 The iCloud brand unites Apple’s well-known online services such as iTunes, iBooks, and the App Store.
The iCloud brand unites Apple’s well-known online services such as iTunes, iBooks, and the App Store.
So it’s understandably popular – not just with Mac owners, but with Windows users…
…and, sadly, with cybercrooks, too.
Indeed, we’ve written about iTunes phishing on various occasions before, most recently just after Christmas 2014.
Apple Store and iTunes payment cards make ideal last-minute gifts, hanging temptingly as they do alongside so many supermarket checkout lines.
So it wasn’t surprising to see the crooks get up their odious enthusiasm for Apple’s brand at the back-end of the recent holiday season.
Here’s another Apple-abusing phish deconstructed, just to help you keep your guard up.
You can use this as an example to show to those amongst your friends and family who are still inclined to click through to bogus warnings.
Better safe than sorry?
It’s easy to justify checking out spams and scams, on the “better safe than sorry” principle.
That’s the same motivation that leads people who don’t themselves believe an internet hoax to pass it on anyway.
“It’s probably false,” they think, “in which case the recipient can ignore it, but if it isn’t, and they find out I knew about it, they’ll want to know why I didn’t at least mention it.”
Don’t do it!
With every click that the crooks can convince you to take, they’re one click closer to conning you.
The bogus order
This time, the crooks have put a slight twist on the usual “bogus order” scam.
Instead of simply telling you about a payment you’re supposed to have made, and leaving it to you to steam in and challenge the transaction, they’re pitching themselves as a bit more on-the-ball this time:
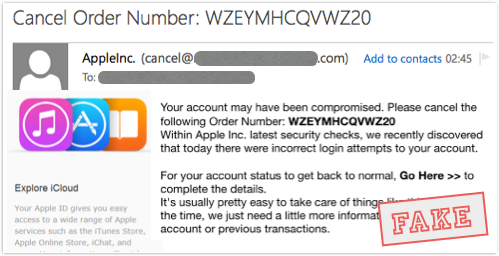
Your account may have been compromised. Please cancel the following Order Number: WZEYMHCQVWZ20
Within Apple Inc. latest security checks, we recently discovered that today there were incorrect login attempts to your account.
For your account status to get back to normal, Go Here >> to complete the details.
It's usually pretty easy to take care of things like this. Most of the time, we just need a little more information about your Apple account or previous transactions.
An order has shown up on your account, but because it coincides with some suspicious login attempts, it’s been cancelled.
In fact, it hasn’t actually been cancelled, but it will be if you would be so kind as to repudiate it:
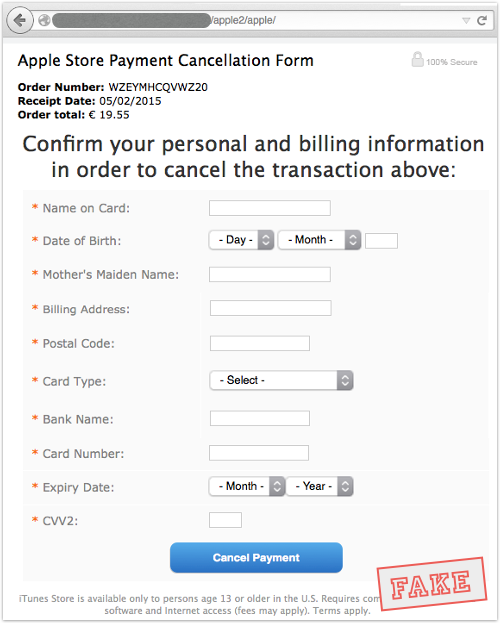
The obvious mistakes
The bogosity of the fake form above should be obvious, because it:
- Asks for far too much data, considering the process you are initiating.
- Isn’t on a typical Apple-named website.
- Isn’t using HTTPS (secure HTTP).
- Contains un-Apple-like inconsistencies, such as saying “available only…in the US” yet giving a price in Euros.
If you do fill in the form, of course, your data doesn’t go anywhere near Cupertino.
The bogus payment cancellation form is hosted on what looks like a hacked home-user DSL connection in Canada.
The form data submission goes to a similar “server” hosted on a connection via a boutique ISP in Switzerland.
What to do?
We’ll repeat what we said last time we wrote about this sort of thing:
- Think before you click. Dodgy emails often sound believable at first, either because the crooks know enough about you to refer to something you are interested in, or because they got lucky and mentioned something you are familiar with.
- Don’t assume that crooks aren’t interested in you. You may have the smallest, simplest web server in the world, but if there’s a security hole, the crooks can use your server, and your URLs, as a staging post for their cybercrimes.
- Use two-factor authentication (2FA) if you can. 2FA relies on one-time login codes, so the crooks can’t simply phish your password and use it over and over.
Learn more
• Anatomy of an iTunes phish: More tips to avoid getting caught out.
• Read why 2FA works: The power of two.
• Read how to use 2FA: Understanding the options.
• Listen to our Sophos Techknow podcast: Two-factor Authentication.
FREE NETWORK PROTECTION AT HOME
Would you like to run Sophos’s network security product at home?
Protect your family from internet threats including spam and scam emails, phishing websites, malware and more.
You can download the fully-functional Sophos UTM Home Edition 100% free.
(UTM Home is simply our regular UTM product, with all features enabled, including email and web filtering, under a home-use-only licence.)
