Visibility is key to stopping an advanced cyberthreat before major damage is done: if you can see intrusion attempts, unauthorized network entry, and other suspicious behaviors as they’re happening, it’s much easier to quickly jump in and neutralize them.
Visibility is key to stopping an advanced cyberthreat before major damage is done: if you can see intrusion attempts, unauthorized network entry, and other suspicious behaviors as they’re happening, it’s much easier to quickly jump in and neutralize them.
And while advanced technology solutions – including next-gen endpoint protection and firewalls – are critical layers of defense, stopping advanced, human-led attacks requires 24×7 eyes on glass.
The good news is that most organizations are already gathering much of the raw telemetry needed to see these risks via their existing security investments.
Endpoint, firewall, identity, email, cloud, and network solutions all provide valuable insights that enable skilled security analysts to detect and respond to sophisticated attacks.
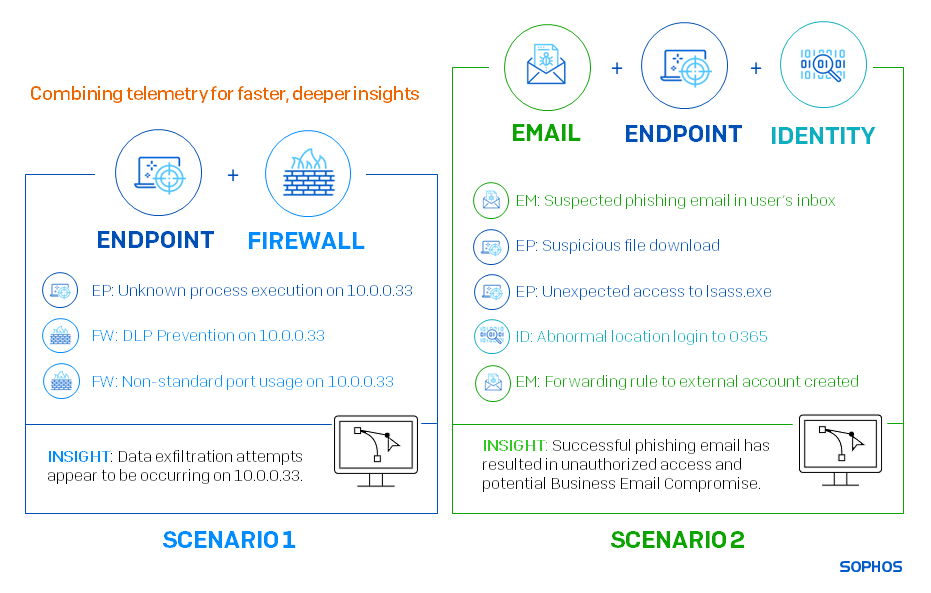
Combining telemetry for faster, deeper insights
Each telemetry source is useful individually. However, the more signals threat analysts can bring together from across the environment, the more they see and the faster they can react. Let’s look at a couple of examples of how we can combine telemetry sources to accelerate threat response.
As we can see, the endpoint signal in the first scenario and the email signal in the second scenario are both suspicious on their own. However, together with data from the firewall, identity telemetry, and other insights, analysts can much more confidently identify data exfiltration attempts in the first scenario and Business Email Compromise in the second.
The defender challenge: telemetry complexity
Achieving actionable visibility from security telemetry is a specialist skill. While many technologies generate security alerts and insights that are useful to highly trained analysts, leveraging the information is very challenging.
Defenders face:
- Huge volumes of data
- Myriad, inconsistent severity score ratings (1-10, 5-1, High/Med/Low, etc.)
- Different types and quantities of data from each provider
- Highly varied reporting formats
As a result, it’s almost impossible for most organizations to correlate data and identify issues in a timely manner. IT teams end up overwhelmed by alerts, unable to identify which ones are related, and what to prioritize.
The Sophos MDR approach
At Sophos MDR, the more we see, the faster we act. We gather telemetry from across our customers’ security environments, using signals and alerts from:
- Sophos’ award-winning endpoint, email, network, firewall, and cloud security solutions
- Third-party technologies including Amazon Web Services (AWS), Check Point, CrowdStrike, Darktrace, Fortinet, Google, Microsoft, Okta, Palo Alto Networks, Rapid7, and many others
- Any combination of the two
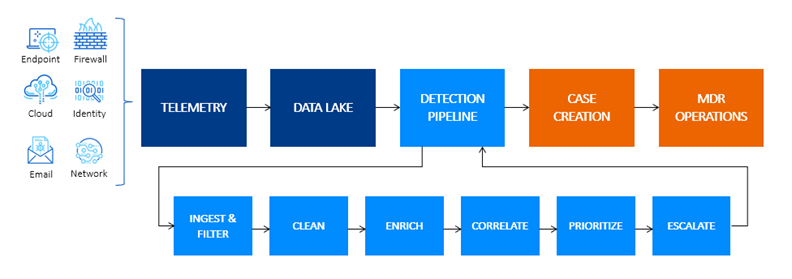
Next, we convert this huge volume of security telemetry into actionable, prioritized insights for our analysts to investigate using the Sophos MDR Event Flow.
The telemetry goes into our data lake and is processed through the six stages of our patented detection pipeline:
- Ingest and Filter – Ingest telemetry and filter unwanted noise
- Clean – Transform data into normalized schema and map to MITRE ATT&CK®
- Enrich – Add additional third-party threat intelligence and business context information
- Correlate – Cluster alerts based on entities, MITRE ATT&CK categorization, and time
- Prioritize – Score alerts and clusters to rank in order of prioritization
- Escalate – Logic that escalates certain clusters into cases for investigation
 The clean, enhanced, correlated, clustered outputs are then passed to the experts in our MDR operations team for investigation and response.
The clean, enhanced, correlated, clustered outputs are then passed to the experts in our MDR operations team for investigation and response.
To give you an idea of the scale at which we do this: on a typical day, we process around 31 billion events and 358 million detections. These result in 367 cases that are then investigated by the team, leading to 47 escalations and one active threat.
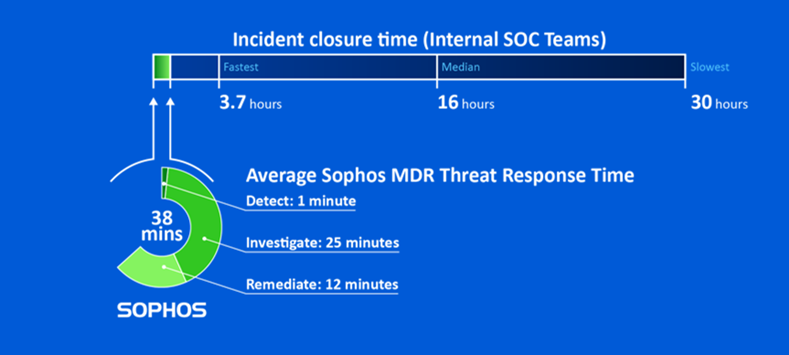
Leveraging cross-environment telemetry in this way helps Sophos MDR to detect and neutralize threats faster than anyone else. Our average threat response time is just 38 minutes, which is considerably faster than other security vendors and more than five times quicker than even the speediest in-house team.
Learn more
Visibility is vital for stopping advanced, human-led cyberattacks early in the attack chain. Fortunately, every organization is already generating security telemetry that can be used by skilled analysts to detect and respond to attacks. Sophos MDR leverages this data, applying our unique Security Event Flow process and unparalleled human expertise to quickly identify and neutralize threats before damage is done.
To find out more about Sophos MDR and how we use cross-environment detections to accelerate threat response, speak to our security specialists today.