 The Immobilise National Property Register website – the place where UK residents register their flat-screen TVs, games consoles, cameras and other pricey toys in case burglars steal them – has sewn up security holes that left millions of records wide open to interception.
The Immobilise National Property Register website – the place where UK residents register their flat-screen TVs, games consoles, cameras and other pricey toys in case burglars steal them – has sewn up security holes that left millions of records wide open to interception.
Information Security Consultant Paul Moore says he first disclosed issues on the site back in 2013.
The Immobilise register allows people to enter details about their valuables, including a registrant’s name; home address; telephone numbers; email address; the make and model of each item; identifying factors such as serial numbers, IMEIs, or unique marks; and how much the items are worth.
Immobilise directly feeds such data into the NMPR (National Mobile Property Register), which is the police’s national database for stolen property.
The way the register works is that Immobilise issues a certificate after you’ve registered a gadget.
You can then give the certificate to the police or your insurance company, either of whom can use it to confirm your device’s authenticity. Likewise, confiscated goods can be returned to their rightful owners.
Moore gave this example of what the certificates look like:
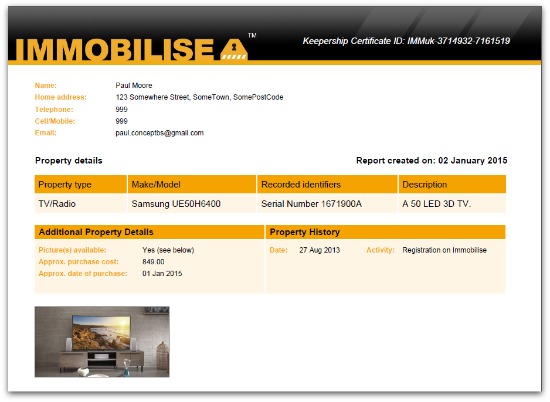
That certificate number includes a static set of letters followed by a user ID and a certificate ID.
You’d imagine that it would be safe from snooping eyes, given that an attacker wouldn’t know the user or certificate IDs, right?
Wrong. Until recently, those numbers, far from being random, were sequential, meaning that an attacker could loop through combinations to collect what Moore says are 28+ million entries.
It’s a thief’s dream, he said:
That's quite a nice shopping list for a would-be burglar!
Such a vulnerability is known as an insecure direct object reference.
That’s the fancy name for the sort of flaw that allows attackers to bypass authorization and to access resources directly by modifying the value of a parameter so that it refers to someone else’s record.
Delta Airlines boarding cards, for example, were a recently affected by a similar sort of bug, as was customer address data at the online retail arm of Alibaba.
Finding a valid ID for other people’s data may be as simple as changing a single digit or letter in a URL, something that can be done by hand in your browser’s address bar, or on an industrial scale with a script or program.
Moore refers to it as the “open DOR” attack to convey its simplicity.
Recipero issued an official response about the flaw after news about the security holes broke on Tuesday.
It says it first learned of the vulnerability on 3 January 2015 and has now removed the affected feature:
The vulnerability was in a feature intended for use by insurers when confirming the validity of an ownership certificate given to them by a claimant. The feature was removed within 30 minutes of us becoming aware.
A thorough review of our records reveals no evidence of any data leakage and therefore no requirement to contact any individual Immobilise users.
Image of burglar courtesy of Shutterstock.

Janne
What a stupid idea!
rakso75
“no evidence of any data leakage” DOES NOT mean no data leakage…
Brian
I had an email from them recently inviting me to join.
I was tempted at the time, but didn’t do anything about it.
Am I glad I didn’t.
Seemed a good idea at the time. Phew