Remember the DDEAUTO vulnerability?
DDEAUTO, short for automatic dynamic data exchange, is a command you can put right inside the data of an Office file to get it to pull data out of another file.
According to Microsoft’s official documentation, DDEAUTO is only supposed to work within the same app, or between two apps that are already active:
DDEAUTO argument-1 argument-2 [argument-3] [switches] [. . .] Description: For information copied from another application, this field links that information to its original source file using DDE and is updated automatically. The application name shall be specified in argument-1; this application must be running.
For example, you could have a Word report that pulled in the latest sales figures “live” from an Excel spreadsheet, provided you had both Word and Excel open already.
But researchers found that there was an undocumented feature in the DDEAUTO function whereby it could start any application already installed on your computer, such as the command shell CMD.EXE.
Having fired up this second program, the DDEAUTO function could be used to run a script specified inside the DDEAUTO command itself, instead of reading data from an existing file, as intended.
In other words, a crook could embed malware, in the form of a Powershell or other script, right in the data of a Word document or an Excel spreadsheet, and just opening the file would launch the malware command – without waiting for you to open an attachment, download a file or enable Word macros.
In short, remote code execution, or RCE.
Fortunately, you’d get two DDE warnings before the malicious script would run, but they weren’t warnings that anyone had previously learned to associate with malware.
First, this:
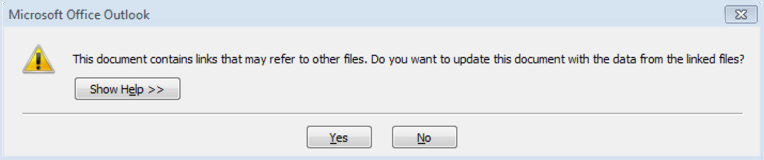
Followed by something along these lines:
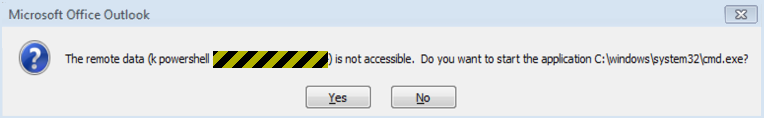
Microsoft demurred over fixing this bug, describing it as a by-design feature – which it was, except for failing to enforce the restriction stated in the Microsoft Developer Network (MSDN) documentation, namely that “[the other] application must [already] be running”.
Cybercrooks quickly learned to exploit DDEAUTO as yet another route for introducing malware – one that few users were trained to look out for and avoid.
Sophos products block DDE attacks under the following names:
- CXmail/OffDDE-*: emailed attachments and booby-trapped messages.
- Troj/RtfDDE-*: booby-trapped RTF files.
- Troj/DocDl-DJV: DDE attacks that try to download additional malware.
Change of heart
The good news is that Microsoft seems to have had a change of heart, at least in part.
I didn’t notice the details until now – as a macOS user, I get away without needing either Windows or Office in daily life! – but it turns out that downloads published in the December 2017 Update Tuesday included ADV170021, a so-called Microsoft Office Defense in Depth Update:
Microsoft has released an update for Microsoft Office that provides enhanced security as a defense-in-depth measure. The update disables the Dynamic Update Exchange protocol (DDE) in all supported editions of Microsoft Word.
Unfortunately, this isn’t a complete patch against your DDEAUTO problems, because it’s specific to the Word app, rather than generic to all the apps in the Office suite.
If you want to block DDEAUTO in other Office apps you will need to follow the app-specific registry hacks detailed in the Microsoft Office Security Advisory 4053440.
Nevertheless, this ADV170021 patch is a welcome change that introduces the following registry entry for Word:
HKEY_CURRENT_USER\Software\Microsoft\Office\<version#>\Word\Security\AllowDDE = 0
The default value, as indicated above, is zero, meaning that DDE is turned off altogether.
If that doesn’t work for you, you can revert to the old, insecure behaviour by setting AllowDDE = 2, allowing all DDEAUTO commands issued from inside Word.
For a middle ground, AllowDDE = 1 sets the as-originally-documented behaviour, so that DDEAUTO is allowed, but only between apps that are already running.
That means you can still hook your Word documents up to Excel spreadsheets for financial and similar data, but crooks can’t send in documents from outside to trick Word into running dangerous external programs such as CMD.EXE and PowerShell.

Laurence Marks
Since
> as a macOS user, I get away without needing either Windows or Office in daily life!
you probably didn’t realize that
> start any application already installed on your computer, such as the command shell CMD.EXE.
doesn’t work any more either.
The latest update eliminates CMD.EXE. Like it or not, if you want to use a shell, you have to use Powershell. (like choosing between Bash, Bourne, Korn, or csh). And like the situation you describe, Windows does provide a workaround to get CMD.EXE back for those who simply must have it.
Paul Ducklin
I have Windows 10 Fall Creators Edition and CMD.EXE is still present, large as life. This is a pretty-much-vanilla install. I didn’t do anything special for CMD to appear – IIRC it was “just there”. There isn’t a default menu item to launch it with a click, but that means nothing to a crook who simply wants/expects/needs it to be around.
Here is a running instance of CMD.EXE finding itself:
Microsoft Windows [Version 10.0.16299.125]
(c) 2017 Microsoft Corporation. All rights reserved.
C:\Users\duck>dir c:\CMD.EXE /s
Volume in drive C has no label.
Volume Serial Number is NNMN-MMNM
Directory of c:\Windows\System32
2017-09-29 13:41 272,896 cmd.exe
1 File(s) 272,896 bytes
Directory of c:\Windows\SysWOW64
2017-09-29 13:42 226,304 cmd.exe
1 File(s) 226,304 bytes
[. . . .]
C:\Users\duck>
Even if CMD.EXE weren’t there, there are plenty of other interesting pre-installed apps that I could launch to Do Bad Stuff On Demand…
(When I say “I don’t need Windows in daily life” I don’t mean I don’t have Windows – for article screenshots alone I need an up-to-date VM; for research I need other versions as and when.)
Laurence Marks
I believe you still have CMD.EXE. I didn’t lose mine until a few days ago. I have the 1709 Version of Windows Pro X64, Build 16299.125. I expect different builds are seeing the update at different times.
Microsoft first piloted this 13 months ago. See
[link removed]
Here’s the support article from Microsoft six weeks ago stating that everyone will see the replacement:
[link removed]
Your competitor pointed out a year ago that attacks have been moving from CMD.EXE to POWERSHELL.EXE:
[link removed]
Paul Ducklin
DDEAUTO attacks I’ve seen have typically used both PowerShell and CMD.EXE. I don’t think that’s of necessity, but rather for convenience – CMD.EXE is used as a wrapper to launch PowerShell and then stay running, which IIRC has the handy side effect of suppressing an error message that you would otherwise see.
So I’m not suggesting that attacks in general haven’t moved to PowerShell – I think we’ve covered the role of PowerShell malware plenty of times ourselves – just that CMD.EXE has been handy in DDEAUTO malware. But as far as I know, it’s not a requirement for a DDEAUTO attack.