 Regular readers will recognise the name Gabor Szappanos, a SophosLabs expert whose expertise and research features regularly at conferences and on this site.
Regular readers will recognise the name Gabor Szappanos, a SophosLabs expert whose expertise and research features regularly at conferences and on this site.
Szappi, as we shall abbreviate him from now on, decided to pick one vulnerability from about a year ago, known as CVE-2014-1761.
He investigated its abuse in a wide range of known attacks.
In particular, he looked at how the crooks had evolved their understanding and exploitation of this hole since it first appeared.
Why do this?
In Szappi’s own words:
It is a common practice in the anti-malware world that security products are compared to each other in comparative tests. Even the tests themselves can be evaluated in relation to the criteria of the Anti-Malware Testing Standards Organization. The only players who are not rated are the malware authors. This is for a good reason: their activities cover a wide range of operations that don’t fully match and can't be exactly measured.
There [aren't] common criteria for rating them, although this information could be useful for the defenders: it is always good to know the strength of the enemy at the other side of the gate.
Notably, Szappi compares the skills of so-called Advanced Persistent Threat (APT) attackers, who typically have focused targets and motivations (e.g. state-based intelligence collection), and “regular” cybercrooks, who are unashamedly after all of us for anything they can get that can be turned into ill-gotten financial gain.
The result is a fascinating paper entitled Exploit This: Evaluating the Exploit Skills of Malware Groups.
The bug explained
CVE-2014-1761 is a bug in how RTF (Rich Text Format) files are handled when they are opened in an unpatched version of Microsoft Word.
Booby-trapped data is carefully buried in an RTF file – data that ought simply to be rejected, or to appear as meaningless but harmless garbage – so that using the file will crash Word, wrest back control of the processor, and infect your computer.
You’ll know his sort of attack as a drive-by install, because the dodgy file takes over without any of the usual pop-up warnings about executing software from an untrusted source; and you’ll know the exploit trickery it uses as a Remote Code Execution hole, or RCE, because that’s what exactly what happens.
Usually, an attack unfolds when you click a web link leading to a harmless-looking RTF document, or open an email with some kind of interesting-looking RTF attachment.
And RTF files look as harmless as can be: rich text format is a text-based markup language that describes in vaguely human-readable form what a document is supposed to look like.
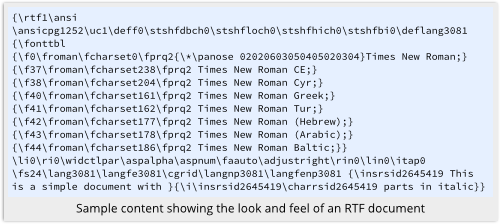
In other words, RTF files make excellent attack documents because they don’t carry the “risk reputation” of files such as SWF (Flash), PDF or even Word’s native .DOC and .DOCX formats.
As well as taking over your computer with an RCE exploit, booby-trapped documents of the sort anaylsed by Szappi typically have another trick up their sleeves.
If the exploit works, instead of leaving you with the tell-tale sign of a crashed Word and no visible document at all, the attacker finishes off by restarting Word and loading up a so-called decoy document, carried along as part of the original booby-trapped file, that looks realistic.
In Szappi’s samples, the decoys ranged from male dating ads, to correspondence from the Lomonosov Moscow State University, to travel articles:
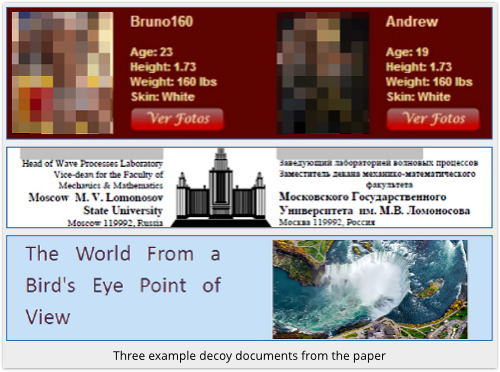
How the crooks fared
Interestingly, Szappi found that the “regular” crooks were smarter, faster and more effective at taking existing attacks and breathing new life into them.
In contrast, the APT attackers seemed less advanced, though in fairness, they only ever need to be more advanced that the victims they have in their sights at any time.
Why burn an brand new exploit when your target is still using an unpatched Word 2010 from a year ago?
As Szappi concludes (my emphasis):
The APT players lack deep skills of exploitation... If security researchers and system administrators follow and act upon vulnerability announcements, they are likely to be prepared for these groups.
Despite all this, one should never underestimate the malware authors mentioned in this report. They develop sophisticated Trojan families, and they manage to deploy them successfully to high profile organizations. The fact that they are not the masters of exploitation doesn’t mean that they are any less dangerous.
But they are not omnipotent either. Understanding their limitations helps us to prepare our defences.
About the paper
There’s a fair amount of technical detail in the paper, which makes it handy for security analysts and reverse engineers, but even if you aren’t technical, you can skip the detail and just follow the fascinating tale of the evolution of a widely-abused security hole.
So I strongly recommend it to techies and non-techies alike.
It’s an insightful and thought-provoking journey into the machinations of the cyberunderworld.
Enjoy.

![Click to read the paper [PDF]... Click to read the paper [PDF]...](https://news-sophos.go-vip.net/wp-content/uploads/sites/2/2015/02/paper-5001.png)
Eman
Great read, thanks Paul! I’m interested in your thoughts regarding conclusion #2 which states, “…The common malware authors show more skills in understanding exploits than the well-known APT groups.” Do you think this is because a.) the APT groups have some sort of ethics (formal or informal) in which they try to minimize casualties among the non-targets or b.) they’re just lazy and don’t give a rat’s hiney about effectiveness after infecting the intended target?
Gabor Szappaos
I would lean towards b)
There is definitely no ethics behind it, just practicality. I think most of the APT groups don’t have exploit specialist, which limits their capabilities.
Paul Ducklin
Maybe it’s all down to economics. If you’re not actually coming up with your own exploits, but buying them on the underground, then you aren’t going to spend more that you need to come out ahead.
“Ahead” for an APTster might be nothing more than “infect at least one computer in company X, steal info about Y, and then abandon ship.” Why burn good money, and then burn an exploit you didn’t need to disclose, if you are attacking an organisation that *still* hasn’t patched against a very well publicised vuln in Word 2010 from a year ago?
“Ahead” for a cybercrook is more like “how much money have we actually cashed out, how is future revenue looking, and how can we invest to make lots and lots more?”
Also…what’s the bet that the bureaucracy for crooks to get approval to spend $50,000 on an update exploit is a lot lower than it is for someone in a governmental hacking squad. You can imagine the meeting:
Government hacker: Can we have $50,000 for a new IE 11 0-day?
Hacking department accountant: What’s wrong with the old one? It’s nearly brand new!
:-)