For our roundup of July, 2020’s Patch Tuesday release, Microsoft today published a few patches that need quick attention. Microsoft fixes 123 vulnerabilities across their product lines this month including 20 classified as Critical, and a whopping 103 flagged as Important.
As usual all the additional details can be found in the Security Update Guide Release Notes and users can download patches manually from the Microsoft Security Update Catalog.
The company fixed a total of 32 potential remote-code execution (RCE) vulnerabilities in what has become a list of the usual suspects (such as the Jet database engine, Windows .lnk shortcut files, the GDI+ graphics subsystem, and the Internet Explorer browser).
Hyper-V and its graphic layer (RemoteFX vGPU) received a lot of attention this month when researchers discovered a series of bugs that could give an attacker an avenue to an RCE. The other major announcement involves a bug that exists in nearly every existent version of the Windows DNS server software. The memory corruption vulnerability in Windows DNS Server service, in all Windows Server versions. Microsoft released fixes for some of these bugs on the out-of-support Windows 7 and Server 2008 platforms.
Beyond the RCE bugs, Microsoft issues fixes for 64 elevation-of-privilege (EoP) bugs, in Windows services (Windows Error Reporting, COM) and kernel driver modules (WSL, UPnP, ALPC, Graphic components).
Here’s our breakdown of the classes of vulnerabilities that Microsoft addressed. Each bar’s colors represent different products that fall under the respective category at left.
This key represents the products that are reflected in the above chart, which should give an indication as to just how broad the scope of a Patch Tuesday can be. These data points are based on the component names that Microsoft provides to MAPP partners, and they can be confusing about what they address: for example, the table lists “Microsoft Office” in some cases, and specific Office applications in others.
In addition, Adobe released four updates to Adobe products, timed to coincide with the Patch Tuesday releases. Included among these releases was an update to the Adobe Download Manager that fixes a serious code execution bug.
SophosLabs has investigated some of the more interesting vulnerabilities that we received exploit details about. Here are some highlights this month.
Hyper-V RemoteFX vGPU RCE
CVE-2020-1032,CVE-2020-1036,CVE-2020-1040,CVE-2020-1041,CVE-2020-1042,CVE-2020-1043
RemoteFX is a set of features first introduced in Windows Server 2008, aimed at improving the graphics in remote sessions (for example, while using RDP). Among those features was RemoteFX vGPU, also referred as GPU Pass-through, which binds virtual machines to one or more physical GPUs on the host in order to benefit directly from the GPU’s computation capability.
It is an interesting target for vulnerabilities, especially in the context of a virtual machine guest-to-host escape – which to this day remains covered by a Microsoft bug bounty that pays out as much as $250,000 for Tier-1 bugs.
This month, Microsoft patched a total of 6 RCE bugs in RemoteFX, all ranked as Critical. However, no technical details were provided by the company. It should be highlighted that the fix Microsoft provides disables RemoteFX altogether; Microsoft does not patch the bug to prevent its exploitation. This comes after more than a year since Microsoft deprecated RemoteFX and removed it from the Hyper-V GUI (though it is still available through PowerShell cmdlets Enable-VMRemoteFXPhysicalVideoAdapter / Add-VMRemoteFx3dVideoAdapter ).
Hyper-V DDA is now the proper (and only) way to assign direct device access to VMs with Hyper-V.
Windows DNS Server RCE
Microsoft patched a severe bug in Windows DNS Server, referred to as CVE-2020-1350, an integer overflow vulnerability in the parsing of DNS signature queries (RR SIG records).
This vulnerability seems to impact Windows Servers from 2019 all the way back to Windows Server 2008 (SP2) and Windows Server 2008 R2 (SP1). Microsoft has issued a special KB entry and a patch despite those releases being EoL-ed last January 14th. One of the likely reasons for releasing a patch on an officially-unsupported platform would be that the exploit could be wormable.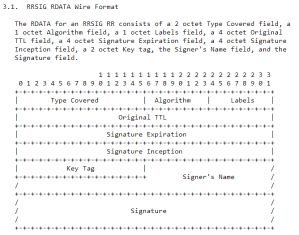
The issue comes from the parsing on SIG RR records, in the service dns.exe which fails to properly validate the length in the record packet, a 16-bit field entirely controlled by the attacker. During the attack they add this field to some additional constant values, to allocate that resulting size from the process heap. So by providing a large length, an attacker can make the WORD value overflow.
The controlled length is then used as the size argument provided to memcpy-ed, allowing to overwrite the allocated heap memory beyond the intended boundaries. Shaping the heap in a way to transform this heap overflow into a code execution is very likely too, as DNS offers many by nature a great number of record types controllable by an attacker.
This critical vulnerability (CVSS 10.0) is therefore likely to be exploited in the future, although for latest versions of Windows Server (2016, 2019) the attacker would face other problems during the exploitation process to successfully (and reliably) execute code on the remote system.
Although as usual applying patches should be the priority, a workaround can be used to prevent the integer overflow being triggered, by editing the registry HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters and set the key TcpReceivePacketSize to a maximum value of 0xFF00, and then restarting the DNS service. Refer to Microsoft Guidance for additional details.
Remote Desktop
Microsoft Remote Desktop Client (mstsc.exe) has been targeted once again, and patched under CVE-2020-1374. The bug in this case is an integer overflow that allows a heap corruption which, if exploited successfully, results in code execution with the privilege of the user running the executable.
This vulnerability can be triggered within the Media Container Dynamic Virtual Channel feature, and follows the well-known path of alloc(controlled_size) followed by a memcpy() to the allocated location. As such, Microsoft deems its exploitation as More likely.
And the code execution would be entirely remote, as this vulnerability could be exploited by either an already compromised RDP server tricking an user to connect back, but also as a MITM attack like ARP poisoning.
Usual suspects
Several other components got patched this month:
- Microsoft Office fixed an Elevation of Privilege vulnerability (CVE-2020-1025) due to an improper OAuth token validation in Microsoft SharePoint Server
- Skype for Business Server allows an attack to tamper with their own token resulting in EoP.
- A Remote Code Execution vulnerability was discovered and patched this month in VBScript (CVE-2020-1403). As it targets specific users who needs to visit a specific crafted page, such vulnerability would not immediately result in a full system compromise, but instead provide access onto a targeted computer, with associated privileges, allowing further horizontal or vertical escalation.
- Graphical components such as GDI+ (Remote Code Execution Vulnerability – CVE-2020-1435), Win32k (Elevation of Privilege – CVE-2020-1381, CVE-2020-1382) were patched, fixing vulnerabilities allowing complete takeover of the targeted system.
Although no vulnerability was reported as exploited in the wild, many vulnerabilities are rated as likable to be in a near future. Therefore, the simple precaution principle would dictate to patch as soon as possible, which is, regardless of any other layer of protection, always the best remediation.
How is Sophos responding to these threats?
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products.
|
CVE |
SAV |
IPS
|
|---|---|---|
| CVE-2020-1403 | Exp/20201403-A | SID:2302036 |
| CVE-2020-1350 |
SID:2303390 |
|
| CVE-2020-1374 | SID:2303388 | |
| CVE-2020-1147 | SID:2303387 |
How long does it take to have Sophos detection in place?
We aim to add detection to critical issues based on the type and nature of the vulnerabilities as soon as possible. In many cases, existing detections will catch exploit attempts without the need for updates.


