Thanks to SophosLabs expert Luca Nagy for the research behind this article.
In the world of computer security, a great deal of time and column inches are devoted to the extremes. At the extreme of simplicity, we have the immortal mystery of how to make basics like “don’t click on that email attachment” stick. At the other, we have the conundrum of how to avoid becoming collateral damage at the hands of complex, organised, highly evolved, state-sponsored threats.
As in many things, while the extremes are interesting they are dwarfed and separated by a vast and important middle, where most of the important work happens, and much of it goes unacknowledged.
Your 2019 next-gen protection doesn’t just need to stop this year’s most dangerous, as-yet-unseen threats. It needs to stop this year’s workhorses, schlubs and turkeys too. And the complete catalogue of last year’s threats. And the ones from the year before that. And the year before that, and everything else between that and the beginning of the history of malware.
The malware middle ground is an enormous army of malicious software journeymen, wallflowers and also-rans. They may not be as advanced as Emotet or as explosive as WannaCry, but they’ll bite you just as hard if you let them.
One such might-have-been is Matrix, a form of ransomware that sulks in the shadow cast by BitPaymer, Ryuk and GandCrab. You probably won’t encounter it, but if you do it could make your life very miserable indeed, and you’ll be glad that people like SophosLabs’ Luca Nagy were paying attention to it.
In 2018, Luca presented an extensive analysis of Matrix at the November Blackhoodie event.
Convergence
Like BitPaymer and Ryuk, Matrix is targeted ransomware. Instead of arriving in an email, like Locky or GandCrab, it arrives courtesy of a hacker, who breaks into your network and places Matrix on to as many vulnerable computers as they can.
Why? Because it pays. One guided Ryuk attack can rake in more than $100,000 from a single victim.
In a targeted attack, a criminal hacker:
- Gains entry to a victim’s network.
- Escalates their privileges until they’re an administrator.
- Uses their powerful access rights to overcome security software.
- Spreads and runs ransomware that encrypts a victim’s files.
- Leaves a note demanding payment in return for decrypting the files.
- Waits for the victim to contact them via email or a dark web website.
One of the signature features of targeted ransomware is the field’s convergence on a standard set of tools and tactics.
Matrix emerged in 2016, at the beginning of the trend for targeted ransomware. It’s been improved steadily since and the methods used by its operators have evolved too. Tactics that were unusual, or that made Matrix a bit different, have slowly been passed over in favour of a template common to almost all targeted ransomware.
For example, the malware has given up its use of an exploit kit to gain a foothold on a victim’s network in favour of the near-universal tactic of exploiting weak RDP credentials.
Until recently, victims were told to contact the malware’s operators using an instant messaging service. Since the messaging service disappeared in December 2018 the attackers have switched, like many other types of targeted ransomware, to simply using email.
Earlier versions of the malware also contained a ransom note that attempted to trick victims into believing their files had been locked by the FBI. That crude piece of social engineering has since given way to a lengthy, more matter-of-fact ransom note that’s part threat, part help file, and which could just as easily have come from SamSam or BitPaymer.
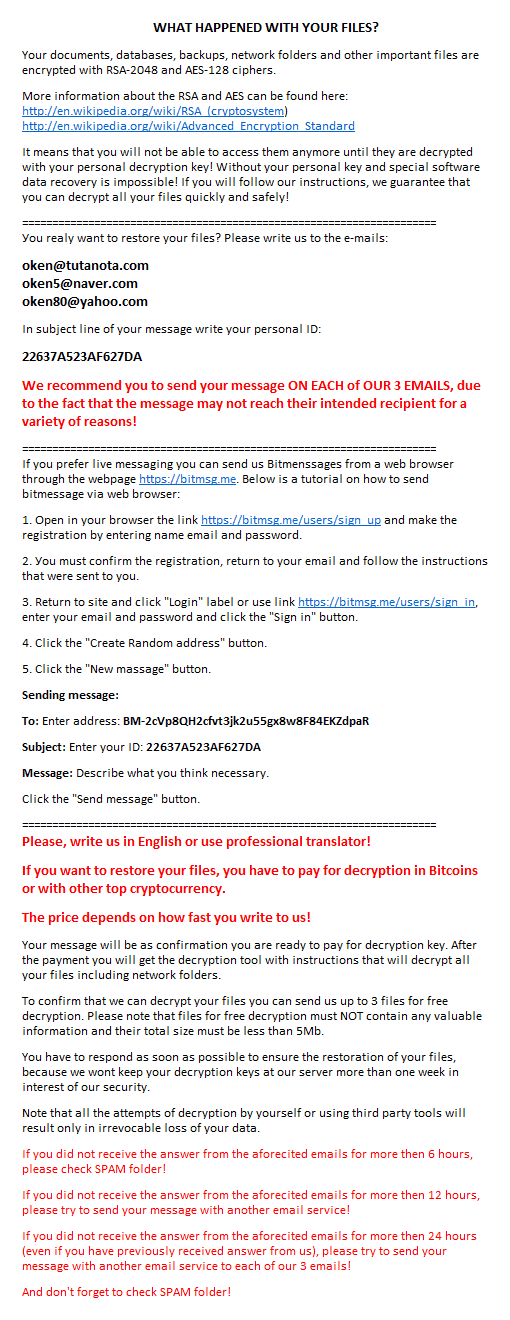
The convergence of targeted ransomware tactics is evidenced by the SophosLabs Targeted Ransomware Playbook, reproduced below, which compares five types of well known targeted ransomware and contrasts them with GandCrab, one of the most popular varieties of Ransomware‑as‑a‑Service (Raas).
| SamSam | Dharma | Matrix | BitPaymer | Ryuk | GandCrab | |
|---|---|---|---|---|---|---|
| Type | Targeted | Targeted | Targeted | Targeted | Targeted | RaaS |
| First appeared | 2015 | 2016 | 2016 | 2017 | 2018 | 2018 |
| Active | No | Yes | Yes | Yes | Yes | Yes |
| Infection vector | RDP (Exploit) |
RDP | RDP (Exploit) |
RDP | RDP | RDP Exploit |
| Victim size | Med/large | Small/med | Med/large | Med/large | Med/large | Any |
| Computers targeted | Any | Servers | Any | Servers | Servers | Any |
| Attack frequency | Med | High | Low | Med | Med | High |
| Regions affected | All | All | All | All | All | All |
| Decryption available | No | No | No | No | No | Some variants |
| Ransom currency | Bitcoin | Bitcoin | Bitcoin | Bitcoin | Bitcoin | DASH |
| Ave. ransom | $50k | $5k | $3.5k | $500k | $100k | $0.8k |
| Payment method | Dark Web | Email (IM) |
Email Dark Web |
Dark Web |
You can read more about the ransomware mentioned in this chart in our articles about SamSam, Ryuk, BitPaymer and the rise of targeted ransomware.
Enter the Matrix
The crooks behind targeted ransomware aim to make the extra effort they put into delivering their malware pay off in the form higher ransoms. By guiding their software into sensitive parts (or even all parts) of a victim’s network, they hope to cause crippling damage to an entire organisation.
Whereas a fire-and-forget ransomware like Locky or WannaCry will charge a fixed fee, targeted ransomware opens the door for crooks to vary their demands and offer victims “deals”. Some attackers offer to decrypt a few computers for free, to prove they can. Others will offer different price bands for decrypting different numbers of computers, and prices can shift up and down depending on what the attackers think they can get away with, how quickly victims pay, and so on.
Unusually, the Matrix ransom note doesn’t tell victims how much they’ll need to pay. To find that out, victims have to get in touch with the crooks using a number of email addresses.
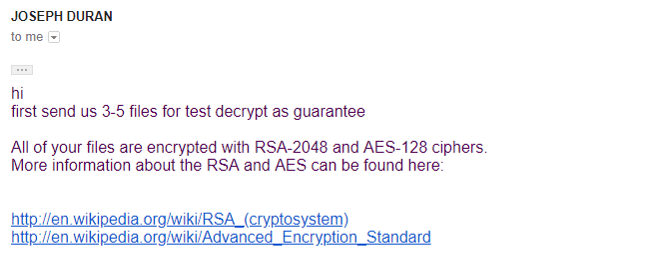
As part of her research, Luca posed as a victim of the ransomware and communicated, briefly, with its operators. The first email attempts to remove all hope for the victim by reassuring them of the strength of the encryption used in the attack:
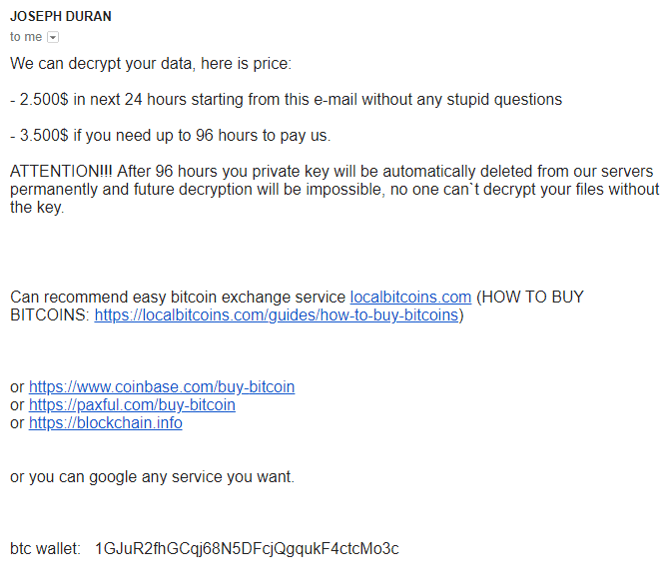
The next email includes the price. The crooks ramp up the social engineering with price incentives for early payment, threats, time limits and disdain for “stupid questions”. Unusually, the price is listed in US dollars rather than Bitcoin, perhaps in an attempt to insulate the crooks from Bitcoin price fluctuations.
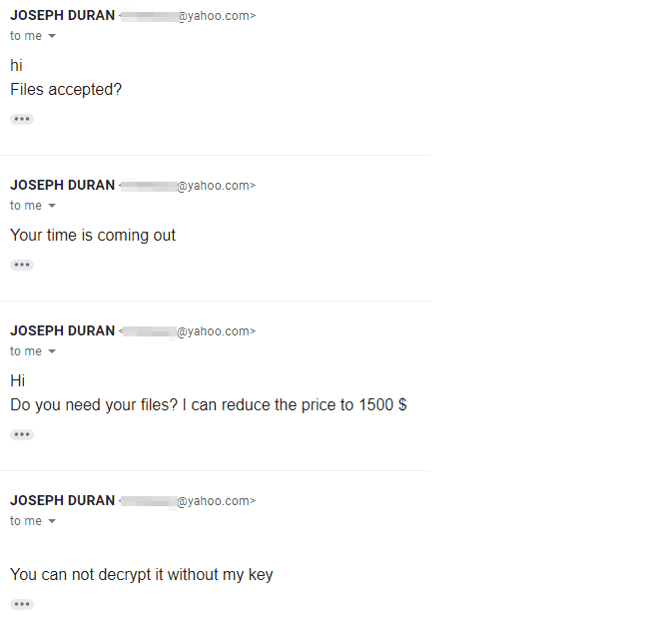
Of course, Luca wasn’t about to pay a ransom, so the crooks are left to wonder what to do with a victim who isn’t intimidated by their threats and doesn’t seem bothered about restoring their files.
What happens next shows you what any good sales person knows: if you can convince the person you’re talking to that you don’t want to buy what they’re selling, the price goes down.
What to do?
The similarities across targeted ransomware attacks gives defenders one advantage: the same diligence and precautions required to prevent an attack by one form of targeted ransomware are much the same as those required to stop any other. You can read more about those precautions in the article How to defend yourself against SamSam ransomware.
Sophos Endpoint and Intercept X can block Matrix and will detect it and its components as Troj/Matrix-*.
You can read much more about Luca’s exhaustive dissection of Matrix in her research paper Matrix: a low-key targeted ransomware.

Mahhn
Wow Luca, I think you know more about the Matrix than those that use it. Great paper.
Side mention: When all else fails – Backups are the best defense for all issues. Clonezilla, keep a cloned drive, anything breaks – swap the drive, back up as fast as a system boots. But if you don’t have it before you need it,,,,.
Peter Mackenzie
Offline and offsite backups are of course an essential part of disaster/ransomware recovery. However you also have to consider what you aren’t backing up. Targeted ransomware attacks aren’t just about data and being able to restore it from a backup. Applications and their configuration files are targeted as well – often, victims will find that, even when they have backups of their data, they additionally need to rebuild all their computers as the only application they can open is IE (in order to pay the ransom). The time it takes to rebuild 10, 100, all… your machines should be a consideration when putting a disaster recover plan together.