A new Sophos research study of 3,000 cybersecurity/IT leaders across 14 countries reveals that today’s reality is a two-speed cybersecurity system with adversaries and defenders moving at different speeds. It also provides valuable insights into how organizations can get ahead of attackers in 2023. Download the full report here.
Adversaries Are Accelerating
As reported in the Sophos 2023 Threat Report, one of the most significant changes in the threat landscape over the last year has been the transformation of the cybercriminal economy into an industry unto itself, with a network of supporting services and well-established, professionalized approaches to operations.
Just as technology companies have shifted to “as-a-service” offerings, so has the cybercrime ecosystem, lowering the barriers to entry for would-be cybercriminals. Together with the growth in the use of automation technologies and constant adaptation, the “as-a-service” model has enabled threat actors to accelerate the volume, speed, and impact of their attacks.
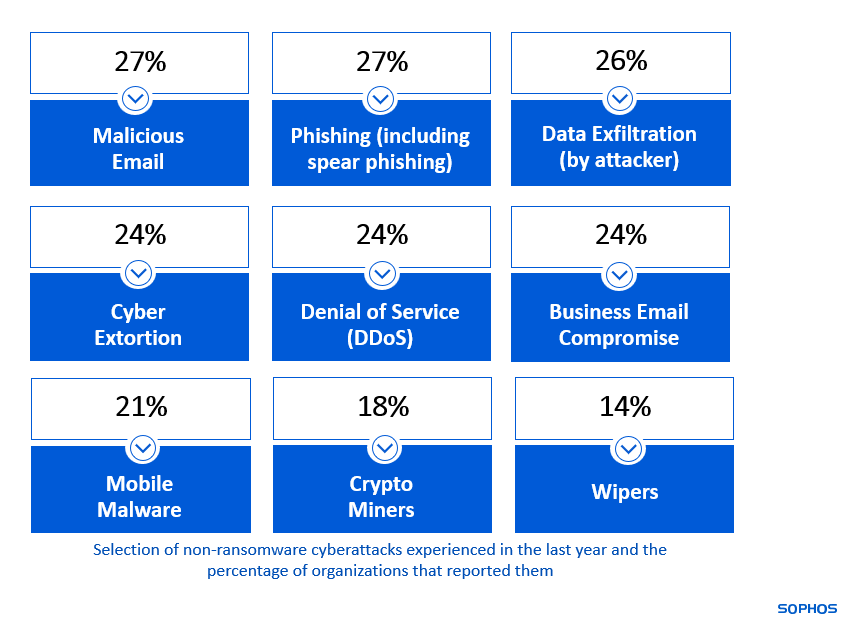
The result is that adversaries can now execute a wide range of sophisticated attacks at scale. 94% of organizations experiencing a cyberattack of some form in the last year, and while ransomware was the most widely reported attack, organizations experienced many other threats.
One of the largest cyber risks for organizations today is active adversaries, threat actors who adapt their techniques, tactics, and procedures (TTPs) on the fly using real-time hands-on-keyboard actions in response to actions by security technologies and defenders, and as a tactic to evade detection. These attacks, which often result in devastating ransomware and data breach incidents, are among the hardest to stop.
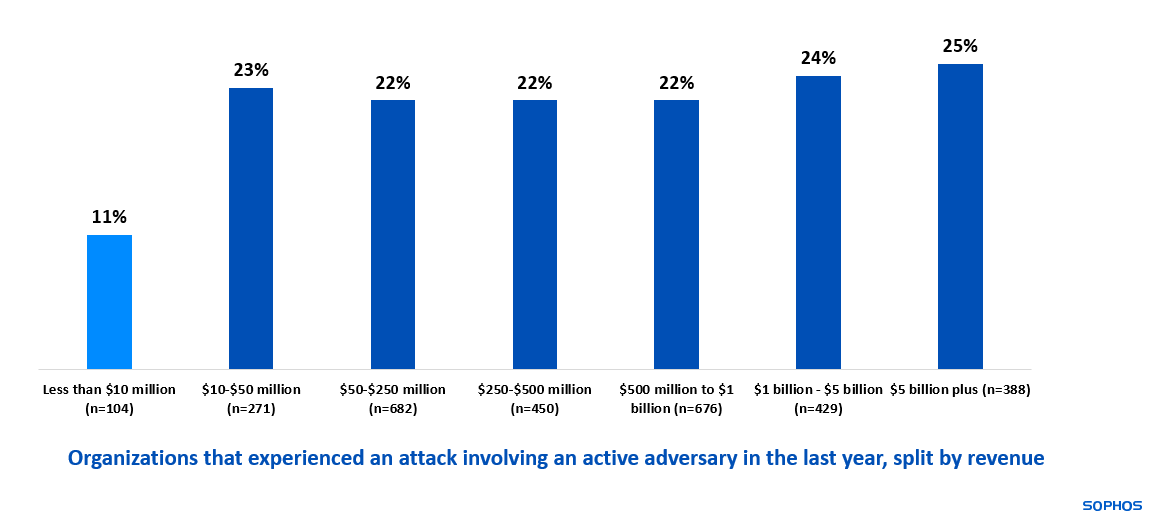
23% of respondents reported that their organization experienced an attack involving an active adversary attack last year. The attack rate was consistent regardless of organization size, varying by only two percentage points across all organization size segment splits.
Interestingly, for organizations with less than $10 million in annual revenue, the rate of reported active adversary attacks dropped to just 11%, which may indicate that attackers are deliberately focusing on targets with deeper pockets. Detecting active adversaries requires a high level of skill and it is likely that the actual rate of incidents is even higher.
Reflecting the potential devastation of these attacks, 30% of respondents reported that active adversaries are one of their top cyberthreat concerns for 2023.
Defenders Are Unable To Keep Up
Slowed by a shortage of expertise, an overwhelming volume of alerts, and too much time spent on incident response, defenders are fatigued and falling behind.
93% of organizations find the execution of essential security operations tasks “challenging,” including identifying signals from noise, getting the context around them, and remediating alerts in a timely manner.
Reflecting these difficulties, the median time to detect, investigate and respond to a security alert is nine hours for organizations with 100-3,000 employees, rising to 15 hours for organizations with 3,001-5,000 employees, likely reflecting the increased complexity of their operating environments. While the majority of alerts will not require the full three-step process, it’s clear that the human overhead of threat response is considerable.
Operationally, defenders lack confidence in their processes, with security tool misconfiguration identified as the top perceived security risk in 2023, followed by zero-day threats and lack of in-house cybersecurity skills/expertise.
As a result of these headwinds, over half (52%) of cybersecurity/IT professionals say that cyberthreats are now too advanced for their organization to deal with on their own, rising to 64% among small businesses (100-250 employees).
The Two-Speed System Has Major Business Consequences
The direct financial repercussions of a cyber incident are huge and already well known, with the average cost to a small or mid-sized organization to remediate a ransomware attack coming in at $1.4 million. These incident clean-up costs are, however, just part of the story.
The time and effort needed to deal with cybersecurity results in reduced capacity for IT program delivery, with 55% of respondents reporting that dealing with cyberthreats has negatively impacted the IT team’s work on other projects. Furthermore, the urgent and unpredictable nature of cybersecurity also gets in the way of business-focused efforts: 64% wish the IT team could spend more time on strategic issues and less time on firefighting.
The lengthy time spent on detecting, investigating and remediating security alerts also has a financial impact. With the average IT Security Specialist salary in the U.S. currently just shy of $100,000 per year [www.indeed.com], the resource cost for each security alert investigation is considerable.
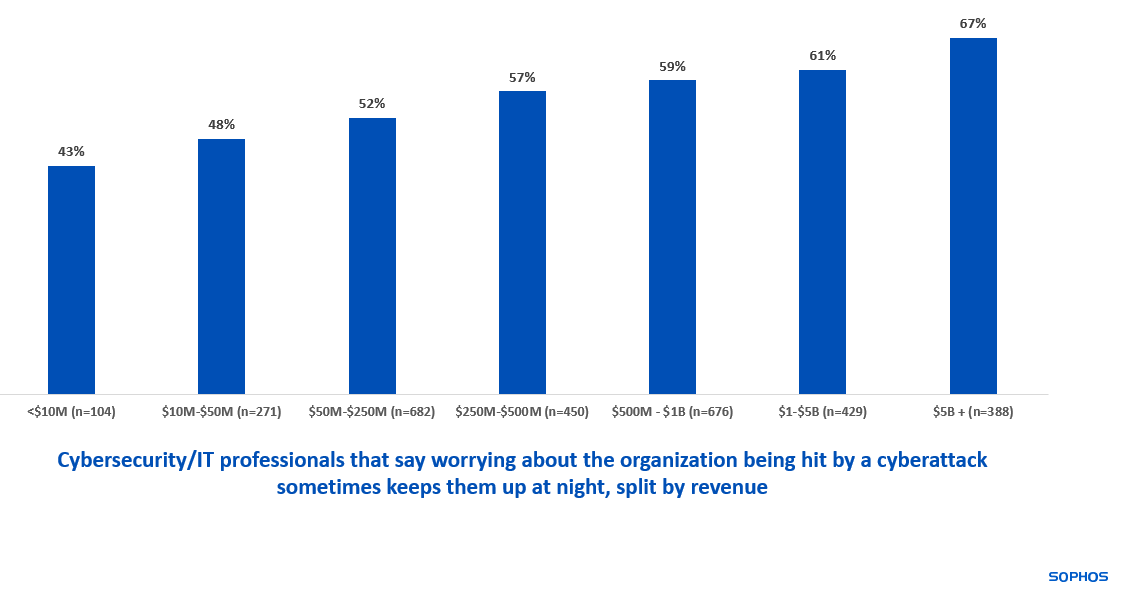
The situation also creates a heavy burden on employees. 57% of IT professionals say that worrying about the organization being hit by a cyberattack sometimes keeps them up at night. The propensity for cybersecurity worries to stop people from sleeping increases steadily as organization revenue grows, starting at 43% of those in organizations with less than $10 million annual revenue and rising to 67% in organizations that turn over $5 billion or more.
Burn out is a major issue in cybersecurity. Too many alerts and having too much to do puts considerable stress on employees. Over-stretched teams are more likely to miss important signals, adding further pressure. Ultimately, people will eventually break.
Accelerate The Defender Flywheel
Enabling defenders to overtake attackers in the 2023 cybersecurity race requires a comprehensive, but straightforward approach.
Firstly, organizations need to set up an incident response process that can scale, through minimizing the attack surface and the volume of alerts that require attention and optimizing response time by leveraging specialist services.
Next, they need to implement adaptive defenses that automatically adjust to the situation. This allows them to slow down adversaries and buy defenders time to respond.
Finally, they also need to set up a virtuous cycle that combines technology and human expertise to turbo-charge defenses, enabling an increase in speed, efficacy, and impact. Together they accelerate the defender flywheel, enabling them to pull ahead.
Strong Shields Are Essential
The quality of your cybersecurity technologies is paramount, and security controls should:
- Optimize prevention, automatically detecting and stopping as many threats as possible early in the attack chain. In doing so, you reduce the risk to the organization while freeing up defenders to focus on fewer incidents.
- Reduce exposure by making it easy to ensure security investments are correctly and optimally deployed and avoid misconfiguration issues.
- Disrupt adversaries. Technologies that automatically detect and disrupt adversarial activity frustrate attackers while buying defenders time to neutralize the incident.
Address the Root Cause with People and Technology
Alongside strong shields, timely, well-informed, and well-executed root cause remediation is also essential. Defenders should use the valuable time that their shields buy them to investigate and respond to attacks.
As the research has shown, adversaries do not follow a single path. By leveraging telemetry from across the security environment, using the security controls organizations already have, defenders can see and respond to threats faster while increasing return on existing investments.
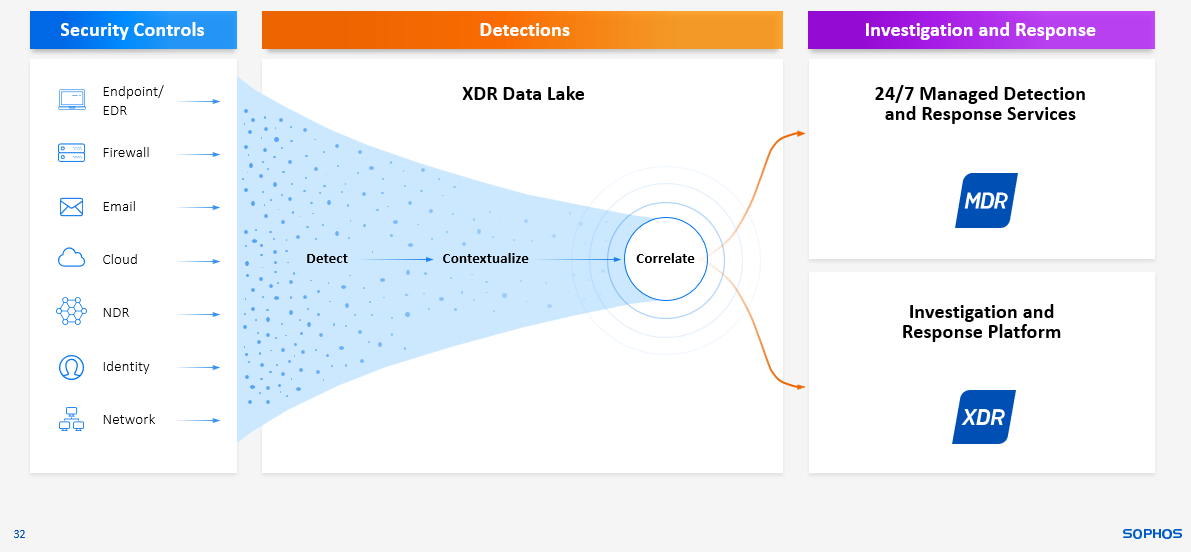
Finding malicious activity among the benign alerts is often akin to hunting for the needle in the haystack (or even the needle in the stack of needles). Processing the signals through an Extended Detection and Response (XDR) platform that adds contextual insights and correlates related alerts enables in-house defenders to quickly focus on what’s important.
Investigation and response can be performed via an XDR platform by the in-house team. Alternatively, organizations can outsource the detection, investigation, and response work to a specialist Managed Detection and Response (MDR) service.
Accelerating The Defender Flywheel
Once a flywheel starts spinning at high speed, it wants to keep spinning. The more force behind a flywheel, the faster it goes. Organizations can accelerate their cybersecurity flywheel by combining security technologies and human expertise. Strong security controls reduce the volume of alerts that defenders need to deal with, enabling them to focus on neutralizing attacks and elevating their security posture. In turn, this increases the efficacy of their security controls, creating a virtuous circle.
Organizations Plan to Adopt Detection and Response Capabilities
The survey revealed that most organizations plan to add threat detection and response solutions to their security stack within the next 12 months.
Over three quarters (78%) plan to add Endpoint Detection and Response (EDR) and/or Extended Detection and Response (XDR) tools within the next year while 44% plan to engage Managed Detection and Response (MDR) services. With a shortage of in-house cybersecurity skills/expertise listed as one of the top three perceived cyber risks for 2023, organizations are wise to look to third-party experts for support.
For a deeper dive into the survey results, download the full report here.
Sophos Can Help
Sophos provides the services and technologies that enable organizations to accelerate the defender flywheel and move ahead of adversaries.
Our endpoint/EDR, firewall, email, network, and cloud solutions deliver the strongest shields, slowing down attackers and giving defenders the time and insights they need to respond:
- Optimize prevention: Sophos blocks 99.98% of threats automatically out of the gate, minimizing risk and enabling defenders to focus on fewer incidents that require human intervention
- Reduce exposure: Optimal protection settings are deployed automatically from day one, eliminating security gaps. Built-in Account Health Checks highlight missing software and configuration issues that can lead to avoidable infections
- Disrupt adversaries. Adaptive Attacker Protection immediately activates heightened defenses when a “hands-on-keyboard” endpoint intrusion is detected, frustrating attackers and buying defenders time to respond
The more defenders see, the faster they can act. We use detections from across the security environment, integrating telemetry from both Sophos and third-party security controls to accelerate detection and response, and increase return on existing security investments.
The Sophos MDR service brings together over 500 experts to hunt for, investigate and respond to active adversaries and other attacks on your behalf 24/7/365. With an average threat response time of just 38 minutes, Sophos MDR is considerably faster than the in-house team average reported in the survey.
Alternatively, organizations can use the Sophos XDR platform that includes full EDR functionality to investigate and respond to attacks directly or work in collaboration with the Sophos MDR team.
For more information, visit www.sophos.com or speak with a security advisor.