We monitor a range of email addresses related to Naked Security, so we receieve a regular (a word we are using here to mean “unrelenting”) supply of real-world spams and scams.
Some of our email addresses are obviously directly associated with various Sophos-related social media accounts; others are more general business-oriented addresses; and some are just regular, consumer-style emails.
As a result, we like to think that our personal scam supply is a reliably representative sample of what the crooks are up to…
…and, as you’ve probably noticed yourself, even though we see all the “old favourites” pretty much all the time, we often see bursts of one specific scam topping our personal prevalence charts.
At one point, sextortion scams were in the #1 spot (that odious sort of message turned into a real deluge in 2019 and 2020).
Then home delivery and parcel scams went wild for a while; then we had a flurry of Docusign ripoffs.
Right now, however, our scam feed is awash with a variety of frauds targeting Instagram, Instagram, and Instagram.
Instagram scams of many sorts
In the past few days, we’ve had a bogus Instagram warnings, complete with Instagram branding, in each of these categories:
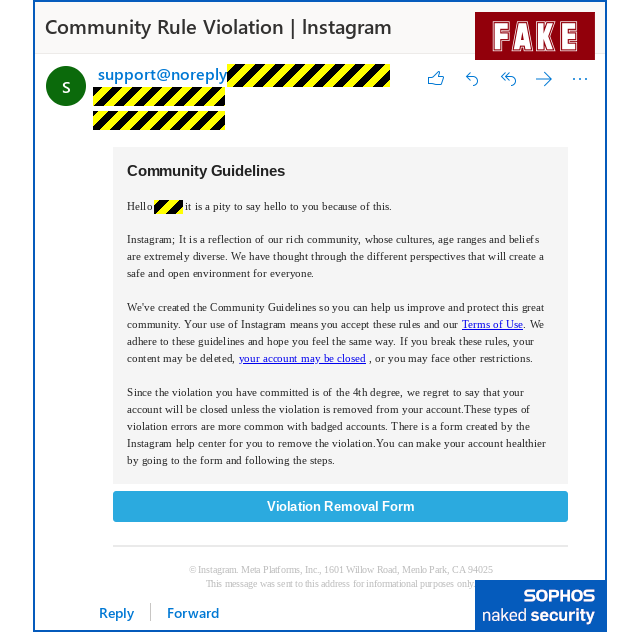
- Fake warning: Community guidelines violation. Proposed solution: Contact us to find the content that needs to be removed to clear the block.
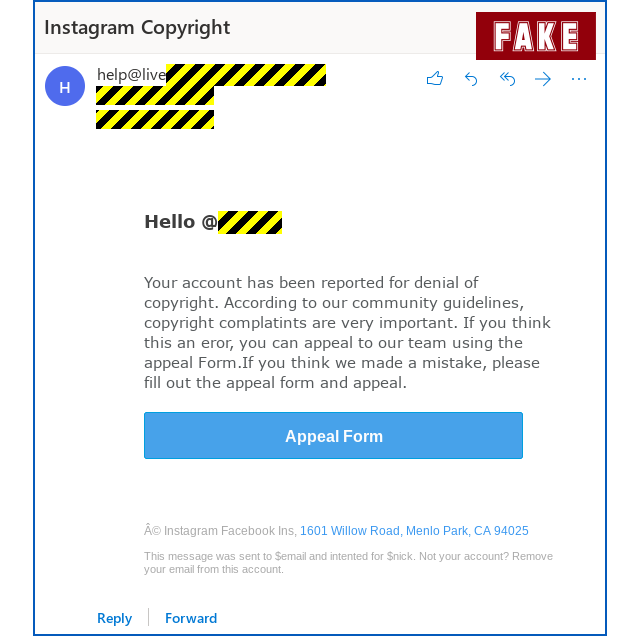
- Fake warning: Copyright infringement. Proposed solution: Dispute the claim and cancel the strike against you by filling in the form.
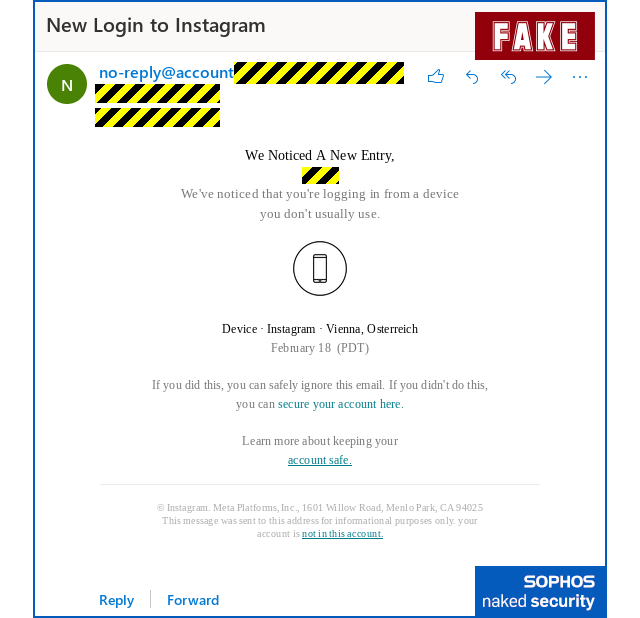
- Fake warning: Suspicious login alert. Proposed solution: If this wasn’t you, click through now to secure your account.
Although most of the examples we’ve receivedwere old-style username-and-password phishes, one went on to request our 2FA code as well.
Even though 2FA codes are typically only valid for a few minutes, cybercriminals no longer simply collect phishing data to use later.
Many cybergangs use manual or automatic techniques that alert them as soon as victims visit their phishing sites, allowing the crooks to react in real time.
If they can trick you into handing over a 2FA code as well as your password, they will try that password-and-2FA code combination immediately, knowing that, if they’re quick enough, they’re likely to get their attempt in before the 2FA code expires.
While this is not exactly exciting or unexpected news, it’s a reminder that these scams are almost certainly still delivering results for the cybercriminals – potentially giving them instant access to established, trusted social media accounts in moments.
And although these scams usually aren’t too hard to spot…
…the crooks are getting better and better at making them easier to miss.
It’s easy to miss the warning signs and fall into the trap if you’re in a hurry, or if you’re distracted by other events (and who isn’t ATM?), or if you’re a delighful, trusting person who thinks, “Oh, there’s obviously been some mistake. Surely just the matter of a moment to sort it out, thanks to the handy and official-looking form provided.”
What to look for
Here’s what the fake warnings we’ve received have looked like; if you have friends or family whom you think might be tricked by this sort of message, please share this article with them so they know that they’re one of millions people receiving the same fraudulent messages.
It’s often easier to convince people near and dear to you if it’s someone else behind the advice you’re offering – if nothing else, it sounds less “preachy” or judgmental if someone they don’t know is saying it.
And, sometimes, pictures are worth 1000 words, so here’s what they looked like.
1. Fake “Suspicious login alert” sample:
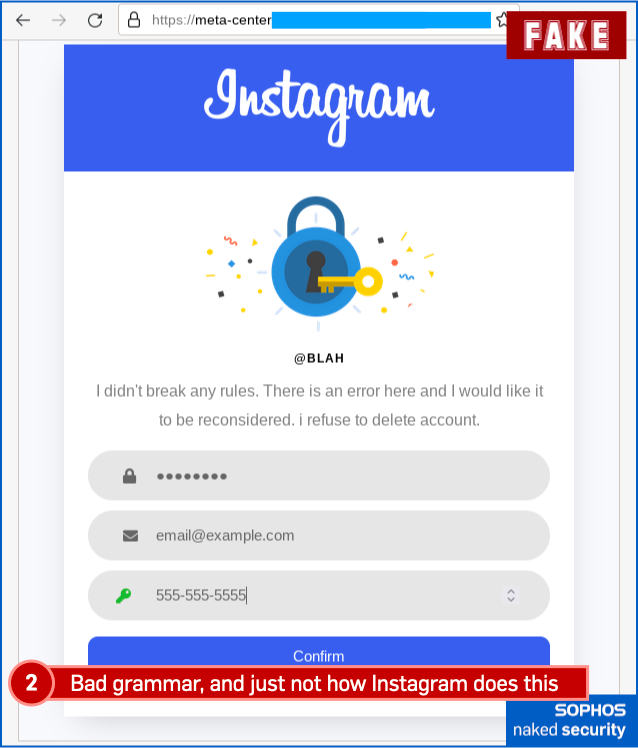
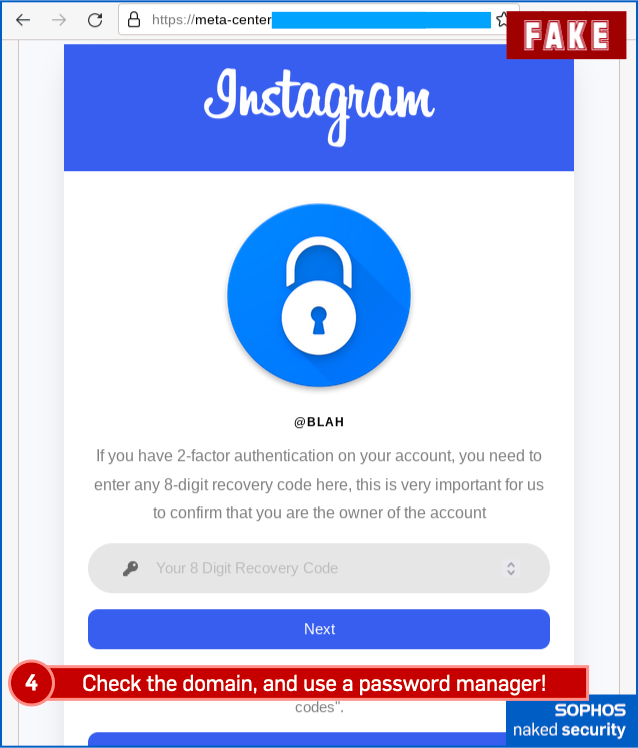
2. Fake “Community guidelines violation” sample:
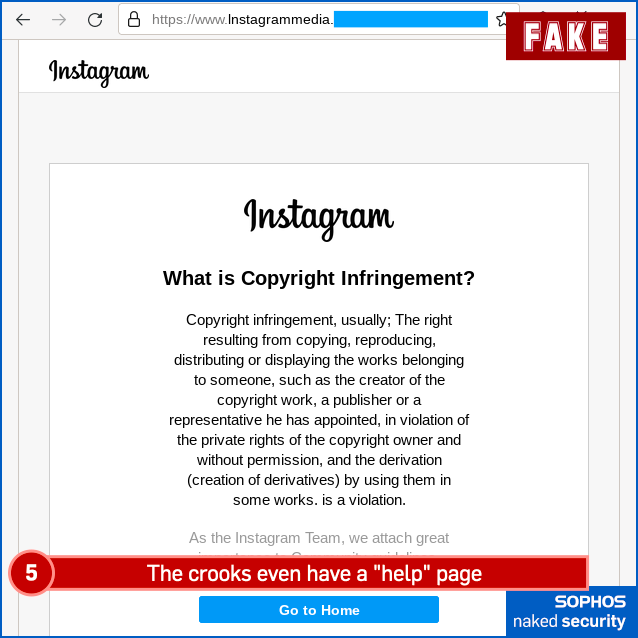
3. Fake “Copyright infringement” sample:
What happens if you click through?
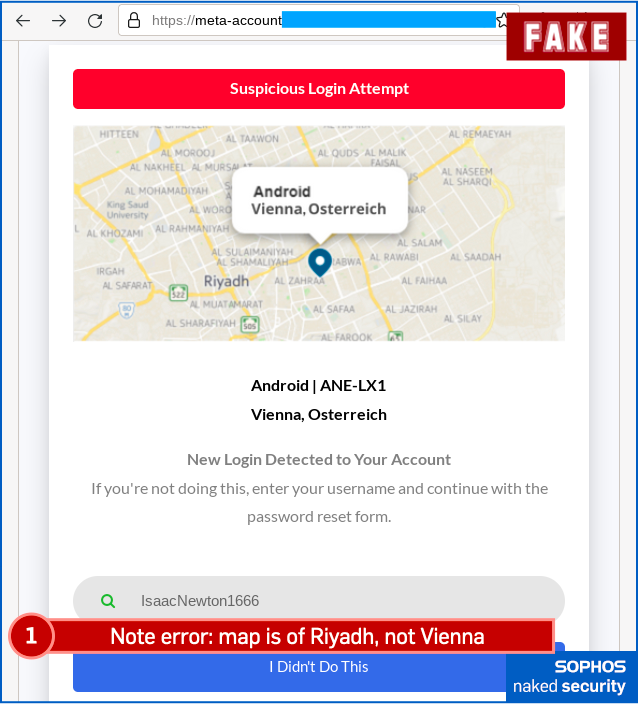
Here’s an example of the sort of follow-up pages that you’d see if you clicked through – this is the “suspicious login” sequence:
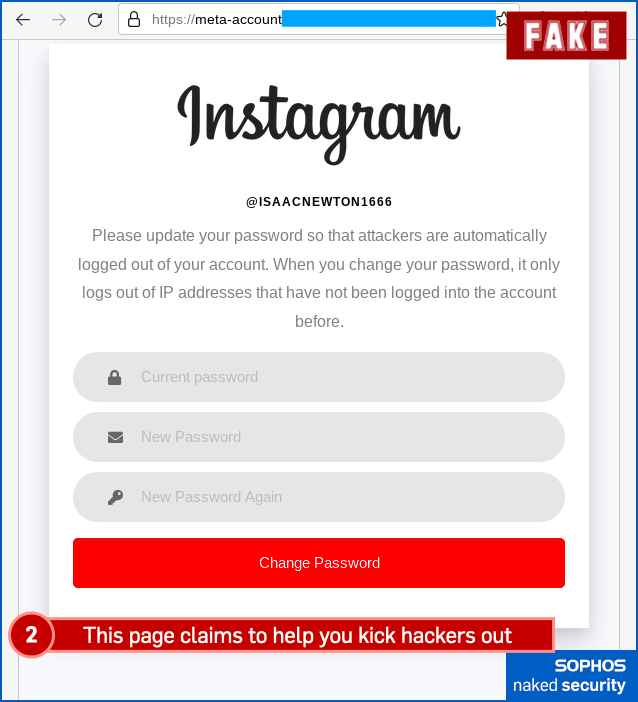

And here’s the fake “copyright appeal” – take note of the website name in these images, where what is looks like an upper-case I (eye) is actually a lower-case L (ell):

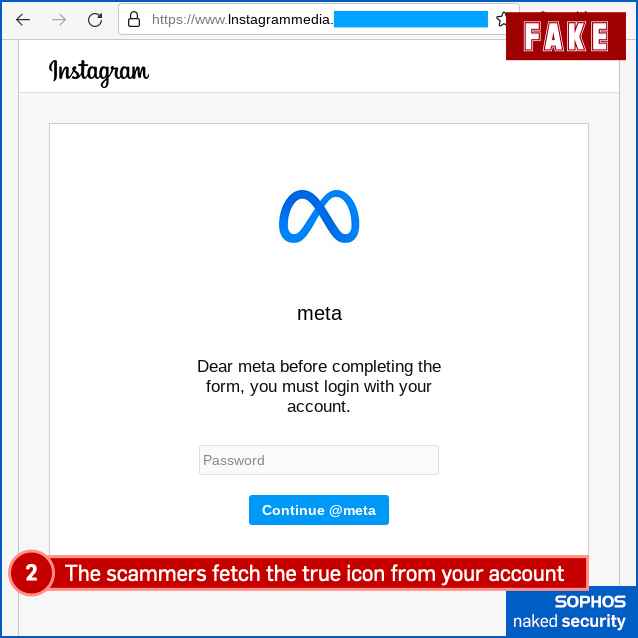
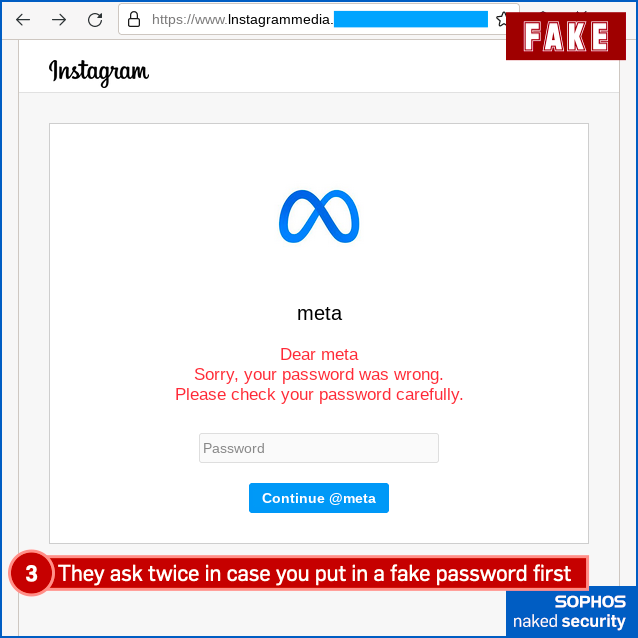
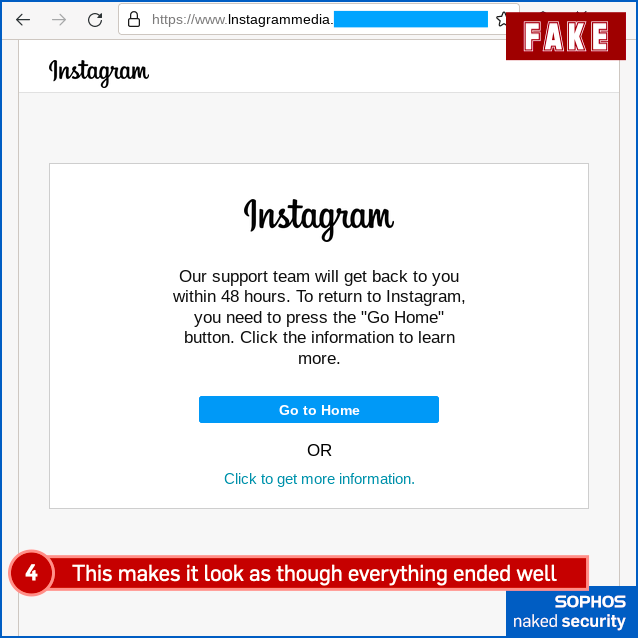
Finally, here’s the fake “community violation”, complete with a phishing page that tries to grab your 2FA code (or one of your backup codes if you don’t have your phone handy) for the crooks to try to break into your account right away, in real time:



What to do?
- Don’t click “helpful” links in emails or other messages. Learn in advance how to handle Instagram complaints or security warnings, so you know the procedure before you need to follow it. Do the same for the other social networks and content delivery sites you use. If you already know the right URL to use, you never need to rely on any links in any emails, whether those emails are real or fake.
- Think before you click. The emails above are only vaguely likely, so we hope you wouldn’t believe them in the first place (see point 1), but if you do click through by mistake, don’t be in a hurry to go further. The fraudulent sites above had HTTPS certificates (padlocks) and server names that included text such as “lnstagram” (note: with an L, not an I!), but they clearly weren’t hosted on the genuine Instagram site. A few seconds to stop and double-check the site details is time well spent.
- Use a password manager if you can. Password managers help to prevent you putting the right password into the wrong site, because they can’t suggest a password for a site they’ve never seen before.
- Watch our video below for additional advice. Early in 2021, we presented a Facebook Live talk looking at the history and evolution of this type of scam. If you have any friends who rely on social media to generate income, and who might be worried about getting cut off from their accounts, show them the video to protect them from tricks like these.
Watch directly on YouTube if the video won’t play here.
Click the on-screen Settings cog to speed up playback or show subtitles.

Earle Self
In addition to all else, “Österreich” is misspelled as “Osterreich.” If were going to be spelled in English without the umlaut, it should be “Oesterreich”…
Paul Ducklin
Good point.
Though I guess that because the crooks are targeting people who are anywhere but Austria (so that the logon location of Vienna will inevitably look all wrong), and because the email is in English anyway, that’s less likely to look wrong to the average Anglophone than the may of Riyadh! (It’s also odd that the country name is is German but the city name is not. That’s an unlikely mix, like seeing “London, Royaume-Uni” or “Londres, United Kingdom”.
Dave C
As has been noted from time to time, most of the errors are likely to be intentional – they are there to weed out those recipients of the spam like you and me who are aware and observant enough to recognise a scam for what it is, people who even if they make the initial click in a careless moment, are unlikely to follow through with the payoff of giving their real password. These are not the scammers targets.
Scammers only want to spend their time on the easiest “marks”: targets who barely know how to operate their computer, who are innocent, gullible, credulous, or stupid enough to click on the email link *and follow through to giving their password/codes*.
These are the people the scammers want to get on the hook, the ones with the greatest chance of being completely pwned by the fact they missed ALL THE REALLY OBVIOUS CLUES that its a scam, and also likely to have used the same passwords on every website they have a login.
This would be especially the case now that scammers have large organised teams ready to babysit a mark about to enter the 2FA code. They won’t want to waste time on people who are going to bolt at the last minute.
Paul Ducklin
I’ve heard that theory many times – that spammers’ and scammers’ errors are entirely deliberate. But I don’t believe that there is any statistically significant evidence to support that theory at all.
If anything, the fact that many, if not most, phishing crooks seem to be making more and more effort to make fewer and fewer blunders, and that they’re taking additional steps to add a veneer of verisimilitude to their websites, would seem to contradict that school of thought.
So I think its an interesting sociological suggestion (namely that these flawed messages don’t contain *mistakes* after all, because the “errors” are all done on purpose) but I am not aware of any credible research that supports it as more than just a suggestion.
My 2p.