 United States Central Command, better known as CENTCOM, is responsible for US military operations in the Middle East.
United States Central Command, better known as CENTCOM, is responsible for US military operations in the Middle East.
As you can imagine, “owning” any part of CENTCOM’s social media presence would make for some serious bragging rights in the hacking scene, as well as attracting a fair amount of public attention.
Sadly, that’s what seems to have happened, with reports stating that a hacking group known as CyberCaliphate took over CENTCOM’s Twitter and YouTube accounts.
Right now, those accounts are rather embarrassingly out of action.
CENTCOM’s Twitter account is described as “suspended,” which suggests it may be back some time soon:
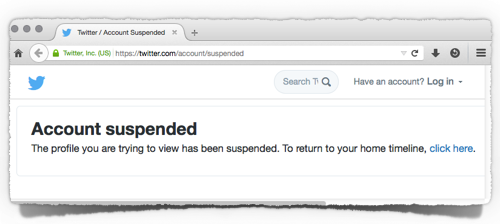
But its YouTube account certainly sounds as though it might be off the air for longer, considering that it “has been terminated due to repeated or severe violations”:
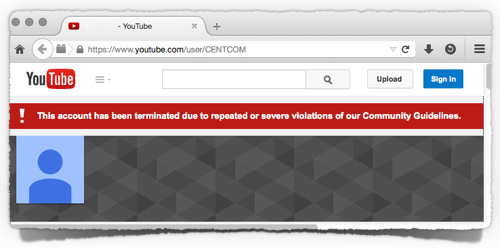
According to reports, the hackers tried to pile on the embarrassment by “leaking” documents such as maps, diagrams and presentations.
But most if not all of the data published sounds as though it was scraped from sites where it is already publicly available,
CENTCOM’s main page also promotes its Flickr and Facebook pages as places to meet the organisation online; both those sites seem to be functioning normally.
Hacking and counter hacking of social media accounts is sadly very common, and isn’t limited to high profile victims like CENTCOM, or high traffic victims such as celebrities.
Sure, hacking CENTCOM’s Twitter gives you huge bragging rights and very broad propaganda opportunities.
At least, it gives you all of that until someone notices that your rants don’t quite fit CENTCOM’s profile, and shut the account down, as seems to have happened here.
What about little old me?
But don’t assume that cybercrooks are only interested in accounts like CENTCOM’s.
Politically motivated hackers probably aren’t hugely interested in your account, or my account, to be sure.
But other crooks may very well be interested in you, along with anyone else whose account they can get their hands on.
That’s because genuine social media accounts – ones that weren’t created yesterday and have an established circle of friends and followers – are worth something that motivates most cybercriminals much more than political notoriety.
Money.
What to do?
Here are three quick tips you can use to keep the crooks out of your accounts:
- Pick Proper Passwords. (And don’t use the same password on two sites: if remembering complex passwords is hard for you, try a password manager.)
- Use two-factor authentication for any services that support it. (This can be a hassle on single accounts operated by a team of people, but it can be done.)
- For team-operated social media accounts, reduce the number of people with write access.
In real life, the “hack” of CENTCOM hasn’t amounted to much, and as far as we can tell, no operational information was lost.
But it’s still a bad look, and for a business, recovering the trust of your customers and prospects is work you’d really rather avoid.

Jim McCleary
What the hell is CENTCOM doing on twitter in the first place? Twitter is for twits. Definition (Webster) twit: fool.
Justin
they should publish what the password was… Would be funny to find out it was just 123456789, but not completely unexpected.