Microsoft on Tuesday released 56 patches affecting 10 product families. Two of the addressed issues are considered by Microsoft to be of Critical severity – and, unusually, both belong to the blended Office-365 product family. Eight have a CVSS base score of 8.0 or higher. One is known to be under active exploit in the wild, and two others are publicly disclosed.
That’s the good news. We’ll get to the advisories in a moment.
At patch time, six CVEs are judged more likely to be exploited in the next 30 days by the company’s estimation, in addition to the one already detected to be so. Various of this month’s issues are amenable to direct detection by Sophos protections, and we include information on those in a table below.
The release also includes information on 14 Edge patches released last week, as well as 12 ColdFusion and four Adobe Reader patches released today. (The sole Edge patch originating with Microsoft is counted in this total rather in the general Patch Tuesday count of 56; the rest originated with Chromium itself and were patched earlier in the month.) We have included information on all those patches in Appendix D. There is no update to the Servicing Stack listed in Microsoft’s manifest this month.
Microsoft also released information on 84 CVEs affecting CBL Mariner and/or Azure Linux. All 84 CVEs originated with MITRE and have been addressed over the course of the past week, and all 84 are indicated as exploited in in the wild (though none are marked as publicly disclosed). Little information was made available on these 84 CVEs, but we’ve provided some guidance in Appendix F at the end of the post.
We are as always including at the end of this post appendices listing all Microsoft’s patches sorted by severity (Appendix A), by predicted exploitability timeline and CVSS Base score (Appendix B), and by product family (Appendix C). Appendix E provides a breakout of the patches affecting the various Windows Server platforms.
By the numbers
- Total CVEs: 56
- Publicly disclosed: 2
- Exploit detected: 1
- Severity
- Critical: 2
- Important: 54
- Impact
- Denial of Service: 3
- Elevation of Privilege: 28
- Information Disclosure: 4
- Remote Code Execution: 19
- Spoofing: 2
- CVSS Base score 9.0 or greater: 0
- CVSS Base score 8.0 or greater: 8
Figure 1: Elevation of Privilege issues were the most numerous in the December collection, once again
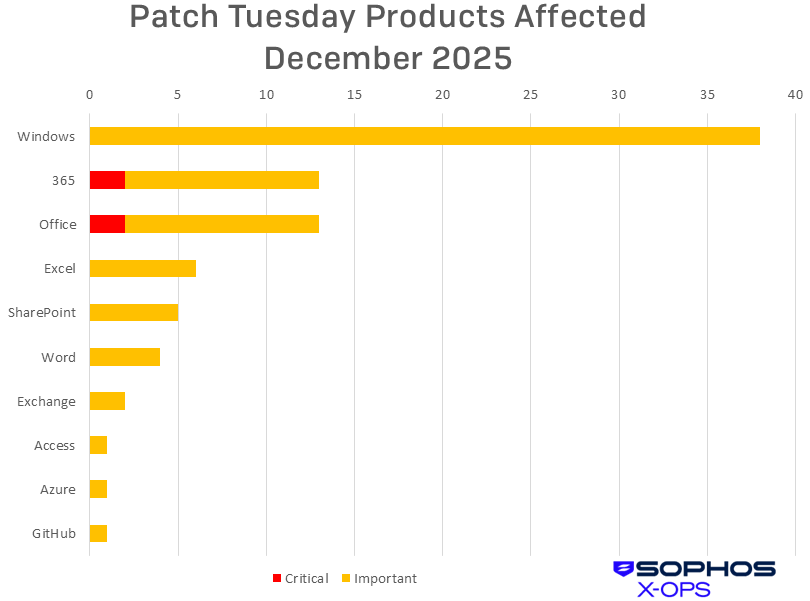
Products
- Windows: 38
- 365: 13
- Office: 13
- Excel: 6
- SharePoint: 5
- Word: 4
- Exchange: 2
- Access: 1
- Azure: 1
- GitHub: 1
As is our custom for this list, CVEs that apply to more than one product family are counted once for each family they affect. We note, by the way, that CVE names don’t always reflect affected product families closely. In particular, some CVEs names in the Office family may mention products that don’t appear in the list of products affected by the CVE, and vice versa.
Figure 2: A smaller, heavily end-user-oriented group of product families received patches this month. Though Windows accounts for half of them, patches related to the operating system are all Important in severity
Notable December updates
In addition to the issues discussed above, several specific items merit attention.
CVE-2025-62554 — Microsoft Office Remote Code Execution Vulnerability
CVE-2025-62555 — Microsoft Word Remote Code Execution Vulnerability
CVE-2025-62557 — Microsoft Office Remote Code Execution Vulnerability
CVE-2025-62558 — Microsoft Word Remote Code Execution Vulnerability
CVE-2025-62559 — Microsoft Word Remote Code Execution Vulnerability
CVE-2025-62560 — Microsoft Excel Remote Code Execution Vulnerability
CVE-2025-62561 — Microsoft Excel Remote Code Execution Vulnerability
All seven of these RCE issues affect multiple versions of 365 and Office, including Microsoft Office LTSC for Mac 2021 and 2024. However, the patches for those Mac versions aren’t ready yet. Users responsible for updating Macs are asked to monitor the CVE information for each vulnerability for further word on those patches. Of the seven, pay special attention to CVE-2025-62554 and CVE-2025-62257 (the two simply called “Office” vulnerabilities) – they’re the ones which Preview Pane is an attack vector. Those two CVEs are Critical-severity and have a CVSS Base score of 8.4. The others are Important-severity.
CVE-2025-54100 — PowerShell Remote Code Execution Vulnerability
As with the 84 Mariner vulnerabilities mentioned above, the release of this patch arrived with less information than Microsoft-issued CVEs generally do. That said, this Important-class issue is allotted to Windows; as with the GitHub issue discussed below, it involves improper neutralization of special elements used in a command. For this one, Microsoft notes that after installation, users attempting to deploy the Invoke-WebRequest command will get a new confirmation prompt warning them of potentially unwanted script code execution and recommending that they include the -UseBasicParsing switch to keep things behaving nicely.
CVE-2025-64666 — Microsoft Exchange Server Elevation of Privilege Vulnerability
CVE-2025-64667 — Microsoft Exchange Server Spoofing Vulnerability
These two Important-severity bugs both affect Exchange Server 2016 and 2019, which are out-of-support versions of Exchange – unless you’re paying for Microsoft’s Extended Security Update (ESU) program, you’re not getting these patches. (Exchange Server Subscription Edition subscribers are covered.) The EoP is a fairly specialized item that would require the attacker to prepare the target environment ahead of time, while the Spoofing bug affects, specifically, how From: addresses are displayed to the user.
CVE-2025-64671 — GitHub Copilot for Jetbrains Remote Code Execution Vulnerability
The only publicly disclosed vulnerability so far this month allows the Jetbrain AI-based coding assistant to ruin the vibe-coding vibe, thanks to improper neutralization of special elements used in a command. According to Microsoft, an attacker could execute additional commands by appending them to commands allowed in the user’s terminal auto-approve setting. This vulnerability is credited to independent researcher Ari Marzouk, who just last weekend posted analysis of a potentially lively new class of vulnerabilities in AI IDEs. An intriguing read.
Figure 3: The year wrapped up with Elevation of Privilege and Remote Code Execution swapping spots at the top of the charts. Note, though, that even though there were fewer RCE bugs squashed this year, there was a higher percentage of Critical-severity RCEs. Overall there were 92 Critical-severity CVEs address in 2025 compared to 55 last year.
Figure 4: Behold the final (one hopes) 2025 tally: In the end, it was the most patch-heavy year (1196 excluding out-of-band patch releases) since 2020 (1245 patches excluding out-of-bands), with two record-breaking months in January and October.
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2025-59516 | Exp/2559516-A | Exp/2559516-A |
| CVE-2025-59517 | Exp/2559517-A | Exp/2559517-A |
| CVE-2025-62221 | Exp/2562221-A | Exp/2562221-A |
| CVE-2025-62454 | Exp/2562454-A | Exp/2562454-A |
| CVE-2025-62470 | Exp/2562470-A | Exp/2562470-A |
| CVE-2025-62472 | Exp/2562472-A | Exp/2562472-A |
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of December patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Elevation of Privilege (28 CVEs)
| Important severity | |
| CVE-2025-55233 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2025-59516 | Windows Storage VSP Driver Elevation of Privilege Vulnerability |
| CVE-2025-59517 | Windows Storage VSP Driver Elevation of Privilege Vulnerability |
| CVE-2025-62221 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2025-62454 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2025-62455 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability |
| CVE-2025-62457 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2025-62458 | Win32k Elevation of Privilege Vulnerability |
| CVE-2025-62461 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2025-62462 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2025-62464 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2025-62466 | Windows Client-Side Caching Elevation of Privilege Vulnerability |
| CVE-2025-62467 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2025-62469 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2025-62470 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2025-62472 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability |
| CVE-2025-62474 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability |
| CVE-2025-62565 | Windows File Explorer Elevation of Privilege Vulnerability |
| CVE-2025-62569 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2025-62571 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2025-62572 | Application Information Service Elevation of Privilege Vulnerability |
| CVE-2025-62573 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| CVE-2025-64658 | Windows File Explorer Elevation of Privilege Vulnerability |
| CVE-2025-64661 | Windows Shell Elevation of Privilege Vulnerability |
| CVE-2025-64666 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| CVE-2025-64673 | Windows Storage VSP Driver Elevation of Privilege Vulnerability |
| CVE-2025-64679 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-64680 | Windows DWM Core Library Elevation of Privilege Vulnerability |
Remote Code Execution (19 CVEs)
| Critical severity | |
| CVE-2025-62554 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-62557 | Microsoft Office Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-54100 | PowerShell Remote Code Execution Vulnerability |
| CVE-2025-62456 | Windows Resilient File System (ReFS) Remote Code Execution Vulnerability |
| CVE-2025-62549 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2025-62550 | Azure Monitor Agent Remote Code Execution Vulnerability |
| CVE-2025-62552 | Microsoft Access Remote Code Execution Vulnerability |
| CVE-2025-62553 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62555 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62556 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62558 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62559 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62560 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62561 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62562 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2025-62563 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62564 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-64671 | GitHub Copilot for Jetbrains Remote Code Execution Vulnerability |
| CVE-2025-64678 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Information Disclosure (4 CVEs)
| Important severity | |
| CVE-2025-62468 | Windows Defender Firewall Service Information Disclosure Vulnerability |
| CVE-2025-62473 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-62570 | Windows Camera Frame Server Monitor Information Disclosure Vulnerability |
| CVE-2025-64670 | Windows DirectX Information Disclosure Vulnerability |
Denial of Service (3 CVEs)
| Important severity | |
| CVE-2025-62463 | DirectX Graphics Kernel Denial of Service Vulnerability |
| CVE-2025-62465 | DirectX Graphics Kernel Denial of Service Vulnerability |
| CVE-2025-62567 | Windows Hyper-V Denial of Service Vulnerability |
Spoofing (2 CVEs)
| Important severity | |
| CVE-2025-64667 | Microsoft Exchange Server Spoofing Vulnerability |
| CVE-2025-64672 | Microsoft SharePoint Server Spoofing Vulnerability |
Appendix B: Exploitability and CVSS
This is a list of the December CVEs judged by Microsoft to be more likely to be exploited in the wild within the first 30 days post-release. The list is arranged by CVE.
| Exploitation more likely within the next 30 days | |
| CVE-2025-59516 | Windows Storage VSP Driver Elevation of Privilege Vulnerability |
| CVE-2025-59517 | Windows Storage VSP Driver Elevation of Privilege Vulnerability |
| CVE-2025-62454 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2025-62458 | Win32k Elevation of Privilege Vulnerability |
| CVE-2025-62470 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2025-62472 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability |
The CVE listed below was known to be under active exploit prior to the release of this month’s patches.
| CVE-2025-62221 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
These are the December CVEs with a Microsoft-assessed CVSS Base score of 8.0 or higher. They are arranged by score and further sorted by CVE. For more information on how CVSS works, please see our series on patch prioritization schema.
| CVSS Base | CVSS Temporal | CVE | Title |
| 8.8 | 7.7 | CVE-2025-62456 | Windows Resilient File System (ReFS) Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-62549 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-62550 | Azure Monitor Agent Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-64672 | Microsoft SharePoint Server Spoofing Vulnerability |
| 8.8 | 7.7 | CVE-2025-64678 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| 8.4 | 7.3 | CVE-2025-62554 | Microsoft Office Remote Code Execution Vulnerability |
| 8.4 | 7.3 | CVE-2025-62557 | Microsoft Office Remote Code Execution Vulnerability |
| 8.4 | 7.3 | CVE-2025-64671 | GitHub Copilot for Jetbrains Remote Code Execution Vulnerability |
Appendix C: Products Affected
This is a list of December’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family. Certain issues for which advisories have been issued are covered in Appendix D, and issues affecting Windows Server are further sorted in Appendix E. All CVE titles are accurate as made available by Microsoft; for further information on why certain products may appear in titles and not product families (or vice versa), please consult Microsoft.
Windows (38 CVEs)
| Important severity | |
| CVE-2025-54100 | PowerShell Remote Code Execution Vulnerability |
| CVE-2025-55233 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2025-59516 | Windows Storage VSP Driver Elevation of Privilege Vulnerability |
| CVE-2025-59517 | Windows Storage VSP Driver Elevation of Privilege Vulnerability |
| CVE-2025-62221 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2025-62454 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2025-62455 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability |
| CVE-2025-62456 | Windows Resilient File System (ReFS) Remote Code Execution Vulnerability |
| CVE-2025-62457 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2025-62458 | Win32k Elevation of Privilege Vulnerability |
| CVE-2025-62461 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2025-62462 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2025-62463 | DirectX Graphics Kernel Denial of Service Vulnerability |
| CVE-2025-62464 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2025-62465 | DirectX Graphics Kernel Denial of Service Vulnerability |
| CVE-2025-62466 | Windows Client-Side Caching Elevation of Privilege Vulnerability |
| CVE-2025-62467 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2025-62468 | Windows Defender Firewall Service Information Disclosure Vulnerability |
| CVE-2025-62469 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2025-62470 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2025-62472 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability |
| CVE-2025-62473 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-62474 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability |
| CVE-2025-62549 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2025-62565 | Windows File Explorer Elevation of Privilege Vulnerability |
| CVE-2025-62567 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2025-62569 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2025-62570 | Windows Camera Frame Server Monitor Information Disclosure Vulnerability |
| CVE-2025-62571 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2025-62572 | Application Information Service Elevation of Privilege Vulnerability |
| CVE-2025-62573 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| CVE-2025-64658 | Windows File Explorer Elevation of Privilege Vulnerability |
| CVE-2025-64661 | Windows Shell Elevation of Privilege Vulnerability |
| CVE-2025-64670 | Windows DirectX Information Disclosure Vulnerability |
| CVE-2025-64673 | Windows Storage VSP Driver Elevation of Privilege Vulnerability |
| CVE-2025-64678 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2025-64679 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-64680 | Windows DWM Core Library Elevation of Privilege Vulnerability |
365 (13 CVEs)
| Critical severity | |
| CVE-2025-62554 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-62557 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-62562 | Microsoft Outlook Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-62552 | Microsoft Access Remote Code Execution Vulnerability |
| CVE-2025-62553 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62555 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62556 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62558 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62559 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62560 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62561 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62563 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62564 | Microsoft Excel Remote Code Execution Vulnerability |
Office (13 CVEs)
| Critical severity | |
| CVE-2025-62554 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-62557 | Microsoft Office Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-62552 | Microsoft Access Remote Code Execution Vulnerability |
| CVE-2025-62553 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62555 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62556 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62558 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62559 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62560 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62561 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62562 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2025-62563 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62564 | Microsoft Excel Remote Code Execution Vulnerability |
Excel (6 CVEs)
| Important severity | |
| CVE-2025-62553 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62556 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62560 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62561 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62563 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62564 | Microsoft Excel Remote Code Execution Vulnerability |
SharePoint (5 CVEs)
| Critical severity | |
| CVE-2025-62562 | Microsoft Outlook Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-62555 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62558 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62559 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-64672 | Microsoft SharePoint Server Spoofing Vulnerability |
Word (4 CVEs)
| Critical severity | |
| CVE-2025-62562 | Microsoft Outlook Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-62555 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62558 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-62559 | Microsoft Word Remote Code Execution Vulnerability |
Exchange (2 CVEs)
| Important severity | |
| CVE-2025-64666 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| CVE-2025-64667 | Microsoft Exchange Server Spoofing Vulnerability |
Access (1 CVE)
| Important severity | |
| CVE-2025-62552 | Microsoft Access Remote Code Execution Vulnerability |
Azure (1 CVE)
| Important severity | |
| CVE-2025-62550 | Azure Monitor Agent Remote Code Execution Vulnerability |
GitHub (1 CVE)
| Important severity | |
| CVE-2025-64671 | GitHub Copilot for Jetbrains Remote Code Execution Vulnerability |
Appendix D: Advisories and Other Products
There are 14 Edge-related advisories noted in December’s release. All but CVE-2025-62223 originated with Chrome. All were patched during the previous week. Please note that the Microsoft-issued CVE applies only to Edge for Mac.
| CVE-2025-13630 | Chromium: CVE-2025-13630 Type Confusion in V8 |
| CVE-2025-13631 | Chromium: CVE-2025-13631 Inappropriate implementation in Google Updater |
| CVE-2025-13632 | Chromium: CVE-2025-13632 Inappropriate implementation in DevTools |
| CVE-2025-13633 | Chromium: CVE-2025-13633 Use after free in Digital Credentials |
| CVE-2025-13634 | Chromium: CVE-2025-13634 Inappropriate implementation in Downloads |
| CVE-2025-13635 | Chromium: CVE-2025-13635 Inappropriate implementation in Downloads |
| CVE-2025-13636 | Chromium: CVE-2025-13636 Inappropriate implementation in Split View |
| CVE-2025-13637 | Chromium: CVE-2025-13637 Inappropriate implementation in Downloads |
| CVE-2025-13638 | Chromium: CVE-2025-13638 Use after free in Media Stream |
| CVE-2025-13639 | Chromium: CVE-2025-13639 Inappropriate implementation in WebRTC |
| CVE-2025-13640 | Chromium: CVE-2025-13640 Inappropriate implementation in Passwords |
| CVE-2025-13720 | Chromium: CVE-2025-13720 Bad cast in Loader |
| CVE-2025-13721 | Chromium: CVE-2025-13721 Race in v8 |
| CVE-2025-62223 | Microsoft Edge (Chromium-based) for Mac Spoofing Vulnerability |
Adobe is releasing patches for 12 ColdFusion issues today with Bulletin APSB25-105. All 12 CVEs affect ColdFusion 22, 16, 4 and earlier versions.
| Critical severity | |
| CVE-2025-61808 | Unrestricted Upload of File with Dangerous Type (CWE-434) |
| CVE-2025-61809 | Improper Input Validation (CWE-20) |
| CVE-2025-61810 | Deserialization of Untrusted Data (CWE-502) |
| CVE-2025-61811 | Improper Access Control (CWE-284) |
| CVE-2025-61812 | Improper Input Validation (CWE-20) |
| CVE-2025-61813 | Improper Restriction of XML External Entity Reference (‘XXE’) (CWE-611) |
| CVE-2025-61830 | Deserialization of Untrusted Data (CWE-502) |
| Important severity | |
| CVE-2025-61821 | Improper Restriction of XML External Entity Reference (‘XXE’) (CWE-611) |
| CVE-2025-61822 | Improper Input Validation (CWE-20) |
| CVE-2025-61823 | Improper Restriction of XML External Entity Reference (‘XXE’) (CWE-611) |
| CVE-2025-64897 | Improper Access Control (CWE-284) |
| CVE-2025-64898 | Insufficiently Protected Credentials (CWE-522) |
Adobe is also releasing patches for four Adobe Reader issues today with Bulletin APSB25-119. All four CVEs affect Reader versions 25.001.20982, 25.001.20668, 24.001.30273, 20.005.30793, 20.005.30803 and earlier.
| Critical severity | |
| CVE-2025-64785 | Untrusted Search Path (CWE-426) |
| CVE-2025-64899 | Out-of-bounds Read (CWE-125) |
| Moderate severity | |
| CVE-2025-64786 | Improper Verification of Cryptographic Signature (CWE-347) |
| CVE-2025-64787 | Improper Verification of Cryptographic Signature (CWE-347) |
For information on the Mariner releases, please scroll to Appendix F.
Appendix E: Affected Windows Server versions
This is a table of the 38 CVEs in the December release affecting Windows Server versions 2008 through 2025. The table differentiates among major versions of the platform but doesn’t go into deeper detail (eg., Server Core). An “x” indicates that the CVE does not apply to that version. Administrators are encouraged to use this appendix as a starting point to ascertain their specific exposure, as each reader’s situation, especially as it concerns products out of mainstream support, will vary. For specific Knowledge Base numbers, please consult Microsoft.
| CVE | S-08 | 8r2 | S-12 | 12r2 | S-16 | S-19 | S-22 | 23h2 | S-25 |
| CVE-2025-54100 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-55233 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-59516 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-59517 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62221 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-62454 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-62455 | ■ | ■ | ■ | ■ | ■ | ■ | × | × | × |
| CVE-2025-62456 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-62457 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-62458 | × | ■ | ■ | ■ | ■ | ■ | ■ | × | × |
| CVE-2025-62461 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-62462 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-62463 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-62464 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-62465 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-62466 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62467 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-62468 | × | × | × | × | × | × | × | ■ | ■ |
| CVE-2025-62469 | × | × | × | × | × | × | × | × | ■ |
| CVE-2025-62470 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62472 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62473 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62474 | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62549 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62565 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62567 | × | × | × | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62569 | × | × | × | × | × | × | × | ■ | ■ |
| CVE-2025-62570 | × | × | × | × | × | × | × | × | ■ |
| CVE-2025-62571 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62572 | × | × | × | × | × | × | × | × | ■ |
| CVE-2025-62573 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-64658 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-64661 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-64670 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-64673 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-64678 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-64679 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-64680 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
Appendix F: CBL Mariner / Azure Linux
The following table provides information on 84 CVEs relating to CBL Mariner and / or Azure Linux. All 84 are listed by Microsoft as under exploit in the wild. That said, five of them also have CVSS Base numbers over 8.5, and we indicate those in red for those needing to prioritize. The CVEs are grouped by severity and further ordered by CVE.
| Critical severity | |
| CVE-2025-40242 | gfs2: Fix unlikely race in gdlm_put_lock |
| CVE-2025-40244 | hfsplus: fix KMSAN uninit-value issue in __hfsplus_ext_cache_extent() |
| CVE-2025-40251 | devlink: rate: Unset parent pointer in devl_rate_nodes_destroy |
| CVE-2025-40262 | Input: imx_sc_key – fix memory corruption on unload |
| Important severity | |
| CVE-2025-12385 | Improper validation of tag size in Text component parser |
| CVE-2025-12819 | Untrusted search path in auth_query connection in PgBouncer |
| CVE-2025-34297 | KissFFT Integer Overflow Heap Buffer Overflow via kiss_fft_alloc |
| CVE-2025-40223 | most: usb: Fix use-after-free in hdm_disconnect |
| CVE-2025-40233 | ocfs2: clear extent cache after moving/defragmenting extents |
| CVE-2025-40240 | sctp: avoid NULL dereference when chunk data buffer is missing |
| CVE-2025-40258 | mptcp: fix race condition in mptcp_schedule_work() |
| CVE-2025-40272 | mm/secretmem: fix use-after-free race in fault handler |
| CVE-2025-40312 | jfs: Verify inode mode when loading from disk |
| CVE-2025-40314 | usb: cdns3: gadget: Use-after-free during failed initialization and exit of cdnsp gadget |
| CVE-2025-40319 | bpf: Sync pending IRQ work before freeing ring buffer |
| CVE-2025-59775 | Apache HTTP Server: NTLM Leakage on Windows through UNC SSRF |
| CVE-2025-61729 | Excessive resource consumption when printing error string for host certificate validation in crypto/x509 |
| CVE-2025-66476 | Vim for Windows Uncontrolled Search Path Element Remote Code Execution Vulnerability |
| Moderate severity | |
| CVE-2023-53749 | x86: fix clear_user_rep_good() exception handling annotation |
| CVE-2025-12084 | Quadratic complexity in node ID cache clearing |
| CVE-2025-13836 | Excessive read buffering DoS in http.client |
| CVE-2025-40215 | xfrm: delete x->tunnel as we delete x |
| CVE-2025-40217 | pidfs: validate extensible ioctls |
| CVE-2025-40218 | mm/damon/vaddr: do not repeat pte_offset_map_lock() until success |
| CVE-2025-40219 | PCI/IOV: Add PCI rescan-remove locking when enabling/disabling SR-IOV |
| CVE-2025-40220 | fuse: fix livelock in synchronous file put from fuseblk workers |
| CVE-2025-40243 | hfs: fix KMSAN uninit-value issue in hfs_find_set_zero_bits() |
| CVE-2025-40245 | nios2: ensure that memblock.current_limit is set when setting pfn limits |
| CVE-2025-40247 | drm/msm: Fix pgtable prealloc error path |
| CVE-2025-40248 | vsock: Ignore signal/timeout on connect() if already established |
| CVE-2025-40250 | net/mlx5: Clean up only new IRQ glue on request_irq() failure |
| CVE-2025-40252 | net: qlogic/qede: fix potential out-of-bounds read in qede_tpa_cont() and qede_tpa_end() |
| CVE-2025-40253 | s390/ctcm: Fix double-kfree |
| CVE-2025-40254 | net: openvswitch: remove never-working support for setting nsh fields |
| CVE-2025-40257 | mptcp: fix a race in mptcp_pm_del_add_timer() |
| CVE-2025-40259 | scsi: sg: Do not sleep in atomic context |
| CVE-2025-40261 | nvme: nvme-fc: Ensure ->ioerr_work is cancelled in nvme_fc_delete_ctrl() |
| CVE-2025-40263 | Input: cros_ec_keyb – fix an invalid memory access |
| CVE-2025-40264 | be2net: pass wrb_params in case of OS2BMC |
| CVE-2025-40266 | KVM: arm64: Check the untrusted offset in FF-A memory share |
| CVE-2025-40268 | cifs: client: fix memory leak in smb3_fs_context_parse_param |
| CVE-2025-40269 | ALSA: usb-audio: Fix potential overflow of PCM transfer buffer |
| CVE-2025-40273 | NFSD: free copynotify stateid in nfs4_free_ol_stateid() |
| CVE-2025-40275 | ALSA: usb-audio: Fix NULL pointer dereference in snd_usb_mixer_controls_badd |
| CVE-2025-40277 | drm/vmwgfx: Validate command header size against SVGA_CMD_MAX_DATASIZE |
| CVE-2025-40278 | net: sched: act_ife: initialize struct tc_ife to fix KMSAN kernel-infoleak |
| CVE-2025-40279 | net: sched: act_connmark: initialize struct tc_ife to fix kernel leak |
| CVE-2025-40280 | tipc: Fix use-after-free in tipc_mon_reinit_self(). |
| CVE-2025-40281 | sctp: prevent possible shift-out-of-bounds in sctp_transport_update_rto |
| CVE-2025-40282 | Bluetooth: 6lowpan: reset link-local header on ipv6 recv path |
| CVE-2025-40283 | Bluetooth: btusb: reorder cleanup in btusb_disconnect to avoid UAF |
| CVE-2025-40284 | Bluetooth: MGMT: cancel mesh send timer when hdev removed |
| CVE-2025-40285 | smb/server: fix possible refcount leak in smb2_sess_setup() |
| CVE-2025-40286 | smb/server: fix possible memory leak in smb2_read() |
| CVE-2025-40287 | exfat: fix improper check of dentry.stream.valid_size |
| CVE-2025-40288 | drm/amdgpu: Fix NULL pointer dereference in VRAM logic for APU devices |
| CVE-2025-40289 | drm/amdgpu: hide VRAM sysfs attributes on GPUs without VRAM |
| CVE-2025-40292 | virtio-net: fix received length check in big packets |
| CVE-2025-40293 | iommufd: Don’t overflow during division for dirty tracking |
| CVE-2025-40294 | Bluetooth: MGMT: Fix OOB access in parse_adv_monitor_pattern() |
| CVE-2025-40297 | net: bridge: fix use-after-free due to MST port state bypass |
| CVE-2025-40301 | Bluetooth: hci_event: validate skb length for unknown CC opcode |
| CVE-2025-40303 | btrfs: ensure no dirty metadata is written back for an fs with errors |
| CVE-2025-40304 | fbdev: Add bounds checking in bit_putcs to fix vmalloc-out-of-bounds |
| CVE-2025-40305 | 9p/trans_fd: p9_fd_request: kick rx thread if EPOLLIN |
| CVE-2025-40306 | orangefs: fix xattr related buffer overflow… |
| CVE-2025-40307 | exfat: validate cluster allocation bits of the allocation bitmap |
| CVE-2025-40308 | Bluetooth: bcsp: receive data only if registered |
| CVE-2025-40309 | Bluetooth: SCO: Fix UAF on sco_conn_free |
| CVE-2025-40310 | amd/amdkfd: resolve a race in amdgpu_amdkfd_device_fini_sw |
| CVE-2025-40311 | accel/habanalabs: support mapping cb with vmalloc-backed coherent memory |
| CVE-2025-40313 | ntfs3: pretend $Extend records as regular files |
| CVE-2025-40315 | usb: gadget: f_fs: Fix epfile null pointer access after ep enable. |
| CVE-2025-40317 | regmap: slimbus: fix bus_context pointer in regmap init calls |
| CVE-2025-40321 | wifi: brcmfmac: fix crash while sending Action Frames in standalone AP Mode |
| CVE-2025-40322 | fbdev: bitblit: bound-check glyph index in bit_putcs* |
| CVE-2025-40323 | fbcon: Set fb_display[i]->mode to NULL when the mode is released |
| CVE-2025-40324 | NFSD: Fix crash in nfsd4_read_release() |
| CVE-2025-61727 | Improper application of excluded DNS name constraints when verifying wildcard names in crypto/x509 |
| CVE-2025-65082 | Apache HTTP Server: CGI environment variable override |
| CVE-2025-65637 | A denial-of-service vulnerability exists in github.com/sirupsen/logrus when using Entry.Writer() to log a single-line payload larger than 64KB without newline characters. |
| CVE-2025-66200 | Apache HTTP Server: mod_userdir+suexec bypass via AllowOverride FileInfo |
| CVE-2025-66293 | LIBPNG has an out-of-bounds read in png_image_read_composite |
| Low severity | |
| CVE-2025-13837 | Out-of-memory when loading Plist |




Leave a Reply