaining” countdown, each guess takes a long time: up to 40 seconds, apparently.
That’s close to five days to try all 10,000 four-digit PINs.
But a PIN of just 7 digits would take more than 12 years to crack for sure.
So, choose a PIN longer than 4 digits!
Our recommendations
- Turn on the Erase Data option to wipe your phone after 10 tries. You are unlikely to do it yourself by mistake.
- Go longer than the 4-digit minimum passcode. Every extra digit makes a brute force attack 10 times less likely to succeed.
- Set Require Passcode to “Immediately.” That means that whenever you see the lockscreen, you know the passcode is activated.
- Choose the shortest Auto-Lock time you can. The shorter you go, the safer you are.
- Consider using a Mobile Device Management product to require these settings at work. If your users complain, remind them you are improving security in their personal digital life, too.