 Google is quite the collector when it comes to data.
Google is quite the collector when it comes to data.
As we well know, sometimes the Mountain View juggernaut sometimes drives right to the brink of controversy, and occasionally right over it.
Nevertheless, for all the dodgy Wi-Fi sniffing and sneaky pharmaceutical promotion, the ad giant has typically been considered a safe pair of hands when it comes to data leakage.
Google may hoover up more about you than you know about yourself, but it hasn’t had any major breach or data spillage moments like Target, Adobe or Sony.
There were some admittedly amateur-time coding flaws revealed in Android in 2014, but as far as network security goes, Google has set itself up as a bit of a leader.
For example, there was the switch to HTTPS and nothing but for Gmail, and the company’s timely blanket shift to 2048-bit RSA keys.
And during a fierce internet freedom dispute in Turkey in 2014, Google’s free, unregulated, public DNS servers (at 8.8.8.8 and 8.8.4.4) became the special favourites of Turkish activists.
But even Google can make mistakes, as network security expert group Talos recently noticed.
In this case, the result was apparently a large-scale leak of data that Google had promised to keep to itself.
The leakage had to do with what’s known as WHOIS data, the information about who’s who on the internet.
When you register a domain name to give yourself a human-friendly location in the internet universe, most countries require you to say who you are.
Legitimate companies and honest individuals often make that information public:
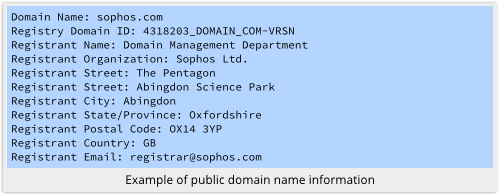
But many domain name service (DNS) registrars offer privacy protection.
Even though the registrar knows who you are, and where you live, for accountability reasons, it shields that information from the rest of the world, for privacy reasons:
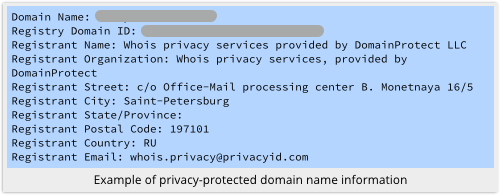
The comparative ease with which crooks can harvest WHOIS data, which includes names, physical addresses and phone numbers, makes DNS privacy protection well worth considering, especially for small businesses and individuals.
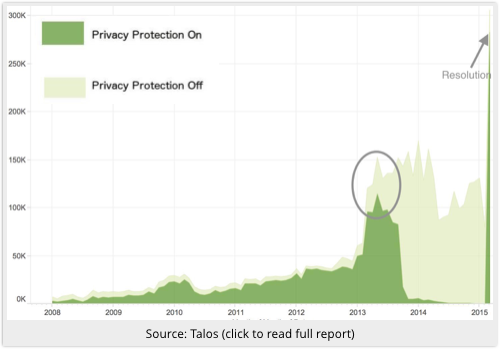
What Talos spotted is that domains registered for Google Apps through a registrar called eNom underwent a strange, and at first unexplained, change near the beginning of 2013.
For years, the proportion of customers requesting privacy protection remained fairly constant, at about 90%.
That started to change rapidly in 2013, until by the start of 2015, about 99% of customers were *not* using privacy protection.
The explanation turned out to be very simple.
When eNom customers renewed a protected Google Apps domain, the protection was lost, apparently due to Google sending incorrect data back at the end of the renewal process.
In other words, what amounted to a single-bit error – Protected? (Y/N) – blew the cover of customers who had requested privacy for their registration data.
What to do?
If you were one of the affected customers, there isn’t a lot you can do now to “unreveal” your data.
That’s the thorny problem of data breaches: how to re-hide data that can’t be changed easily, or even at all, like your physical address or your birthday.
Anyone who did a WHOIS query against your domain name while it was non-private now has your data, and may end up keeping it as part of the internet’s historical record.
Nevertheless, this incident does remind us of one thing: if you have data that you have deliberately opted out of making public, it’s worth checking, as regularly as you can, to make sure that you remain opted out.
The earlier you spot any mistakes – much like realising you are listed in the phonebook when you weren’t supposed to be – the earlier you can try to get the mistake reversed.
Also, if your data was revealed as part of a more general operational error (which seem to be what happened here), the sooner someone says something, the better for everyone else, especially those who haven’t been affected yet.
Think of checking for and reporting privacy glitches partly as a protective move for yourself, and partly as an altruistic move for the rest of us!


Dan
“But many domain name service (DNS) providers offer privacy protection”
No they don’t, domain registrars do.
A DNS provider is not the same thing as a domain registrar.
Paul Ducklin
I guess it’s important to use that word “registrar.” It sounded confusingly medical or legalistic, but you’re right: if you have a SoHo router, you are probably a DNS provider yourself, since you provide DNS service on the router your own internal network :-) But you probably aren’t a company that can register DNS names in the first place…
I’ll change the article. Thanks.
Bob
You’ve got to be kidding. You spent eight paragraphs before getting to the point.
Paul Ducklin
Well, seven sentences, actually. It’s called “setting the scene.” Google has done all these things safely…which makes the glitch we’re going to talk about more surprising.
If you’re that fussed about brevity, why did you use two sentences in your comment, the first of which is a rhetorical question – a literary device that is pretty much redundant by definition?