“Fragile?” “Handle with care?”
“Meh! Looks like a football to me,” workers for the UK parcel delivery company Yodel must have said around the time – 2016 – they were caught on video, apparently tossing packages around.
Have they grown more tender? Dunno, but FWIW, a year after the football exposé, they made it to the top of the country’s worst delivery companies (again).
More to the cybersecurity point, and more recently, a security researcher spotted Yodel’s mobile parcel delivery app doing something similar in the data realm – as in, tossing around random parcel data, and letting it leak into the apps of people whose doorsteps those packages weren’t supposed to show up on.
On Saturday, Akshay “Ax” Sharma, having failed to get Yodel’s attention, blogged about his discovery.
As Sharma tells it, around noon on Saturday, he noticed something weird on Yodel’s mobile app for Android. The app lets you track parcel deliveries scheduled for your address but was showing other people’s packages in addition to his own. Every time he refreshed the feed, the app loaded new tracking numbers for more random packages – packages that weren’t even destined for the same building as his own, nor that he’d ever tracked.
After Sharma tweeted about the issue, one other Twitter user said that she was seeing the same thing:
I have other people’s deliveries on my Yodel app today too! Couldn’t work out for the life of my how I had so many deliveries coming then realised they were in Dartford, Borehamwood etc when I’m in Edinburgh!
— Michelle Burgess (@chelleburgess) November 30, 2019
…and ditto for multiple users who noted the glitch in their Google Play Store reviews:
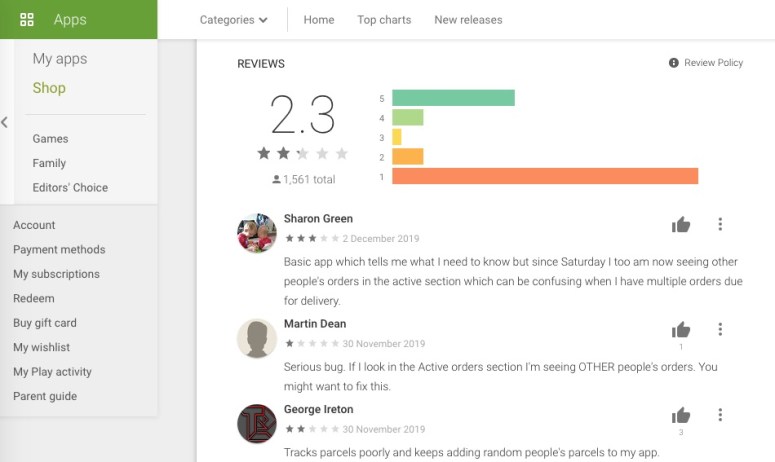
The app was last updated on 18 November, and the reports of data leakage seemed to have cropped up after that.
On Tuesday night, Yodel told The Register that the problem’s been fixed. It didn’t elaborate on what caused the leak, nor whether anybody’s packages got pinched because of it, saying only that…
Following an investigation into the issue we can confirm that it is now resolved, with the Yodel app running again as normal.
Let’s just redirect those goodies, shall we?
Sharma provided a number of screenshots showing the information the app was dribbling – about other people’s packages – before it got plugged. He said that the list included:
- Tracking numbers
- Name(s) of retailer(s) who sent the package
- Package’s current location on a map
- Delivery driver’s name
- Package destination (i.e., recipient’s location)
- Customers’ reference notes with regards to the parcel contents (say, “that insanely expensive new iThingie I’m getting my sweetie for Christmas”)
- Estimated delivery time
Besides all that, Sharma said, the app offers users the option to reschedule or cancel deliveries – in some cases, “using just the tracking number which is now revealed to a user with absolutely no connection to the package.” All of which could lead, of course, to “Hello, new iPhone that I didn’t pay for!”
Perhaps nobody’s packages got tampered with due to the bug, but they could have. Sharma blames poor mobile app design and testing:
While the potential for damage arising from a minor security bug like this one may seem negligible, the app still reveals way too much data than necessary and gives control of your precious parcels to unknown parties, should they get tempted to abuse it.
This is yet another lesson in how serious bugs and security flaws can arise from poor design and testing when coding mobile apps.
What to do?
Not a thing, given that users can’t avoid a glitch in a mobile app like this one, and it’s all now been fixed. However, given that it’s holiday season and purchases are flying through the intertubes, why not take a minute and watch our video on how to stay safe on Black Friday? Sure, that was last week, but the crooks are after us year-round. That makes our tips as fresh as pine garlands and as green as mistletoe!

Steve
The privacy aspect of this is bad enough, but on top of that, it sounds like a porch pirate’s dream-come-true!