SophosLabs just published a new report on an intriguing but lesser-known part of the malware scene known as MyKings.
You probably haven’t heard of MyKings, mainly because it’s not ransomware and the gang isn’t currently slamming businesses up against the wall by demanding money, so it hasn’t made big enough waves to make the headlines.
In simple terms, MyKings is all about illicit Monero cryptomining, and at the current low price of Monero, our researchers estimate that on some days the crooks are only making about $300.
For all we know, MyKings might be little more than a sideline hobby for the people running it (albeit a hobby pulling in a quiet and untaxed $100,000 a year, of course).
Compared to the multimillion dollar extortions that some cybercrime gangs are demanding for ransomware recovery, it’s easy to write off malware like MyKings as unimportant and therefore not worth trying to learn from.
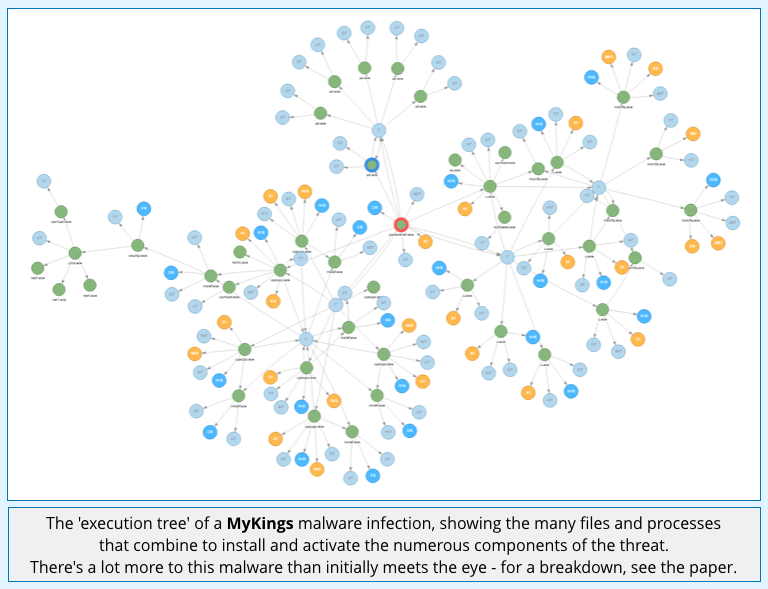
But that couldn’t be further from the truth, because the MyKings story gives a fascinating insight into a type of cybercrime that involves a huge amount of complexity, and has a surprising reach.
According to SophosLabs research, the MyKings crew:
- Currently have about 45,000 infected computers in their Monero-mining botnet, up from about 35,000 a year ago.
- Can upgrade their malware code on infected computers at will.
- Are using surprisingly sophisticated ‘rootkit’ tricks to get kernel access and to avoid detection.
- Also go after your local cryptocoin wallets.
- Employ a ‘fileless’ password stealing tool to crack passwords and spread on your network.
- Use the ETERNALBLUE exploit to spread.
- Kill off numerous security products or stop them loading at all.
- Get rid of rival cryptomining software and other programs of their choice.
- Rewrite your firewall rules to keep rival crooks out.
- Hide malware downloads inside innocent-looking images to complicate detection.
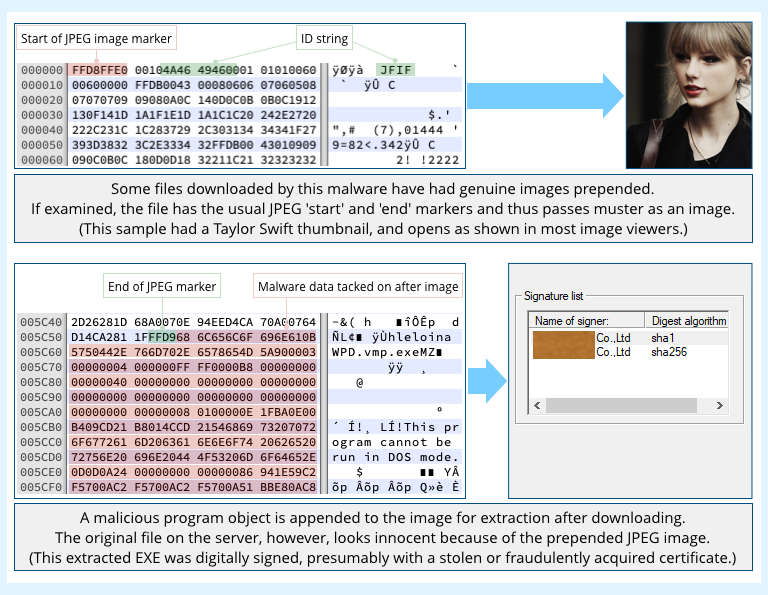
In other words, if you measure the threat of MyKings only in terms of the financial cost of its most obvious side effect, namely the electricity it steals to mine Monero…
…you’re missing a lot of vital lessons.
If the MyKings gang suddenly decided to give up on the cryptomining, for example, the flexible way in which their malware can reconfigure itself via the internet means that they could switch over to almost any other sort of malware-based cybercrime they liked.
Or they could just sell on their whole botnet, complete with auto-upgrade functionality, and who knows where your cybersecurity might go next?
Get the report
The MyKings report was produced by experienced and well-respected researcher Gabor Szappanos, also known as Szapi, whom many of our readers will already know from his previous research papers.
Szapi doesn’t just give you a detailed and informative review of how real-world multi-component malware operates and evolves.
He also tells the story in a way that helps you plan your defences well, and reminds you not to judge a malware book by its cover.
Read the paper now!


Tom
I have to admit, these computer viruses have come a long way from “AnnaKournikova.jpg.vbs”.
But the interesting thing that I question here is why doesn’t the JPG interpreter just stop once it sees the ‘End of JPEG’ marker? Could this be fixed by those software designers that create these image interpreters?
Paul Ducklin
The thing is, image editing and rendering programs generally do stop at the JPEG end marker. They’re not supposed to bother with what might come afterwards. So if you examine the image with conventional tools it looks normal – because to those tools it *is* normal and the appended EXE is ignored.
The malware downloader, however, doesn’t treat the file as a JPEG – it knows that the JPEG part is just there as a ‘cover story’, so it throws it away and uses the rest of the file instead. Thus it effectively hides the downloaded part in plain sight – and if you do ever get hold of a copy of the downloaded file yourself and wonder, “Hey, is this suspicious?”…
…then unless you look at it in detail with something like a hex editor, as I did above in the screenshot, you’re likely to dismiss it as harmless.
(To be clear, this is not an exploit or an attack that gets in initially by means of the JPEG. *You* don’t download the image or get tricked with a dodgy link – you have to be infected with the initial part of the malware already; this is just a way for it to fetch a new component in a less suspicious fashion than downloading the EXE directly. That’s the reason for this trick.)
RHartes
So it wouldn’t be blocked by a firewall, because it’s a JPEG. Where a .exe would be blocked.
Paul Ducklin
That’s the theory, assuming that the firewall hasn’t already blocked the download on the basis of where it came from or on account of the process that tried to download it, or because it deemed the JPEG suspicious or spotted the tacked-on data.
Mahhn
So the witch that is doing magic for you, is sneaking in ingredients to make a poison to use on it’s host.
Or maybe Jafar from Aladin would be a better analogy.
DudeSweet
Confirmed Taylor Swift is a virus.
Billy R. Gilbert
I’ve been surprised for awhile now how/why Steganography isn’t a more common vector than it is. I’m okay that it’s not, but still…
Semysig
This isn’t steganography. That’s when you put a few pixels in a pic that’s pattern decodes, or can be recognized by a human as something.
Paul Ducklin
I think it’s OK to call it steganography (‘hiding in plain sight’) even though the EXE is very obvious *once you know where to look*. It’s not very sophisticated steganography – as you say, that word is often associated not with hiding text after an image but cunningly sprinkled as pixels in the image itself – but IMO the word will do fine here.
For further discussion on this topic you might enjoy:
https://nakedsecurity.sophos.com/2018/11/12/how-to-fit-all-of-shakespeare-in-one-tweet-and-why-not-to-do-it/
https://nakedsecurity.sophos.com/2013/05/15/and-the-winner-of-the-world-war-two-steganography-competition-is/
Semysig
Ok, so this ISNT really a virus at all, its a ctrl mechanism for a virus you’re already infected with?
So why isnt this article telling us how to spot THAT?
That said, the implications of this ingenious (and evil) ability are important to know.
Paul Ducklin
Well, to be fair, this article is an overview of an extensive research paper that provides much more detail about the surprisingly many moving parts that constitute this virus. We’ve also published an extensive list of IoCs (“indicators of compromise”) on the SophosLabs GitHub page, our primary source for publishing malware identifiers such as checksums, URLs used and so on.
So the detail you are demanding is available – we didn’t repeat it here because it’s not of immediate interest to most of our readers. This piece is just a short summary to let you know that a full dissection is available.
If you click on the ‘execution tree’ image, for example, you will go straight to the source material (the full paper) from which that tree was drawn.
HtH.
Faz
Still.. worth adding a direct link to the indicators of compromise for those who want to check if they’ve been caught up in this tangle?
Paul Ducklin
Here is the relevant GitHub page. I recommend checking out the paper first as it helps you make sense of where the very numerous IoCs fit in…
https://github.com/sophoslabs/IoCs/blob/master/malware-MyKings