Researchers at Palo Alto Networks discovered 132 Android apps on Google Play tainted with hidden IFrames linking to malicious domains in their local HTML pages. Interestingly, the malware is Windows-based.
The researchers believe developers have been inadvertently grabbing the same sinister code, saying in their report:
Our investigation indicates that the developers of these infected apps are not to blame, but are more likely victims themselves. We believe it is most likely that the app developers’ development platforms were infected with malware that searches for HTML pages and injects malicious content at the end of the HTML pages it finds. If this is this case, this is another situation where mobile malware originated from infected development platforms without developers’ awareness.
But researchers from SophosLabs believe there’s more to the story.
Rowland Yu, a SophosLabs researcher specializing in Android malware, reviewed Palo Alto’s report and confirmed the lab has seen and reported the same malware to Google. Rather than being a case of many innocent developers scooping from the same poisoned well, Yu believes this is the work of one developer in particular.
More developers may be involved, but all roads seem to lead back to a developer who goes by the name Nandarok.
What happened, exactly?
Palo Alto said the infected apps included those used for design ideas for everything from cheesecake to gardening and coffee tables. All use Android WebView to display static HTML pages:
At the first glance, each page does nothing more than loading locally stored pictures and show hard-coded text. However, a deep analysis of the actual HTML code reveals a tiny hidden IFrame that links to well-known malicious domains. Although the linked domains were down at the time of investigation, the fact that so many apps on Google Play are infected is notable.
Also significant is that one of the infected pages attempts to download a malware-laced Windows file when the page loads. It’s a curious development, since the devices don’t run Windows and therefore won’t execute.
SophosLabs has identified the malicious iFrame payloads as Troj/Fujif-Gen – an ID first published in 2015, Yu said. On February 20, the Android samples were detected as App/Adload-H.
Sophos puts App/Adload-H in the category of Potentially Unwanted Applications (PUA): items such as adware that are not necessarily malicious but are usually considered a nuisance.
Enter Nandarok
App/Adload-H can be traced back to dozens of apps from the developer who goes by the name Nandarok. Yu said:
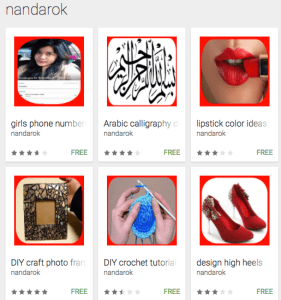
One of interesting apps is for “girls’ phone numbers”. Incredibly, between 100,000 and 500,000 users believed it and downloaded these apps.
Here is just a sample of the apps that appeared under Nandarok’s name:
Yu agreed with Palo Alto that the samples are very small and have no real function. But he disagrees with this statement from its researchers:
Our investigation indicates that the developers of these infected apps are not to blame, but are more likely victims themselves.
It’s true that others have probably spread it without realizing it. But this started as a deliberate action on the part of Nandarok and a few fellow developers. Yu said:
I believe the malware samples are from a same developer, or from a few developers who have a relationship with him. They intentionally release a bulk of junk samples. They use a framework to generate these samples, and that framework is accidentally loaded with the infected IFrame along the way.
The good news is that Google does appear to be eliminating these apps as they are reported. The key now is for researchers to keep scouring Google Play to ensure that if these or new variations surface, they can be dealt with.

Laurence Marks
“The good news is that Google does appear to be eliminating these apps as they are reported.”
I don’t think so. There are currently (2017-03-08 2002Z) 83 apps by Nandarok in the Android Google Play Store. Incidentally, all the ones I sampled had the same developer name (edited to remove email address)
Normally I wouldn’t post an address like this, but it’s so readily found by searching for nandarok that it’s not really doxing anyone.