
We’ve written several reports over the past year about a malware toolkit that uses Microsoft Word as its delivery vehicle.
The idea is to package malware inside a Word document in such a way that the file looks innocent, with no macros (Word program code), no embedded programs, or other content that might make a well-informed user think, “I’m not clicking on that.”
Instead, the file is booby-trapped in one or more ways so that if you haven’t patched Word recently, the internal layout of the file trips up the Word application.
This triggers a bug, known as a vulnerability, and causes Word to crash.
The infection kit, known as Microsoft Word Intruder (MWI), tries to rig up those crashes so that MWI itself takes control over from Word during the crash, thus exploiting the vulnerability to install malware.
Some users who might be reluctant to click on risky-looking web links, or to download unknown applications, nevertheless feel safe opening documents in email.
After all, documents are supposed to be data, and data ought to be safe.
The business model
The idea is that crooks with malware that they want to distribute pay a modest fee to Objekt, the nickname of the criminal behind MWI.
Objekt’s revenue stream comes from packaging and spreading other people’s malware, not from the malware itself.
He has “officially” announced that he’s not interested in huge malware campaigns with massive infection targets, preferring to live a quieter life on the fringes:
Objekt seems to offer a boutique service that he hopes will draw less attention to itself, and thus deliver returns for longer.
→ Remember when the news broke about the Internet Worm, or Code Red, or Blaster, or Stuxnet, or Heartbleed? Once malware incidents get masive coverage in mainstream media, there is usually an “all hands on deck” response. The big-ticket malware gets wiped out quickly, which can have the paradoxical effect of leaving less well-known malware unnoticed in the shadows.
So, it is interesting to look at some of the malware campaigns that have chosen MWI as their delivery system.
The Pony Express
Here’s one set of malware campaigns, Operation Pony Express, which ran in April and May 2015.
Pony Express used spear-phishing email campaigns in which booby-trapped RTF (Rich Text Format) documents were send out to prospective victims.
Spear-phishing, also known as a “targeted attack”, means sending out spoofed, infected emails that ring some sort of bell with the recipient.
In this case, one of the bells was RingCentral, a perfectly legitimate cloud-based communications company that offers internet telephony services:
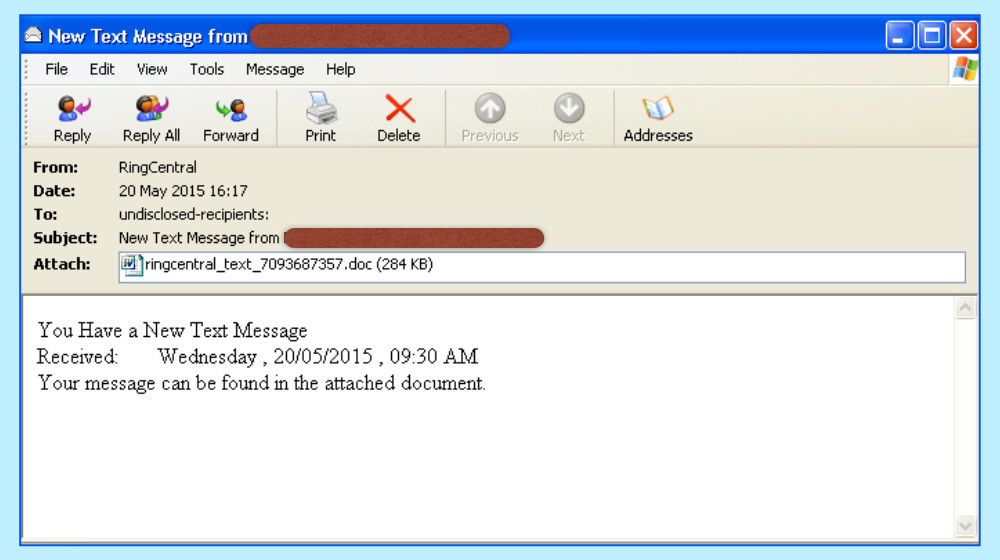
The typical campaigns in this operation targeted only a few hundred victims, with varying success rates.
As far as we can tell, about 30% of users who opened the booby-trapped files ended up infected.
We found a number of documents relating to this attack, with names such as:
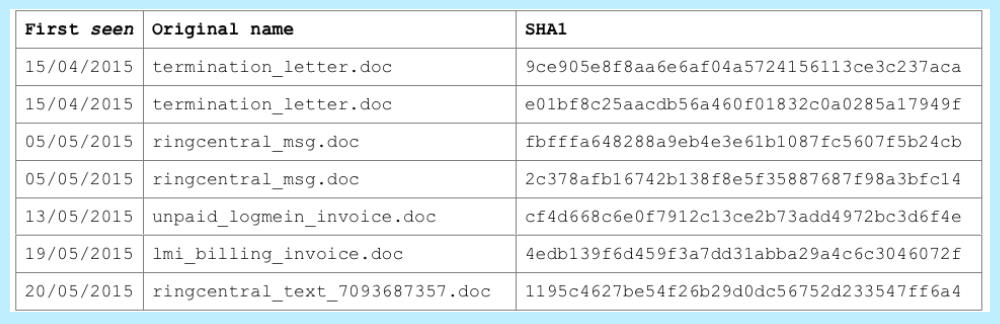
As the names suggest, the cybercriminals used the well-known subterfuge of fake invoices as well as the RingCentral theme.
The MWI documents used in this operation were all downloaders.
Rather than have the final malware payload packaged inside the booby-trapped document (what’s known as a dropper), the Pony Express campaign worked by “calling home” to servers where malware was stored for distribution.
The installed payloads came from the malware families Fareit, Rovnix, Wauchos and Dyzap.
Tracking the campaigns
The MWI toolkit includes a component called MWISTAT, which we have described before, allowing the crooks (and sometimes the good guys!) to keep track of infected computers.
Operation Pony Express was one of the few cases where we saw the criminals transferring their ongoing campaigns from one MWISTAT server to another, which led to some interesting observations.
During the operation the following servers were used:

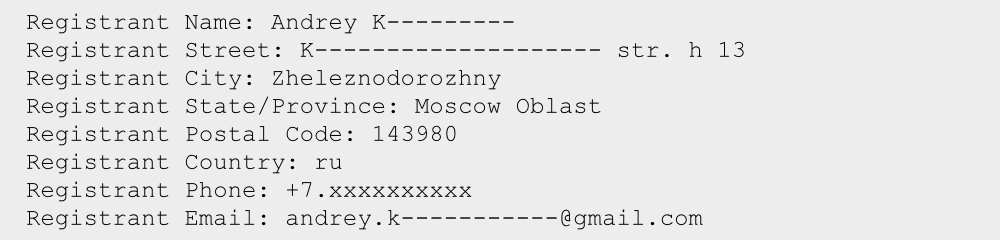
All domains had the same registration info:
Once an MWI document had completed its malware delivery task, the final malware typically connected somewhere else, as we saw with the Fareit, Rovnix, Wauchos and Dyzap Trojans identifed above.
Those Trojans used a different list of command-and-control (C&C) servers:

Those domains were either registered with exactly the same data as the MWISTAT servers, or by someone going by:
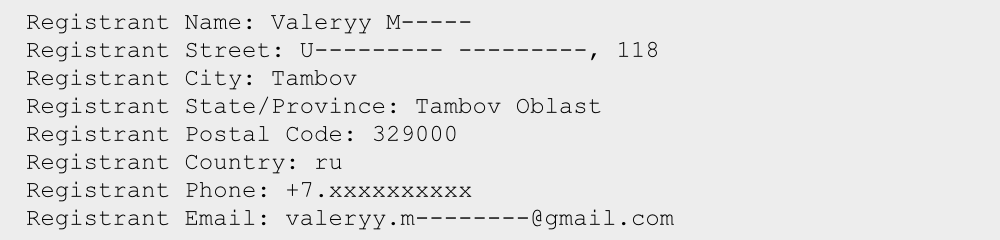
Of course, this doesn’t mean that the crooks behind the operation really are called Andrey and Valeryy, or even that they are based in Russia.
Indeed, the two servers above that are identified by IP number rather than by name have different locations:

Interestingly, the two email addresses above were used to register a raft of other domains, including:
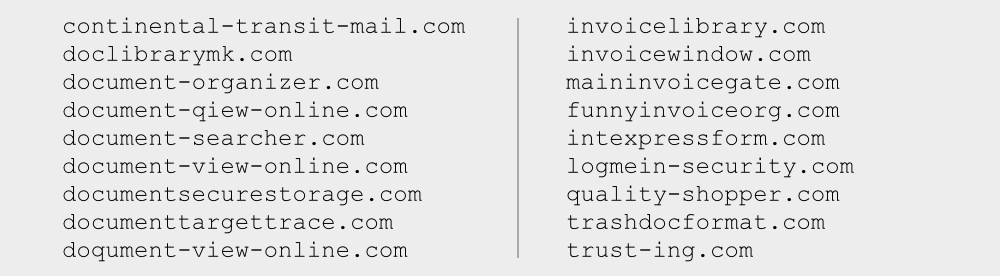
The document and invoice theme is obvious.
Operation Pony Express was predominantly aimed at the USA, as you might expect given the the use of RingCentral (a US company) as a camouflage.
About half of the computers that ended up infected were in America, with UK, Canada, China and France next down the list:
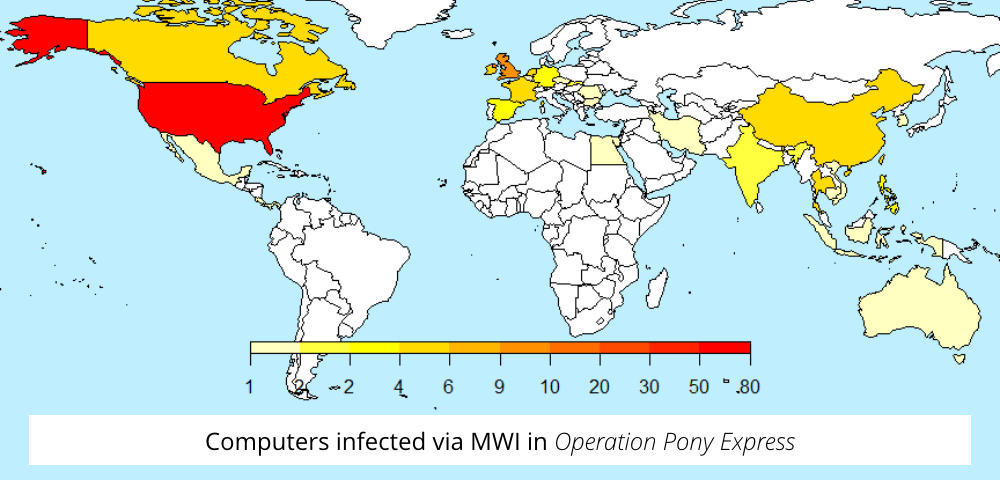
Nevertheless, as you can see, there were victims in dozens of other countries, too, so even when cybercriminals have a particular interest in one country, that doesn’t mean the rest of us can relax.
In summary
It is reasonable to assume that MWI was only one way that these criminals tried to distribute their malware – mostly Trojans aimed at stealing banking information.
But their modestly-sized MWI campaigns were nevertheless successful, with up to 30% of victims who were persuaded to open the attachments ended up infected.
Let that be a warning: as we have explained in previous articles, MWI relies on Word vulnerabilities that were patched well over a year ago.
A patched system wouldn’t have the bugs needed for MWI to work, thus blocking the exploit before it even started.
Don’t be one of the 30%…patch early, patch often!




Anonymous
Thanks, updated our blocked list since it hasn’t added these itself yet.
Paul Ducklin
If you used a Sophos product you’d be sorted automatically. That’s not a sales pitch, or anything :-)
Actually, for home use, our UTM is 100% free, including web filtering.
Anonymous
Paul, I have yet to set up my home UTM, but will get to it eventually (I plan on add blocking with it too). I have reviewed it and recommended it to friends though, particularly for their small businesses as it has better ROI for small companies while other products have a large initial investment. At work we have another product, under contract, so maybe in another couple years. While I’m chatting here – I really enjoy the site, comments and the recordings. To much tech news these days is so dry I can’t stand it, much more life here. I try to read here every day, and usually comment at least once a day (almost 2 years now). I have to post anonymously due to world press login blocked (my fault, but policy) but glad I get to. Might catch up to you at a security event one day and say hi.
Thanks for the entertaining reporting.
Paul Ducklin
You don’t have to log in to post unanonymously, if you’d prefer to use a name/handle/moniker.
If you _are_ logged in, WordPress uses your login name, but if you aren’t logged in, the comment system just asks you for “Name.” If you leave it blank, it uses “Anonymous.”
Mahhn
Cool
(Mahhn: internet nic last couple years)
Anonymous
really? docs as images? let me just type it all out manually since that won’t take me all day…
Paul Ducklin
Yes, really.
Firstly, why do you need to “type it all out manually”? Secondly, it won’t take you all day, it’ll take you a few minutes. Thirdly, the last thing we want is people’s web filters throwing a wobbly because of the URLs in cleartext in the article causing them a false alarm (and the possible ire of IT).
In short…we’re hoping you’ll be willing to take one, a very, very, small one, for the team :-)