On 18 November, somebody swapped out the legitimate command line wallet binaries for the Monero (XMR) cryptocurrency and replaced them with software that stole users’ funds.
The malicious versions of the Linux and Windows binaries were first spotted by a user on Monday who noticed that the software failed an integrity check.
Like a lot of software vendors, The Monero Project publishes SHA-256 hashes of its software. Users can check their software download by running it through a SHA-256 hashing function to see if it matches the published hash.
In this case, it didn’t.
The Monero team confirmed the swap on Tuesday, assuring users that the malicious wallet binaries were up for only a short time – 35 minutes, to be precise.
The malware-impregnated binaries were immediately dealt with, according to binaryFate – a member of the XMR core team who said on Tuesday that the binaries were now being served from a new, safe, “fallback” source.
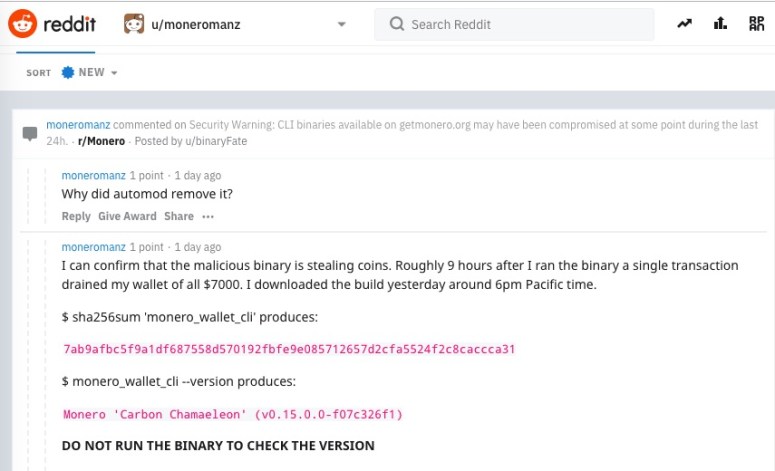
A half hour was long enough to lead to at least one wallet getting drained, however: one user claimed on Reddit that 9 hours after they ran the binary, a single transaction scooped $7,000 worth of coins out of their wallet.
Whodunnit? Howdunnit? For how much?
As of Wednesday, there were a number of unanswered questions. It wasn’t clear how the attacker(s) pulled off the compromise of the Monero site, nor how many users were affected, nor the total value of cryptocoins that were stolen. There are several people investigating the incident, Monero said.
When the security researcher BartBlaze analyzed the malicious binary, they found that it it had a few new functions not in the official software, one of which sent data – namely, stolen funds – to command and control servers. That one was immediately called after a user either opened or created a new wallet.
…and that’s about all it did, BartBlaze found:
As far I can see, it doesn’t seem to create any additional files or folders – it simply steals your seed and attempts to exfiltrate funds from your wallet.
A seed is like a passcode or phrase that gives a user access to their wallet. Anybody who gets their hands on one can vacuum out a wallet.
Check your binary hashes
As of Tuesday, binaryFate was telling Monero users who’d downloaded binaries in the previous 24 hours to check the files’ integrity – immediately.
If the hashes do not match, do NOT run what you downloaded. If you have already run them, transfer the funds out of all wallets that you opened with the (probably malicious) executables immediately, using a safe version of the Monero wallet (the one online as we speak is safe – but check the hashes).
For instructions on how to verify binaries on Linux, Mac or Windows, Monero has this how-to.