A bug in Facebook’s photo API may have exposed up to 6.8 million users’ photos to app developers, the company announced on Friday.
Facebook said that normally, when a user gives permission for an app to get at their Facebook photos, the developers are only supposed to get access to photos that are posted onto their timeline.
In this case, the bug allowed up to 1,500 apps – built by 876 developers – to access photos outside of the timeline. Specifically, photos from Marketplace or Facebook Stories were exposed. The most worrisome collection of exposed photos, however, were those that users hadn’t even posted.
It’s not that the apps were sniffing at your photo rolls, Facebook said. Rather, the API bug was letting those apps access photos that people had uploaded to the platform but hadn’t chosen to post.
They might have uploaded a photo to Facebook but hadn’t finished posting it because they lost reception, Facebook suggested.
Then again, maybe a user had second thoughts about posting a particularly sensitive, personal or intimate photo, and that’s where the fear factor kicks in: they might have had second thoughts for very good reasons, but a bug like this one makes reticence completely irrelevant.
Why is this even an issue, you might ask? One would imagine that photos that were never posted to Facebook were nothing more than a glimmer in the photographers’ eye, but no: Facebook says that it stores a copy of photos that are postus-interruptus for three days “so the person has it when they come back to the app to complete their post.”
Note the “when”: that’s marketing-positive speak that ignores the existence of “if,” as if second thoughts about posting just don’t happen in social media.
If only.
The only apps that were affected by the bug were so-called trusted ones: the apps that Facebook has approved to access the photo API and to which people had granted permission to access their photos.
You found this out WHEN?
Facebook says that its internal team discovered the bug, which may have affected people who used Facebook Login and who had granted permission to third-party apps to access their photos. It’s now fixed, but the third-party apps could have had inappropriate access to photos for nearly two weeks: specifically, the 12 days between 13 September to 25 September.
In its announcement, Facebook stayed quiet on the question of why we’re only hearing about this now. But when TechCrunch asked Facebook about what seems like an excessive notification lag, the platform said that its team discovered the breach on 25 September, went ahead and informed the European Union’s privacy watchdog (the IDPC, or Office Of The Data Protection Commissioner) on 22 November, and the IDPC then began a statutory inquiry into the breach.
Facebook must be suffering from serious apology fatigue at this point because all it managed to cough up was:
We’re sorry this happened.
Facebook told TechCrunch that it took time to investigate which apps and users were affected by the bug, and to then build and translate the warning notification it’s planning to send to those affected users.
Early this week, Facebook will release tools for app developers that will allow them to determine which people using their app might be affected by the bug. Facebook says it will be working with those developers to delete the photos that the apps should not have been able to access in the first place.
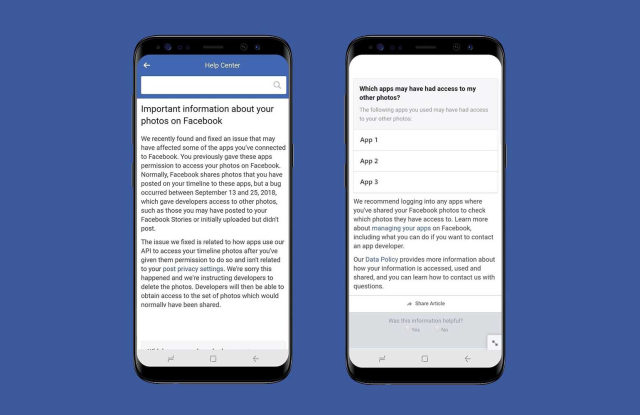
Facebook will be notifying users who’ve potentially been affected by the bug via an alert that will direct them to a Help Center link where they’ll be able to see if they’ve used any apps that were affected by the bug. It will look something like this:
What are the GDPR implications?
The delay might put Facebook at risk of stiff General Protection Data Regulation (GDPR) fines from the European Union for not promptly disclosing the issue within 72 hours. That can get painful: those fines can go up to €20 million (USD $22.68 million) or 4% of annual global revenue.
European regulators confirmed on Friday that they are, indeed, investigating Facebook for violating the GDPR, as ABC News reports.
Here’s what Graham Doyle, the Irish Data Protection Commission’s head of communications, told ABC News:
The Irish DPC has received a number of breach notifications from Facebook since the introduction of the GDPR on May 25, 2018. With reference to these data breaches, including the breach in question, we have this week commenced a statutory inquiry examining Facebook’s compliance with the relevant provisions of the GDPR.
Yet another day that will live in privacy infamy
The photo API bug was discovered on 25 September: the same day that Facebook discovered that crooks had figured out to how to exploit a bug (actually, a combination of three different bugs) so that when they logged in as user X and did View As user Y, they essentially became user Y. In other words, the crooks exploited a bug so as to recover Facebook access tokens – the keys that allow you to stay logged into Facebook so you don’t need to re-enter your password every time you use the app – for user Y, potentially giving them access to lots of data about that user.
The access token bug affected what would turn out to be an estimated 30 million Facebook users.
As far as the newly disclosed photo API bug goes, we don’t know yet which apps got at photos they weren’t supposed to access. ABC News reached out to dating apps Tinder, Grindr and Bumble, but they hadn’t responded as of Monday.
Privacy advocates expressed a combination of concern and shell-shocked shrugging at the latest in Facebook’s privacy fumbles.
ABC News quoted Christine Bannan, counsel for the Electronic Privacy Information Center (EPIC), who said that the latest incident shows just how Facebook’s lack of concern for user privacy results in incidents like this:
It’s another example of FB not taking privacy seriously enough. Facebook just wants as much data as possible and just isn’t careful with it. This is happening because they are having developers have access to their platform without having standards and safeguards to what developers have access to.
Gennie Gebhart, a researcher with Electronic Frontier Foundation (EFF), told the news outlet that as far as users are concerned, it doesn’t matter if their data gets abused by design or by flubbery. It all amounts to the same in the end:
2018 has been the year of Facebook and other tech companies violating these privacy expectations, with nothing resembling informed consent. It is important to differentiate this from Cambridge Analytica, which wasn’t a bug. That was a platform behaving as it was intended. This is a different breed of privacy violation. This was an engineering mistake in the code. Of course, on the user end, those technicalities aren’t important. This is just another huge Facebook privacy scandal.

Jack Barker
“Acute apology fatigue” —perfect!