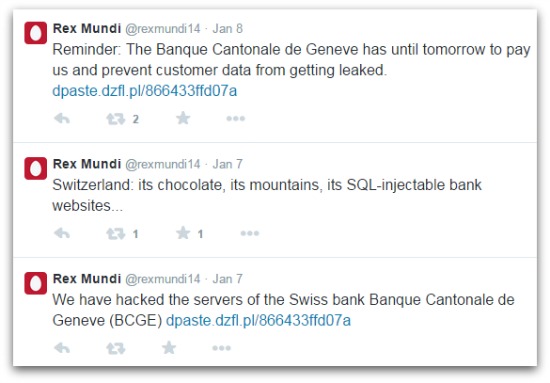
Serial cyber-extortionist gang Rex Mundi has published a cache of emails apparently stolen from the servers of Swiss bank Banque Cantonale de Geneve (BCGE).
The crooks had been trying to blackmail the bank into paying 10,000 Euros to keep the stolen data private.
The theft was announced on the @rexmundi14 twitter feed on Wednesday, with links to the stolen data made public on Friday after the bank refused to give in to extortion.
The exact scale of the leak is unclear, with Reuters describing “more than 30,000 emails” and Bloomberg claiming it affects “about 30,000 clients”. Either way, it seems like a reasonably large amount of information for a bank to have leaked to the world, especially one that’s based in a nation with a reputation for privacy in financial matters.
The bank played down the sensitivity of the data leaked, insisting it was of “no particular financial risk for clients or the bank”. As a spokesperson told Reuters:
At first analysis, this information is hardly critical, is obsolete or corresponds to foreseen contents about which it has already informed a significant number of clients concerned.
There were apparently no banking passwords or codes included in the cache, which should come as some consolation to both the bank and the customers involved.
Rex Mundi has some history in extortion attempts on organisations it has compromised, with previous targets including Domino’s Pizza.
Blackmailing victims of hacking in this way is a common cybercriminal approach – sort of the reverse of the ransomware threat.
Where ransomware such as CryptoLocker encrypts or otherwise locks up systems or data and demands money for the keys, this sort of extortion threatens to reveal information unless a bounty is paid.
Financial firms whose data is highly private are a common target for this sort of crime, for example in the case of Belgian credit house Elantis in 2012. Others holding very sensitive data are also at risk, such as medical firms.
The third main prong of the cyberextortion threat targets websites and services rather than data, threatening to overload sites with DDoS attacks and hamper businesses unless they pay up.
In this category gambling sites tend to be the favourite victims, but others including dating sites and even hospitals have also been hit.
Semi-cryptic commentary on the Rex Mundi feed implies that the compromise took the form of an SQL injection attack, one of the most common ways of bypassing website security.
One might expect a bank to take more care with the security of the systems it exposes to the internet, and perhaps to segregate its data a little better, keeping private information away from web-facing servers.
Nevertheless, data theft remains a crime and BCGE should be commended for refusing to bow to blackmail.
Image of YYYYY courtesy of Shutterstock.

Leave a Reply