SophosLabs has a seen a variety of Christmas-time spam campaigns that shamlessly hitch a ride on the coat-tails of climate activist Greta Thunberg.
The malware-spreading spams arrive with subject lines such as…
Please help save the planet Greta Friends help Support Greta Thunberg - Time Person of the Year 2019 Greta Thunberg the biggest demonstration Demonstration 2019
…and they urge you to join an upcoming demonstration.
The catch, however, is that the time and place of the alleged demonstration aren’t in the body of the email itself.
To find out more, you need to open a Word document that’s either linked to in the email, or attached to it:
MERRY CHRISTMAS You can spend Christmas Eve looking for gifts for children. They will tell you Thank you only that day. But the children will thank you all their lives if you come out for the biggest demonstration in protest against the inaction of the government in connection with the climate crisis. Support Greta Thunberg - Time Person of the Year 2019 I invite you. Time and address are attached in the attached file. FORWARD this letter to all colleagues, friends and relatives RIGHT NOW, until you forget! Many thanks.
As mentioned, some of the emails didn’t actually have an attached file; instead, they had a link at which you could download the file for yourself.
Fortunately, the links we’ve seen aren’t working at the moment, which means that even if you do click one of them you won’t be inviting malware onto your computer.
Unfortunately, of course, that means we can’t be sure what malware the crooks intended to foist on you, or what malware might suddenly appear at those links in the future.
Where we did receive a booby-trapped document, the process seemed to be geared towards delivering the Emotet malware onto your computer.
As you may know already, Emotet is a widespread malware family that seems to have evolved to fill a very specific cybercrime niche: delivering malware for other crooks.
As Naked Security’s Mark Stockley explained back in January 2019:
Over its five-year life [up to the end of 2018], Emotet has evolved from a Trojan that silently steals victims’ banking credentials into a highly sophisticated and widely deployed platform for distributing other kinds of malware, most notably other kinds of banking Trojan.
Emotet arrives on the back of malicious spam campaigns and serves up whatever malware pays. So far this year that’s meant TrickBot and QBot banking trojans, although it’s also been linked with BitPaymer – a strain of sophisticated ransomware that extorts six-figure payouts.
You have to imagine that the Emotet gang, who seem to have started life using malware to steal end users’ banking credentials, suddenly realised that they could make a living directly from other crooks by providing a malware distribution system…
…using their own malware – a sort of B2B content delivery network for other criminals.
What if you open it?
If you open one of these infected attachments, you will see what looks like an innocent-looking system warning, apparently from Word itself:
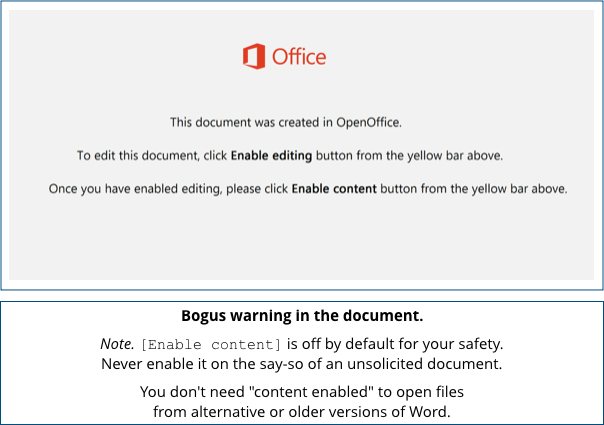
Don’t be fooled!
The “warning” is just an image inserted into the document by the crooks to trick you into bypassing Word’s default security settings of blocking active content, such as Word program macros (embedded software code), in the file.
You don’t need to use the [Enable content] button to load Word-format files created by alternative word-processing packages (or, for that matter to open documents from older versions of Word) – if the document is saved in a Word-compatible format then Word will open it; otherwise it won’t.
If you do [Enable content] then macro code inside the Word file will run a Powershell command that will go online to fetch whatever malware comes next – probably Emotet.
Remember that when malware arrives in a multi-step chain, like here, you can never be quite sure what comes next. That’s one reason the crooks like to deliver their final malware payloads via a web download that happens at the time and place that your infection started. That way they can tailor the final malware not only by time, but also by your geolocation and even by what type of computer you’ve got. For example, if your laptop turns out to be a Mac, some crooks will deliberately try to hit you with Mac-specific malware instead of sending you a Windows program that isn’t going to run at all.
What to do?
- Don’t open attachments you didn’t ask for or expect. Getting unsolicited email is bad enough – so don’t give the spammers yet more time-of-day by opening attachments to help them out even further. If this were a genuine invitation, the time and location would be in plain view in the body of the email, not hidden away in an un-needed, unwanted attachment.
- Don’t turn off security features because a document tells you to. Microsoft selected [Disable content] as the default to protect you from unscrupulous documents, including unscrupulous documents that tell you to [Enable content].
- Look for an anti-virus with behaviour-blocking and web filtering as well as plain file scanning. The multi-step approach used by malware like this means the crooks need to get away with less at each stage – the DOC file itself doesn’t need the full and final malware built right in. But that means you can stop the attack by blocking any of the stages, while the crooks have to succeed at all of them. You gain the upper hand if you have multiple layers of defence.
PS. Sophos Home is 100% free for Windows and Mac. The Premium version, with more features and cover for up to 10 computers (including friends and family), is half-price at the moment.

Magyver
My take? Anyone dumb enough to take environmental & political advice from an untrained 16 year old high school student deserves a wakeup call, lol…
They won’t do it twice! …*grins*
Magyver
Sorry Paul, I forgot to tell all you guys Merry Christmas & happy new year – spread the word, will you?
Anonymous
I’m with Magyver. Only an idiot would listen to Greta Thunberg so you get what you deserve.
Magyver
Ha ha, thanks… Happy new year!
Raffles
The kid has been given bad tutoring or advice.
Cam
Funny
Mick
I agree with the comments above. The malware campaign is clearly targeting those who are indoctrinated enough to believe her stage act, so they’re assumed to be gullible enough to click on any documents they are sent. My only comment to the attackers: “How dare you?”
Anonymous
This threat has absolutely nothing to do with Greta herself or her platform. If you want to jump on the Trump bandwagon of belittling a child, especially one you’ve never met and know next-to-nothing about, stick to Reddit. This article details a very real threat for the majority of folks who don’t know much about the technical aspects of a computer; it has nothing to do with whether a person agrees with Greta’s platform.
Move along children, the adults are here for grown-up information.
Magyver
Your premise is wrong Anon, “in our opinion”. Greta was selected for a reason, and we feel that reason was because the hacker felt her followers would flock to her side just to be a part of the growing divisiveness of her so-called platform.
Your use of the “Trump bandwagon” phrase also explains why you don’t think we have a right to express an opinion in public – I would add that the adults here have already expressed their opinion.
Anonymous
“You have been invited to a Donald Trump rally. Help make America Great again!. Click the link and download the attached word document for location and time.”