 Unlike Microsoft, which wants to wean us all off the word “Patch” and onto the word “Update,” Oracle has always embraced both those terms.
Unlike Microsoft, which wants to wean us all off the word “Patch” and onto the word “Update,” Oracle has always embraced both those terms.
Even the word “Critical,” which Microsoft adopts only for the most serious and exploitable vulnerabilities in each month’s updates, is OK in Redwood Shores, home of the database giant.
Indeed, Oracle goes for a triple play, calling its regular scheduled fixes Critical Patch Updates, or CPUs. (Not to be confused with Central Processing Units.)
Oracle CPUS only come out once a quarter, however, instead of the monthly cycle you’re used to with Microsoft and Adobe, so they’re a bit like buses.
You don’t see one for ages, and then 48 come along at once.
That’s how many different products in the Oracle stable made it onto this quarter’s CPU list, released on Tuesday 20 January 2015.
Many of those patches affect multiple different supported versions (for example, 10 in the case of Oracle E-Business Suite), resulting in a daunting list:
By my count, the patches fix a total of 160 known vulnerabilities, of which 93 (58%), in Oracle’s words:
...may be remotely exploitable without authentication, i.e., may be exploited over a network without the need for a username and password.
Java on the list
As usual, Java, probably the most widely-deployed Oracle product, is amongst the applications that needs updating.
The Java fixes include patches for 14 remotely exploitable holes, out of 19 vulnerabilities in total.
Java, of course, can run natively on your computer in the form of full-blown applications that you need to download and install yourself.
Java can also run as a plugin inside your browser, where the Java runtime environment (JRE) is exposed to small-scale programs called applets that are downloaded on demand from remote websites.
These pose by far the greatest risk, because applets are pushed onto your computer from untrusted outsiders.
In fact, Oracle’s default configuration turns Java off inside your browser.
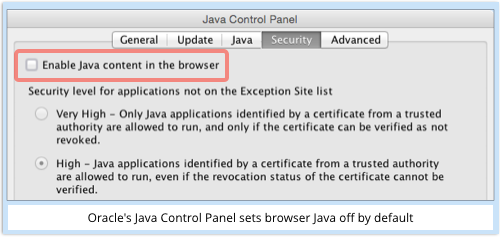
We recommend you leave things that way.
If you really need Java for specific websites, browsers like Firefox and Safari allow you to set the Java plugin into “Ask to activate” mode, where Java applets won’t run without prompting:
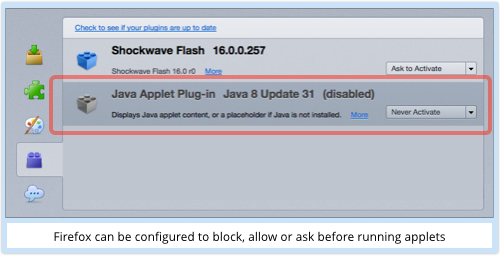
That makes it easy to work out which sites actually require Java.
Safari even allows you to enable the plugin for those sites only:
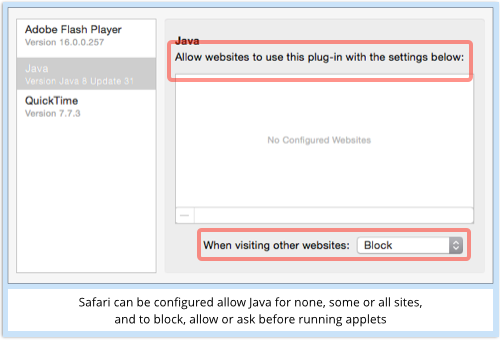
That way, dodgy websites that include Java exploits – rogue applets that try to trick or crash your browser into violating security – simply won’t get anywhere.
The bottom line
As always, Oracle’s patches aren’t really optional.
As the company readily admits:
...due to the threat posed by a successful attack, Oracle strongly recommends that customers apply Critical Patch Update fixes as soon as possible.
We agree.
Learn more about Java
If you would like to know more about Java, the risks it brings, and how to minimise them, why not listen to our Sophos Techknow podcast All About Java?
(Audio player above not working? Download, or listen on Soundcloud.)

