Thanks to Vikas Singh of SophosLabs for his work on the malware in this article.
B-r-e-x-i-t!
Not just in the UK but all over the world, it’s a word you can’t escape.
And it turns out it’s not just ‘the rest of us’ that are fascinated by/have strong feelings about/can’t stop arguing for or against this Brexit thing.
Malware writers are too…
In the bad old days before cybercrooks figured out how to make real money out of malware, they tended to let viruses loose for a range of different reasons, including to score political points, to cheer their favourite teams, to wreak havoc on society, to show off to imaginary friends, to celebrate anniversaries and birthdays and, in one infamous case, to tell us all, “Beer and tequila forever!”
Sometimes, the messages were overt – such as popup boxes, tunes playing, files trashed on specific days.
And sometimes they were hidden, buried like treasure inside the malware code itself so that if you didn’t know where or how to look, you’d miss out on the secret.
Well, the art of the hidden political malware comment isn’t dead!
In a number of recent attacks, SophosLabs has encountered a variant of the WannaMine malware family that was similar enough to other samples in the family that you could guess what it was going to do, but with a sneaky and unexpected change right at the end of the main malware script.
The WannaMine malware family
You may remember WannaMine from when it first showed up – it got its name because it could spread virally like the WannaCry ransomware did, which gave it the Wanna- part at the beginning, but instead of delivering ransomware, it stitched you up with cryptocoin mining software instead, thus the -Mine suffix in the name.
Actually, the WannaMine family of malware does a lot more than just cryptojacking, although it’s the mining code – which revs up your CPU, slows down your computer, steals your electricity, heats up your lap and keeps the cryptocoins for itself – that is likely to attract your attention.
Unlike ransomware, which jolly well wants you to know it’s there so you can get busy paying the blackmail money to get your files back, coinminers would prefer to remain unnoticed, because the amount of money they earn for the crooks is directly proportional to how long they keep running.
But coinmining is, for the most part, a CPU-intensive task that doesn’t play well with anything else on your system, such as your laptop battery, your CPU temperature, your electricity consumption and the speed at which all your other software runs.
While it’s busy, though, WannaMine malware variants typically try to do a bunch of other stuff in the background, such as:
- Sneaking through memory looking for credentials for already-logged in accounts.
- Cracking passwords for other computers on the network to spread further.
- Looking for computers on the network that can be broken into using the ETERNALBLUE exploit.
- Turning off Windows security settings.
- Carrying out DoS (denial-of-service) attacks.
- Looking for updates to itself so it can fetch the latest version of the malware.
Getting ready to attack
The last few lines of the main script set up the main part of the attack, something like this:
$mimi = ([WmiClass] 'root\default:Window_Core_Flush_Cach').Properties['mimi'].Value $a, $NTLM= Get-creds $mimi $mimi $ipsu = ([WmiClass] 'root\default:Window_Core_Flush_Cach').Properties['ipsu'].Value $i17 = ([WmiClass] 'root\default:Window_Core_Flush_Cach').Properties['i17'].Value $scba= ([WmiClass] 'root\default:Window_Core_Flush_Cach').Properties['sc'].Value [byte[]]$sc=[System.Convert]::FromBase64String($scba)
The PowerShell code above builds a load of data variables that include a mixture of data and code.
For example, the $mimi variable has an in-memory copy of the well-known Mimikatz program, a password harvesting and cracking tool commonly used by crooks once they’re inside your network.
The $scba variable is a downloader tool that can be used for fetching new files; ba refers to ‘base64 encoded’, because the $scba content is immediately base64 decoded to produce $sc, another in-memory copy of a program that, in a conventional world, would be saved on disk as a regular .EXE file.
You’ll also notice that the data is fetched using WMI, short for Windows Management Instrumentation, which means that the code and data used by this malware is buried inside the Windows WBEM database (short for Web-Based Enterprise Management).
In other words, even though the malware components are, strictly speaking, saved on disk, they aren’t visible as regular files that a regular program can read and analyse – the WBEM database is sort of like the Windows registry, but completely different.
(Your local WMI database files usually live in a directory called C:\Windows\System32\Wbem\Repository, if you are interested – but be really careful if you plan to mess with them by hand!)
Show me the Brexit
So, where’s the Brexit?
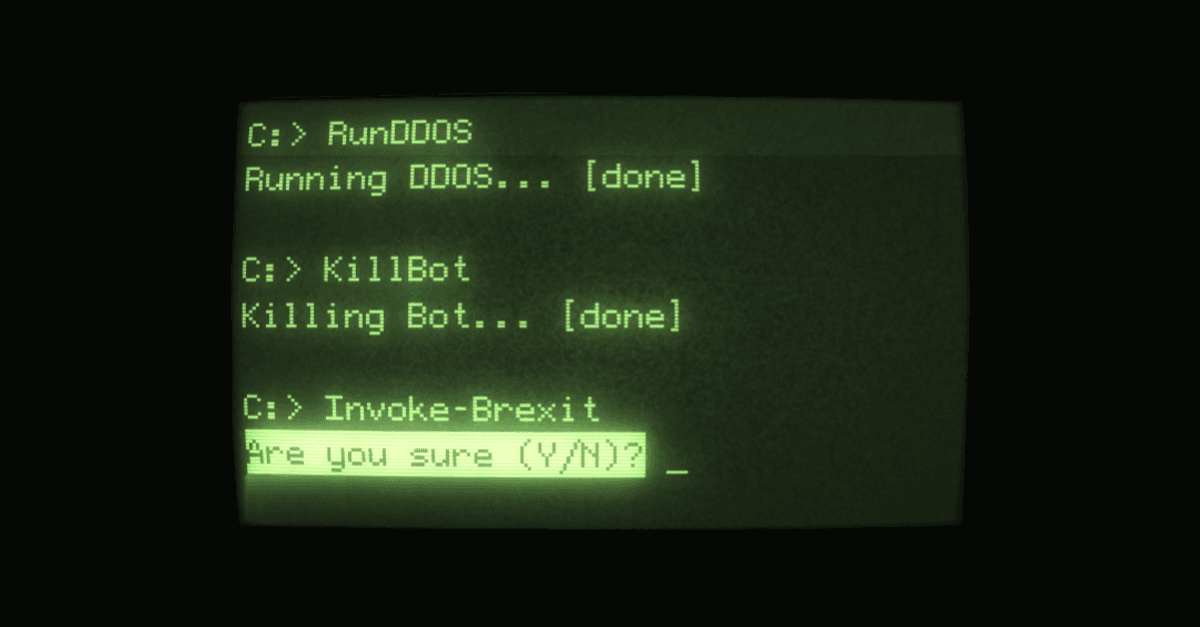
Right in the last line of the malware script, the virus writer calls their main ‘do-the-bad-stuff’ function.
Earlier in the code, they’re rather boring, using function names such as:
RunDDOS KillBot
But the parting shot in this one is a function called like this:
Invoke-Brexit -scccccc $sc -ipsu $ipsu -i17 $i17 -nic $nic -a $a -NTLM $NTLM
What we can’t tell you is whether the virus writer has embedded a secret message to imply that Brexit is a good idea, and we should get on with it…
…or whether they intended this code as a metaphor to invite us to infer that invoking Brexit is something best avoided.
We’re not going to get drawn into expressing a public opinion on real-life Brexit, but we are prepared to tell you that the virus writer’s Brexit is definitely not one you want!
J
Refreshing seeing an article without personal Brexit opinions, merely the facts. Great write-up!
zeke
Dear Paul,
A totally unrelated topic, as usual.
I have just visited google’s play store and was pleasantly surprised to see Intercept X being offered to Android users.
Excellent. :) I hope Intercept X is offered to Sophos Home (Mac) users soon. Fingers crossed! :)
Merry Christmas and a Happy New Year.
zeke