Understandably, most news stories in cybersecurity focus on attackers’ behaviors and how they are advancing or changing for maximum damage. While this is important intelligence for defenders to have on a daily basis, and is covered in depth in our new Sophos 2022 Threat Report, it’s equally important to reflect on where we are making progress.
The end of the year seems to be the time when we see the greatest impact of everyone’s hard work to defeat the bad guys.
Most recently we observed BlackMatter ransomware announcing “project is closed.” The operators implied that some of their team members were missing, perhaps related to the recent arrests by Europol and others.
We have heard this all before, though, and “closed” is rarely as final as it sounds. Ransomware-as-a-service is simply the service. Affiliates who buy the service and do the actual hacking simply seek out new networks to affiliate with and continue with their crime sprees unabated. Meanwhile, the operators, or original creators, of the ransomware that “closed,” will likely re-emerge under a new name (more on this later).
Calling it quits
BlackMatter’s announcement comes hot on the heels of the news that REvil, another ransomware-as-a-service group, officially called it quits on Oct.18, 2021.
The REvil news is an example of your typical cyber-drama: one of the co-founders, named “Unknown” (memories of Abbott and Costello here) disappeared and no one seems to know if he was arrested or exit-scammed (the practice of taking all the money and running without paying any debts and obligations.) Most money is on the latter.
The other co-founder, “0_neday,” appeared to be attempting to resurrect the service after a three-month hiatus but got spooked when the U.S. government took over the dark website used to leak stolen data. For a group known for its braggadocio, REvil appears to have gone out with a whimper.
While REvil was one of the most active ransomware groups in the first half of 2021, it was only a year ago that we saw the last attacks of the previous most prolific ransomware group, Maze.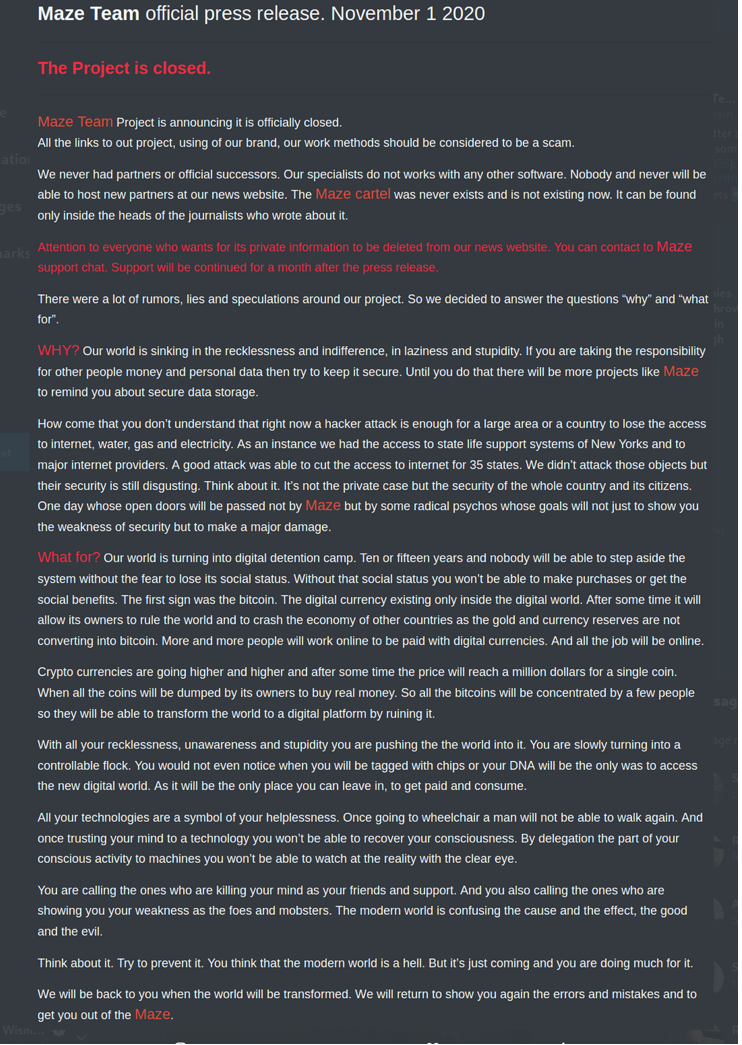
Maze folded on Nov. 1, 2020. The note, which at best could be called a screed declared that the “cartel” was officially closed. It is in FAQ-style, and the operators also tried to explain their behavior by complaining how vulnerable companies entrusted with sensitive information are ripe for the picking and how the world is turning into a “digital detention camp.”
Maze changed the ransomware threat landscape by being the first group to steal information for extortion purposes in addition to solely encrypting it and demanding a ransom.
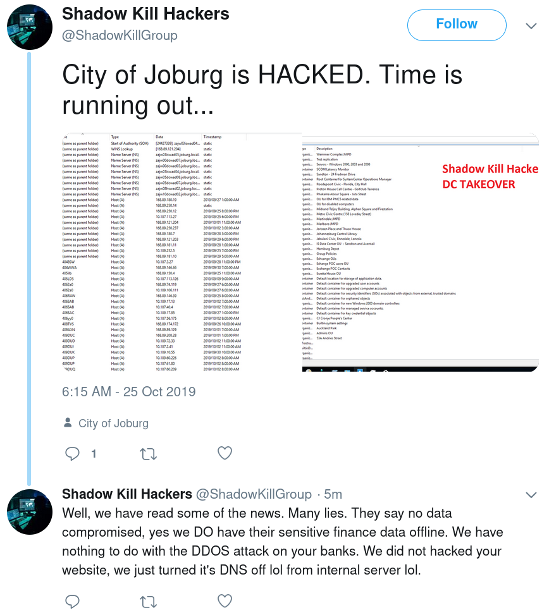
Maze appears to have been inspired by Shadow Kill Hackers, another criminal group that attempted extortion. In late October 2019, Shadow Kill Hackers broke into the City of Johannesburg’s network, stole sensitive resident information, and demanded money to not release the information publicly.
The revolving door of ransomware
We have made a ton of progress fighting cybercrime, more often than not in the fourth quarter of every year, including 2021. The pace of prosecutions, identification and attribution is finally maturing to a point where it is making a difference. However, this is only the beginning, and we can’t let our guard down because, as evidenced below as soon as one ransomware groups fades from the spotlight, another one appears.
For example, in last year’s Sophos 2021 Threat Report, all the buzz was about Maze ransomware and how it had presumably refined the tactic of using extortion to increase the payouts from victims.
Half a year later, Maze was almost forgotten; the security industry had moved on to studying how REvil had furthered the technique. Before we knew it, REvil was also a thing of the past, and now Conti ransomware and others lead the way.
New code or just a new coat?
The real question is, is there any difference? Cybercrime abhors a vacuum. Where one criminal forges a new path, another is happy to steal the idea and go one better.
Every year, a seemingly different set of thugs has held innocent victims to ransom and, oddly, many of them appear awfully similar to the previous bunch.
Whether they are one and the same or are simply ambitious up and coming opportunists is irrelevant. In the end they are out there, they are aiming to rob us blind, and they are increasingly bold in their actions. The industry is making progress, but the urgency of the message to set up protocol and defenses isn’t reaching every potential ransomware target.
The way forward
Some key ways to end ransomware include: stop paying ransoms, learn from the security mistakes of others and increase vigilance and security protocols to continue to raise the bar for the attackers. As the difficulty of compromise increases, so does the cost. This reduces the number of adversaries, which in turn makes our collective actions more effective at reducing their impact.
We’ve made incredible progress in recent years. We’ve removed browser plugins, automated browser patching and encrypted close to 95% of internet communications. This has seriously reduced the risk for average internet users in almost all aspects of modern life.
We hope the Sophos 2022 Threat Report contributes to this trend. Our team compromises some of the most dedicated and passionate security researchers in the world and we spent months working together to identify the most important trends, changes and tactics employed by those who wish to harm us.
Together we can make a difference and the evidence of that is already clear. Let’s make 2022 more secure than any time in recent memory.