In October 2022, we asked you to imagine being stuck in the following awful situation:
Imagine that you’d spoken in what you thought was total confidence to a psychotherapist, but the contents of your sessions had been saved for posterity, along with precise personal identification details such as your unique national ID number, and perhaps including additional information such as notes about your relationship with your family…
…and then, as if that were not bad enough, imagine that the words you’d never expected to be typed in and saved at all, let alone indefinitely, had been made accessible over the internet, allegedly “protected” by little more than a default password giving anyone access to everything.
Sadly, for tens of thousands of trusting patients of the now-bankrupt Psychotherapy Centre Vastaamo, that really happened.
It gets worse
Worse, a cybercriminal found his way into the poorly-secured system and stole all that ultra-personal data.
Worse still, the company responsible for keeping that data secure decided to keep quiet about the intrusion, with the company CEO apparently deciding that he could get away with hiding the breach from the authorities as long as no publicly visible harm came of it.
But the breach couldn’t be denied any more once the company was hit up with a blackmail demand for €450,000 (about $0.5m at the time).
Ultimately, as reported in the Helsinki Times in late 2022 in an article entitled Prosecutors: Vastaamo’s information security was in absolute chaos, the now-former CEO was charged personally with data protection offences, even though the company itself was the victim of a cybercrime.
Worst of all was that when the company itself refused to pay the blackmail money (which, as we pointed out last year, wouldn’t have done much good given that the data had already been stolen), the extortionist turned their attention directly on the company’s patients.
Patients were blackmailed to the tune of €200 each, with cybersecurity journo-sleuth Brian Krebs reporting in 2022 that the demand jumped to €500 if the initial “fee” wasn’t paid within 24 hours, followed by publication of personal details 48 hours after that.
The hacker threatened to release not only the sort of information that would help other crooks to carry out identity theft, including contact details and ID data, but also the saved transcripts of patients’ conversations that we mentioned at the top of this article.
The Finnish authorities issued an arrest warrant for the suspected hacker in October 2022, noting that:
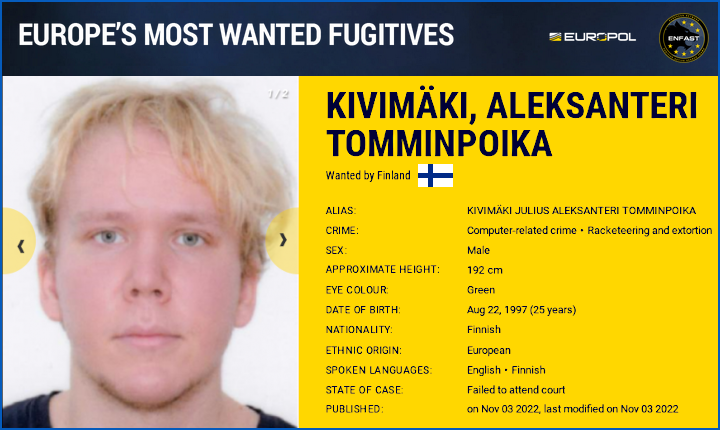
The police have established that the suspect currently resides abroad. For this reason, he was remanded in absentia. A European arrest warrant has been issued against the suspect. He can be arrested abroad under this warrant. After that the police will request his surrender to Finland. An Interpol notice will also be issued against the suspect, who is a Finnish citizen and about 25 years of age.
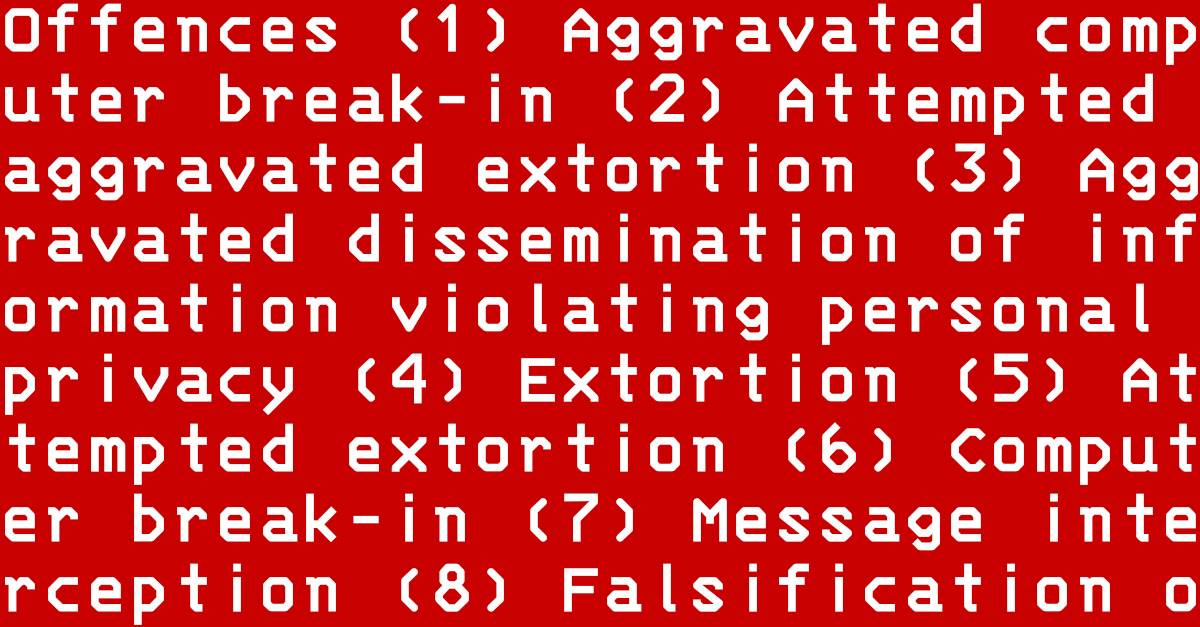
He appeared on Europol’s Most Wanted Fugitives list on 2022-11-03, charged with eight offences: aggravated computer break-in, attempted aggravated extortion, aggravated dissemination of information violating personal privacy, extortion, attempted extortion, computer break-in, message interception, and falsification of evidence:
Suspect apprehended
Well, the Finns have just announced that the suspect has been apprehended in France, where he has been locked up while his extradition to Finland is being processed.
Brian Krebs, who is well-known for digging into the histories of notorious hackers and hacking suspects, has published a report listing a string of previous cybercrimes for which Kivimäki has been convicted, apparently including denial-of-service attacks under the banner of Lizard Squad, theft of source code from Adobe, use of stolen credit cards, and more.
According to Krebs, the suspect was convicted of “orchestrating more than 50,000 cybercrimes”, but got away with a suspended sentence and a small fine, having been under 18 at the time of that criminal activity.
After he’d evaded a prison sentence, says Krebs, the Lizard Squad hacking group openly boasted on Twitter than “All the people that said we would rot in prison don’t want to comprehend what we’ve been saying since the beginning, we have free passes.”
If his extradition from France is approved in this case, and he’s convicted, we can’t imagine the consequences being quite so much of a “free pass” this time, now he’s 25 years old.
What to do?
- Rehearse what you will do if you suffer a breach yourself. You are not preparing to fail if you do so, but you are failing to prepare if you don’t. Learn what your reporting obligations are, and practise what you would say to those affected by the breach. As this case suggests, prompt disclosure would at least have prevented tens of thousands of vulnerable people finding out about the breach from extortion demands made directly to them and their families.
- Consider filing a personal report if you are caught up in a breach. This helps regulators and law enforcement collect evidence; helps to determine an appropriate level of response (if no one says anything, then it’s hard to convince a court that real harm was done); and helps the authorities demand higher cybersecurity standards in future.