Articles about ransomware often don’t make terribly happy reading, especially if you’ve gone looking for the article because you’re looking at a “pay page”.
That’s the message you see from most ransomware after it has scrambled your data, when the crooks make absolutely sure you know how to go about buying your data back.
Occasionally, the malware attacks everything.
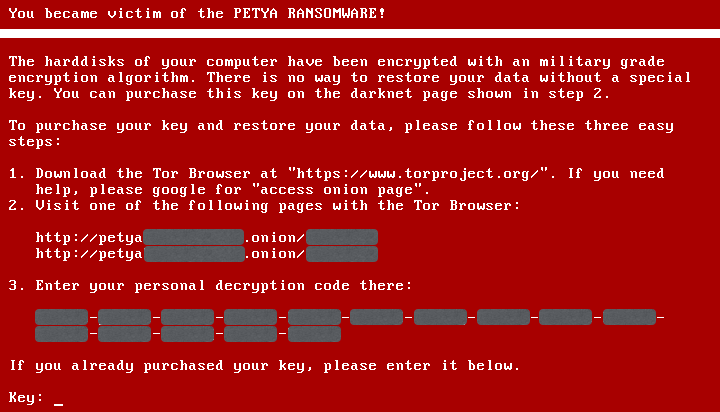
That happened with ransomware called Petya that scrambled the low-level index of your C: drive so you couldn’t boot at all, let alone use a browser, or copy-and-paste text, or even take a screenshot.
You had to find another computer to get online, and manually type in a long, alphanumeric personal decryption code that Petya displayed:
But most ransomware is much more commercially savvy than that, and goes to great lengths to ensure that your operating system and all your applications are left well alone.
That leaves you free to get online, follow instructions, and send money to the criminals.
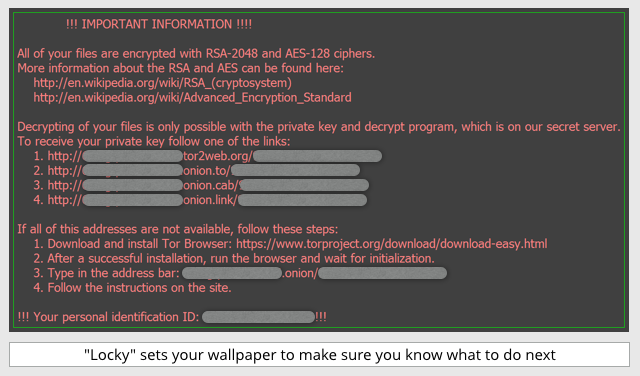
To leave you in no doubt what to do next, some ransomware even changes your wallpaper so that the how-to-pay details are permanently in your face:
So we were surprised and delighted in equal measure to read that fellow security researchers over at ESET had reached out to the crooks behind TeslaCrypt…
…asked them for the private key used in the operation…
…and received the reply, “Project closed, master key for decrypt XXX…XXX, […] we are sorry.”
We weren’t inclined to believe that the crooks really were sorry, but it seems that the master key was genuine.
Most ransomware uses what’s called a hybrid cryptosystem, in which files are scrambled with a regular symmetric encryption algorithm such as AES, which is fast and straightforward.
Each computer, or more commonly each file, uses a unique, randomly chosen key that is never saved on disk, so it can’t be recovered directly.
Instead, the file encyption key is then itself encrypted using a public key for which only the crooks have the corresponding private key.
(Public-private encryption, known as public key cryptography, relies on two related keys: one that locks data, and an other that unlocks it. You can’t use mathematics to figure out the private key from the public key because they have to be generated as a pair. In other words, the public key means that other people can scramble data that only you can decrypt.)
Usually, the crooks never part with the private key – they just use it to decrypt the unique AES key or keys needed to unlock your computer.
Because your key is unique, it only works on your files, so you can’t use it to help out other victims.
In other words, the announcement by the Teslacrypt gang that they’ve revealed their business secret is unusual.
Indeed, various public tools have already been created to use the Teslacrypt master key to unscramble locked files for free.
Result!
Of course, only victims who have been hit recently and haven’t yet paid up, or victims who backed up their already-encrypted data just in case, will get much use out of the master key at this stage.
Why did the crooks do it?
That really is the $64,000 question, and we shall probably only ever be able to guess at the answer.
We can think of the following possibilities:
- The crooks are genuinely sorry, and have retired in a fit of conscience.
- The crooks were hacked by another gang, who spilled the master key to ruin their rivals’ business.
- The crooks have switched their time and effort to newer ransomware.
- The crooks have made so much money that they want to retire in a media-friendly way before they get caught.
What do you think?
ejhonda
I think your last 2 theories are the most likely.
Bryan
they want to retire in a media-friendly way before they get caught.
That was my first thought. I want to believe the “change of heart” theory, but it’s tough to imagine anything other than “quit while you’re ahead” retiring; not many greedy people exhibit having the I-Should-Stop-Now gene. Even switching tactics/software sounds unlikely as they’d still want the revenue “earned” through their old job.
It’s possible they had rivals ^H^H^H conquerors. But I expect the key would only remain online briefly until they recovered–unless they threw in the towel figuring the key would be prolifically duplicated like deCSS and it’s severely compromised from their perspective…I find myself leaning more toward this. We may soon see Telsa-2 or a completely renamed replacement which may or may not hearken to its predecessor.
two hundred twenty
four; and last (of course not least)
the humble zero.”
Guest
Fifth possibility: They suspect or know authorities are onto them, their details have been leaked or something similar, and they want to lessen any punishment or risk of being caught. If they’re no longer operational, they think they might be left alone.
Paul Ducklin
Good point, though you could argue that’s a special case of #4 :-)
Bryan
Maybe #1 is the real answer, and the entire thing wraps up like early South Park episodes:
“you see, I learned something today…”
Greenaum
Might be worth putting a copy of the master key up somewhere it’s likely to persist longer than a TOR site run by extorting dicks who’ve retired. Perhaps a computer security company with a web server could help out by putting it on their site. Rather than XXX-XXXXX. The key itself can’t harm.
Paul Ducklin
There’s no real risk of the master key, as revealed by the crooks and published by ESET, now being lost because it’s available all over the place. But you make a fair point that publishing it one more time won’t hurt :-)
440A 241D D80F CC56
64E8 6198 9DB7 16E0
8CE6 27D8 D40C 7EA3
60AE 855C 727A 49EE
Cliff
“The crooks were hacked by another gang, who spilled the master key to ruin their rivals’ business.” Spy vs. spy? Rival organized crime syndicates? White hat vs. black hat?
Contrite? That’s an interesting idea.
Retired as wealthy hackers in their mid 20’s?
Number three sounds possible.
But “They suspect or know authorities are onto them,” sounds more like the typical criminal.
0laf
Insider threat?
Maybe TeslaCrypt has disgruntled employees as well and one of them has dumped the key on his/her way out the building?
As malware gangs get larger and more professional they’re going to pick up the problems that normal businesses have as well.
Bryan
I may be basing too much on my current employer, but I move we substitute “normal” with “traditional” please.
Mike
I’m going to bet that someone told their mothers.
Mahhn
The 7 people from the NSA that were running this while on vacation were arguing about future profits while others wanted out, so one of them gave out the key to end the discussion. Of course that’s just how the movie starts, it always ends in a mess.
Ben
First article I’ve on the subject that really explained how a single masterkey allows everyone to get their files back. Thanks!
Anonymous
or there’s a second payload and they need the computers back up to activate it.
Rani Kheir
I would think it’s #4 as well. The others seem possible as well, but #1 seems unlikely unless some incident happened to them.
Besides if they wanted to restart the project again later on, they probably can do so easily.
Xavier
Help! My computer has been attacked by the ransomware Ultra Crypter 3, all my important files have been encrypted and I have tried all solutions that I can find on the internet so far with no luck. Can anyone please give me some advice on what I can do to remove or report this virus?